Difference between revisions of "Kill Your Internet"
| [unchecked revision] | [checked revision] |
m (→Questions and Answers) |
|||
| (13 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
| − | Kill Your Internet was an ARG created by [[Camouflaj]], connected to their game | + | {{argbox |
| + | | float = right | ||
| + | | name = Kill Your Internet | ||
| + | | image = File:BBS_logo.png | ||
| + | | description= Kill Your Internet - an ARG that took place in the world of République. | ||
| + | | creator = [[Camouflaj]] | ||
| + | | type = Official | ||
| + | | status = Completed | ||
| + | | discovered = 03-18-2016 | ||
| + | | completed = 04-02-2016 | ||
| + | }} | ||
| + | [[Main Page]] > [[List of Investigations]] > '''Kill Your Internet''' | ||
| + | |||
| + | Kill Your Internet was an ARG created by [[Camouflaj]], connected to their game [http://store.steampowered.com/app/317100/ République]. It was focused around a retro [[Kill_Your_Internet:CypherPunk|Bulletin Board System]] and its administrator, [[Kill_Your_Internet:KatherineTheGreat|KatherineTheGreat]]. Puzzles included interacting with chatbots hosted on the BBS, solving puzzles on in-fiction sites, and playing games. The ARG concluded with an IRC chat session between the players and KatherineTheGreat, as well as KtG's artificial intelligence Shahrazad. | ||
== Prelude == | == Prelude == | ||
| Line 35: | Line 48: | ||
* 2 (Listen to System Operator Voice Support Tickets) presented a single voicemail, made by the employee Ev Donald on 1998-11-29. He is with a client but is unable to log in to the employee system (option 3 on the original menu). He then tries to access this again and the tones for his 8-digit employee number can be heard. Ev then says that the system then disconnects, and asks for a solution before hanging up. | * 2 (Listen to System Operator Voice Support Tickets) presented a single voicemail, made by the employee Ev Donald on 1998-11-29. He is with a client but is unable to log in to the employee system (option 3 on the original menu). He then tries to access this again and the tones for his 8-digit employee number can be heard. Ev then says that the system then disconnects, and asks for a solution before hanging up. | ||
| − | With the help of | + | With the help of Discord user nanoi, Ev Donald's code was successfully identified as 71469122 and was used to log in to the Technician Support Hotline option, which then informs the caller that the password for user creation is 4E6A863C. |
=== Creating an Account === | === Creating an Account === | ||
| Line 59: | Line 72: | ||
=== The Search Begins === | === The Search Begins === | ||
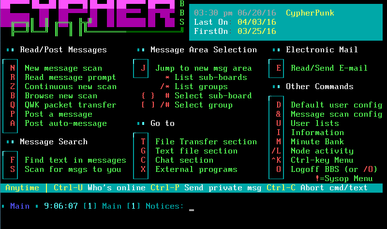
| − | [[File:BBS main.png|thumbnail|right|The main menu displayed when | + | [[File:BBS main.png|387px|thumbnail|right|The main menu displayed when logging into the BBS]] |
The BBS has many different options available, including a directory of text files and a chat bot named the Guru. Pressing 'G' on the main menu of the BBS to get to the text files that are hosted there leads to a list of 13 files. Discord user Emoticon created a [http://pastebin.com/sTtLYAZr Pastebin] documenting the contents of the 13 files. Only the 13th file is relevant to the puzzle: it encourages the reader to ask the Guru about the archives, and mentions the letters S, E, P, L, I, C, and E. Discord user nanoi figured out that "S E P L I C E" is an anagram of "ECLIPSE". | The BBS has many different options available, including a directory of text files and a chat bot named the Guru. Pressing 'G' on the main menu of the BBS to get to the text files that are hosted there leads to a list of 13 files. Discord user Emoticon created a [http://pastebin.com/sTtLYAZr Pastebin] documenting the contents of the 13 files. Only the 13th file is relevant to the puzzle: it encourages the reader to ask the Guru about the archives, and mentions the letters S, E, P, L, I, C, and E. Discord user nanoi figured out that "S E P L I C E" is an anagram of "ECLIPSE". | ||
