Difference between revisions of "Sombra ARG"
| [unchecked revision] | [checked revision] |
m (→Skull Video) |
(Rejected the last text change (by Itechbrand) and restored revision 19078 by 01101000 01101001) |
||
| (292 intermediate revisions by 24 users not shown) | |||
| Line 2: | Line 2: | ||
| float = right | | float = right | ||
| name = Sombra ARG | | name = Sombra ARG | ||
| − | | image = File: | + | | image = File:Sombra_skull.png |
| − | |||
| description= The Sombra ARG - an ARG involving an unreleased Overwatch hero. | | description= The Sombra ARG - an ARG involving an unreleased Overwatch hero. | ||
| − | | creator = Blizzard | + | | creator = [https://www.blizzard.com/ Blizzard Entertainment] |
| − | | type = | + | | type = Official |
| − | | status = | + | | status = Completed |
| − | | discovered = 06-12- | + | | discovered = 2016-06-12 |
| + | | completed = 2016-11-04 | ||
}} | }} | ||
| − | + | {{ArgHeader}} | |
| − | The Sombra ARG | + | The Sombra ARG was an ARG for the first-person shooter [https://www.playoverwatch.com Overwatch], developed by [https://www.blizzard.com/ Blizzard Entertainment]. Sombra was the name of a then-unreleased Overwatch hero. The ARG was comprised of clues and ciphers referencing Sombra, which were found in various developer updates and short animations. |
| − | + | At the game's release, there were numerous pieces of in-game information that appeared in the map Dorado, hinting at a character called Sombra. When the hero Ana was revealed, more Sombra clues appeared in Ana's origin video. In the weeks that followed, more clues were discovered, which led up to a character reveal animation at BlizzCon 2016. | |
| − | = Ana Videos = | + | == Ana Videos == |
| − | == Ana Origin Video == | + | === Ana Origin Video === |
| − | On July 12, 2016, a [https://www.youtube.com/watch?v=TE0CXgpNxG0 video] for the new Overwatch hero named Ana was released. | + | On July 12, 2016, a [https://www.youtube.com/watch?v=TE0CXgpNxG0 video] for the new Overwatch hero named Ana was released. At the 1:16 mark, players discovered a set of hexidecmial values: |
[[File:Ana_Hex2.png|400px]] | [[File:Ana_Hex2.png|400px]] | ||
| − | + | <pre> | |
| − | + | 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E | |
| − | + | 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 | |
| − | + | 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 | |
| − | + | 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 | |
| − | + | 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 | |
| − | + | 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 | |
| − | + | 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 | |
| − | + | 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 | |
| − | + | 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 | |
| + | 72 7B 20 67 78 73 72 65 2E 2E 2E 64 78 7A 75 | ||
| + | </pre> | ||
| − | + | A hex to ASCII translation yielded the following: | |