| Line 78: | Line 91: | ||
01000010 01*01001 00*10*11 01001001 *101*10* 010*100* | 01000010 01*01001 00*10*11 01001001 *101*10* 010*100* | ||
| − | Discord users | + | Discord users successfully decoded the corrupted binary to read "VULN3RABI7ITY". Typing this in causes the chatbot to respond further: |
Oh.... | Oh.... | ||
| Line 109: | Line 122: | ||
[[File:Archives_image.jpg|thumbnail|right|The image that hid the Archives.zip file]] | [[File:Archives_image.jpg|thumbnail|right|The image that hid the Archives.zip file]] | ||
| − | Discord user whizzer0 hosted [https://drive.google.com/open?id=0BzXFasEE14qrbVBCVkhYc0Rmek0 a copy of pictures.zip] on their Google Drive for faster access, with just the 9 extracted photos [https://drive.google.com/open?id=0BzXFasEE14qrRk5SUjFvU1EwQ3c here]. Discord | + | Discord user whizzer0 hosted [https://drive.google.com/open?id=0BzXFasEE14qrbVBCVkhYc0Rmek0 a copy of pictures.zip] on their Google Drive for faster access, with just the 9 extracted photos [https://drive.google.com/open?id=0BzXFasEE14qrRk5SUjFvU1EwQ3c here]. Discord users realised the filenames of the photos were hex and solved them, but they only held thematic relevance. |
| − | Using the Openpuff tool, | + | Using the Openpuff tool, Discord users discovered a hidden zip file named "Archives.zip" in 4f70656e70756666.jpg, using the passwords A: "Stanford", B: "Deep Blue" and C: "05/04/99". |
=== We are Being Watched === | === We are Being Watched === | ||
| − | Meanwhile, Discord users | + | Meanwhile, other Discord users reported having received a post from KatherinetheGreat on the BBS, suggesting that she was watching the Game Detectives' progress: |
I have been watching you, you are heading in the right direction | I have been watching you, you are heading in the right direction | ||
| Line 154: | Line 167: | ||
Bl4ckZer0 | Bl4ckZer0 | ||
| − | Finally, from adding the dots & dashes in each paragraph of the file, Discord | + | Finally, from adding the dots & dashes in each paragraph of the file, Discord users got this Morse code: |
... .... ....- -.. --- .-- | ... .... ....- -.. --- .-- | ||
| Line 162: | Line 175: | ||
=== Spammimic === | === Spammimic === | ||
| − | Discord | + | Discord users asked the chat Guru about 'spammimic', which led to [http://www.spammimic.com/decodepw.shtml this website] that could be used as a way to encode and decode messages hidden in what appeared to be spam. There were various spam messages found throughout the ARG: |
* Spam #1: From the BBS, contained in a text file called FREE.txt - The key is `Phr3Ak!` and output is [https://www.youtube.com/watch?v=pCvFGZ7ZUas this video]. | * Spam #1: From the BBS, contained in a text file called FREE.txt - The key is `Phr3Ak!` and output is [https://www.youtube.com/watch?v=pCvFGZ7ZUas this video]. | ||
| Line 173: | Line 186: | ||
[[File:KYI QR code.png|thumbnail|right|The QR code that resulted from combining all 4 SSTV signals from each video]] | [[File:KYI QR code.png|thumbnail|right|The QR code that resulted from combining all 4 SSTV signals from each video]] | ||
| − | In each video, some sections had what seemed to be SSTV signals. Discord users | + | In each video, some sections had what seemed to be SSTV signals. Discord users translated the signals from all 4 videos into a single [http://i.imgur.com/5rg2pSN.png QR code], which led to a [https://www.dropbox.com/sh/dxj0ytmd92gljth/AAC9RIfjCRI4gh8IAhjYTYhea/Archives.zip?dl=0 Dropbox link] that contained more files. Again, most of these files pertained to the lore of the ARG and described KatherineTheGreat ultimately ending up on the run from the authorities with her friends. However, one of the files was different: |
| Line 183: | Line 196: | ||
=== 13 hours later... === | === 13 hours later... === | ||
| − | + | Discord users finally cracked the hash - U@D!6i7 was the result of the hash check. | |
We were able to gain access to 52.53.251.28, SSH'ing into it with the username "root" and the password "U@D!6i7". The directory /etc/passwd led to [http://pastebin.com/3P7T141G another message], that urged readers to send an email to [email protected]. Shortly after this discovery was made, KatherineTheGreat appeared in the GameDetectives discord with the username 4b7447. She congratulated us for our hard work, and then went on to say this: | We were able to gain access to 52.53.251.28, SSH'ing into it with the username "root" and the password "U@D!6i7". The directory /etc/passwd led to [http://pastebin.com/3P7T141G another message], that urged readers to send an email to [email protected]. Shortly after this discovery was made, KatherineTheGreat appeared in the GameDetectives discord with the username 4b7447. She congratulated us for our hard work, and then went on to say this: | ||
Latest revision as of 15:59, 7 July 2018
| Kill Your Internet | |
|---|---|
| Kill Your Internet - an ARG that took place in the world of République. | |
| Type | Official |
| Creator | Camouflaj |
| Discovered | 03-18-2016 |
| Completed | 04-02-2016 |
Main Page > List of Investigations > Kill Your Internet
Kill Your Internet was an ARG created by Camouflaj, connected to their game République. It was focused around a retro Bulletin Board System and its administrator, KatherineTheGreat. Puzzles included interacting with chatbots hosted on the BBS, solving puzzles on in-fiction sites, and playing games. The ARG concluded with an IRC chat session between the players and KatherineTheGreat, as well as KtG's artificial intelligence Shahrazad.
Prelude
History
Kill Your Internet, the main site for the ARG, has existed as far back as 2002-11-03 but was first accessible on 2004-01-31. The posts on the site date back to 1996-04-04, but it is unlikely that they were actually created that long ago, as post dates can be easily changed.
The site runs on the WordPress blogging system and has a visual style very reminiscent of the 90s/early 00s internet. Kill Your Internet is run by Camouflaj, the developers of the game Republique. On March 17, they made a post on their Kickstarter page, linking to the Kill Your Internet site.
The BBS
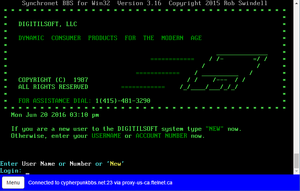
On 2016-03-18, this post was made on Kill Your Internet, embedding a BBS system (Bulletin Board System - a precursor to modern internet forums). The BBS was hosted at cypherpunkbbs.net:23 which claims to be for "Digitilsoft, LLC" and was dated 1987. A phone number was also given, as well as a login prompt. There was also a message at the front of the BBS, explaining how to log in or register a new user on the BBS - but registering a new user required a password of its own. Finding this password was the first puzzle.
Into the BBS
Phone Line
/u/tjjos called 1(415)-481-3290, the number given by the BBS front page. They received four options: 1, Sales; 2, Technical Assistance; 3, Technician Support Hotline; or 4, PBX Systems Operator Menu.
- 1 (Sales) had waiting music followed by the message "I'm sorry, the sales department cannot be reached."
- 2 (Technical Assistance) had waiting music followed by the message "The next technical support operative will be available in approximately 12345 days."
- 3 (Technician Support Hotline) requested "Please enter your 8 digit DIGITILSOFT employee login number."
- 4 (PBX Systems Operator Menu) requested "Please enter your 5 digit system operator code." Entering the wrong code led to the reply of "I'm sorry, the system operator password was not correct. If this is your first time configuring this system, please enter the default password."
By entering the password 12345 (the same number of days remaining on option 2 and a likely default password), /u/tjjos was able to log in as a system operator on option 4, which then presented two further options: 1, System Diagnostics; or 2, Listen to System Operator Voice Support Tickets.
- 1 (System Diagnostics) presented the status of each service: "Sales - offline. Technical assistance - busy. Technician support - online. Data analysis - offline. Point of sale - offline. Legacy Unix systems - online."
- 2 (Listen to System Operator Voice Support Tickets) presented a single voicemail, made by the employee Ev Donald on 1998-11-29. He is with a client but is unable to log in to the employee system (option 3 on the original menu). He then tries to access this again and the tones for his 8-digit employee number can be heard. Ev then says that the system then disconnects, and asks for a solution before hanging up.
With the help of Discord user nanoi, Ev Donald's code was successfully identified as 71469122 and was used to log in to the Technician Support Hotline option, which then informs the caller that the password for user creation is 4E6A863C.
Creating an Account
Entering "New" to create a new user, and inputting the password 4E6A863C when prompted, asks some basic questions that set up your account on the BBS. It then continues with some basic information about the BBS and how to use it, and concludes with this message:
Greetings, I need your help. You were likely guided to this BBS through word of mouth, a CD, a text file, or some form or another. You were sent here because you can be trusted, and you have the skills we need. Many have come before you, and many of have paid the ultimate price protecting what is contained on this BBS. Once, this BBS was a bustling place--an area to trade knowledge, wares and whatever else could be uploaded. That time has long since passed. This BBS was abandoned but it now must serve a new purpose. If you choose to accept this invitation and join us, I must warn you, it is extremely dangerous and once you choose to go down this path, there is no turning back. I am not trying to warn you away, I am trying to invite you in. I have archived many of the conversations from this board for posterity's sake. They are signposts on the road that will guide you to the truth. Welcome to CypherPunk
The Search for the Archives
The Search Begins
The BBS has many different options available, including a directory of text files and a chat bot named the Guru. Pressing 'G' on the main menu of the BBS to get to the text files that are hosted there leads to a list of 13 files. Discord user Emoticon created a Pastebin documenting the contents of the 13 files. Only the 13th file is relevant to the puzzle: it encourages the reader to ask the Guru about the archives, and mentions the letters S, E, P, L, I, C, and E. Discord user nanoi figured out that "S E P L I C E" is an anagram of "ECLIPSE".
Pressing 'C' on the main menu of the BBS, and allows the user to "Talk with the System Guru (Artificial Person)". Speaking to the Guru and then asking it "access to the archives?" has it reply with the following message:
hahahaha.... you're funny! Do you think I would just give you access to the archives that easily? NOPE! Keep dreaming, [username]. How can I be sure I can trust you? Paaasssswwooorrrdddd???
Giving it the password "ECLIPSE" continues with:
Oh wow!! Kate must have sent you. My apologies, [username]. Well... this is awkward now .... Oh yes, the archives! One second while I open this up..................... what's going on here... It appears the password has been corrupted and I can't o pen the archives. Can you help me out? pretty please...? with a cherry on top? 0*01*110 01010101 0**01100 0100*110 00*10*11 0101001* 010*0001 01000010 01*01001 00*10*11 01001001 *101*10* 010*100*
Discord users successfully decoded the corrupted binary to read "VULN3RABI7ITY". Typing this in causes the chatbot to respond further:
Oh.... my... goodness... it worked.... YOU DID IT! WOOOO! I am able to open up the archives now. Thank you very much, [username]! You have proven yourself trustworthy. I've never even opened up the archives before, so I'm not sure what you're going to find. Good luck, and have fun!! Here you go.......... http://bit.ly/1QqoaxZ Can you please tell Kate that I need a vacation!
Questions and Answers
The bit.ly link leads to a .txt file hosted on Dropbox:
The archives that you are looking for have always been located in the the BBS in plain sight. You have had to leave to find you needed to go back to where you started. To move forward, something important in the archive must reveal itself to you. You may require assistance from Mr. Openpuff. Mr. Openpuff won’t help just anybody. To prove you are trustworthy, Mr. Openpuff might have some questions for you. To help you prepare, you may need to know: A) The college Kate was accepted to B) The name of the AI that beat the chess world champion C) The month, day, and year of my interview at the AI lab (ex January 1 1999 = 01/01/99)
Discord user Emoticon solved the answer to A to be Stanford, B to be Deep Blue, and C to be 04/05/99 or 05/04/99. Openpuff was discovered to be a steganography tool hosted by Berkeley University whose page also links to a "CypherPunk manifesto".
Pressing T on the main BBS menu shows a file transfer menu from which many files are accessible. Pressing D here allows one to browse through the various files uploaded to the server. Pressing G selects the correct protocol to download a file; if using the BBS client on KillYourInternet.com, one must then click Menu and then Download to download the file.
Most of the files are assorted texts, games and tools that fit with the BBS theme and are uploaded by Th3w0lf. free.txt was uploaded by Aaron Ly. The most interesting file, Pictures.zip, was uploaded by Unknown.
Discord user whizzer0 hosted a copy of pictures.zip on their Google Drive for faster access, with just the 9 extracted photos here. Discord users realised the filenames of the photos were hex and solved them, but they only held thematic relevance.
Using the Openpuff tool, Discord users discovered a hidden zip file named "Archives.zip" in 4f70656e70756666.jpg, using the passwords A: "Stanford", B: "Deep Blue" and C: "05/04/99".
We are Being Watched
Meanwhile, other Discord users reported having received a post from KatherinetheGreat on the BBS, suggesting that she was watching the Game Detectives' progress:
I have been watching you, you are heading in the right direction
Soon after, multiple users reported receiving strange messages when talking to the chatbot:
THE PIECES ARE ALL THERE LONG LIVE KATHERINE THE GREAT YOU WERE TOO LATE DON'T BE SCARED I AM ALWAYS WATCHING
The Archives
Cipher Puzzles
Archives.zip (mirror needed) contained a variety of documents pertaining to the BBS sysop, KatherineTheGreat's, history; her education at university, development of a sentient AI she called Shahrazad, and the attempt that was made by the U.S. government to confiscate Shahrazad. Rather than let Shahrazad fall into the hands of the government, she opted to destroy it. Archives.zip also contained this file:
Hello I just stumbled onto this BBS and I don't know if anyone is going to read this but I feel like writing about my life. I sense this is a safe place where I can just talk about anything. I'm just going to write stream of conscious about whatever pops into my head. I use to have this friend that carried 32 keys named Alan Gronsfeld who always loved looking through my stuff which prompted me to password protect everything I had. He would always mimic everything I say and would spend his day spamming my inbox with mail so I started calling him spammimic. He wasn't really happy about it at first but it eventually became his nickname around our group of friends. His best friend Derek Hex would even call him by that name. Growing up I didn't really have that many friends. I would spend most of my free time walking around outside or sitting at home reading a book. I would occasionally talk to some of the people in my neighborhood but usually I spent my time alone. I use to live 5 houses away from a man named Bill Caesar and there was always something really fishy about him. People always said that he was a kind-hearted fellow but I would disagree because he was a bad-tempered man. I could sometimes hear him screaming at someone during all hours of the night which always made me worry. My head kept spinning like a merry-go-round because I kept worrying about the well-being of whoever was in the house with this man. I am a strong-willed person so i decided to march over there to check-in on whoever is living there Sju3Cn! 30726221743072 Gq4hpEjw0 MORSE CODE .-
The four blocks of text at the end of the file were decoded using the ciphers referenced in the main text: Gronsfeld, hex, Caesar, and Morse code:
Phr3Ak! 0rb!t0r Bl4ckZer0
Finally, from adding the dots & dashes in each paragraph of the file, Discord users got this Morse code:
... .... ....- -.. --- .-- sh4dow
Spammimic
Discord users asked the chat Guru about 'spammimic', which led to this website that could be used as a way to encode and decode messages hidden in what appeared to be spam. There were various spam messages found throughout the ARG:
- Spam #1: From the BBS, contained in a text file called FREE.txt - The key is `Phr3Ak!` and output is this video.
- Spam #2: From file `Spam - March 10, 2005 5.09 pm PST.ans` in archives folder - The key is `0rb!t0r` and output is this video.
- Spam #3: Discord user Atropos sent `[email protected]` (address also in the spam.ans file) and was replied with an email containing another spam - The key is `Bl4ckZer0` and output is this video.
- Spam #4: In the comment section of the first video. However due to Youtube formatting, the spam needed to be cleaned up a bit to get this. The key is 'sh4dow' and the output is this video.
What's on SSTV?
In each video, some sections had what seemed to be SSTV signals. Discord users translated the signals from all 4 videos into a single QR code, which led to a Dropbox link that contained more files. Again, most of these files pertained to the lore of the ARG and described KatherineTheGreat ultimately ending up on the run from the authorities with her friends. However, one of the files was different:
[email protected] root:0:c878f5455c7f3448623cf4a246d98997872aecbd776eb5ed816aaa0788f43291 53 48 41 32 35 36
53 48 41 32 35 36 is a hex sequence that can be converted to text, meaning SHA256. This led us to believe that the middle line of the file was a hash encrypted with SHA-256. Discord users Benolot and Durendal used Hashcat, a hash brute-forcing tool, to solve the hash over the course of a several hours. Once solved, this hash would be the password needed to connect to the IP provided in the file: 52.53.251.28.
13 hours later...
Discord users finally cracked the hash - U@D!6i7 was the result of the hash check.
We were able to gain access to 52.53.251.28, SSH'ing into it with the username "root" and the password "U@D!6i7". The directory /etc/passwd led to another message, that urged readers to send an email to [email protected]. Shortly after this discovery was made, KatherineTheGreat appeared in the GameDetectives discord with the username 4b7447. She congratulated us for our hard work, and then went on to say this:
If you are willing, I could really use your help. Next week, on Saturday 4/2 9:00 PM PST I have a special surprise planned for Treglazov, but I can't do it alone. If you want to help log onto the BBS @ 9:00.
(Note: Treglazov is the fictitious dictator of the oppressive Metamporphosis regime that Katherine is on the run from, in the fiction of the ARG. Metamorphosis and Treglazov exist in the video game Republique.)
IRC and Satellites
The CypherPunk IRC Channel
About 30 minutes before the scheduled time (Saturday 4/2 @ 9:00 PM PST), KtG messaged users on the BBS, telling them to join an IRC channel: cypherpunkbbs.net/6667, #punks. A complete chat log of the evening can be found here.
After joining the server, we were greeted by KatherinetheGreat and her AI companion, Shahrazad. Shahrazad was uploaded to a satellite called Remus that was equipped with a laser, which was used to destroy a Metamorphosis satellite. "Radar images" (in ANSI form) of the satellites were posted to the BBS as KtG and Shahrazad continued to chat with us in IRC. These images can be found here, courtesy of Jr.
The Evening Standard
Shahrazad was able to get some information from the satellite before destroying it, including some classified files and Metamorphosis' internal news site, The Evening Standard. In those classified files, ESIS_PASS.txt revealed that the password for Evening_Standard_Internal_Server.7z was a combination of answers to puzzles hosted on the Evening Standard site. Evening_Standard_Internal_Server.7z was unlocked with the password "ambiguousenigmaprohibit729531864", which yielded a hash.
Cracking the hash gave the password "!E5t3@6", which was used to unlock DoD Files and e-mails.7z. (This password is weird and contains a newline character, so it may not work for you - the decrypted file can be found here). The file contained sensitive information about Treglazov, leader of Metamorphosis, and KtG concluded this information would be helpful to the resistance - this sensitive information was the end goal of this entire escapade. After thanking everyone, KtG claimed to be hearing sirens and seeing police lights, before signing out of the IRC channel.
Conclusion
Shortly after this, we were given a bunch of free keys for Republique on Steam, and congratulated by its creator. This suggested that the ARG had reached its conclusion.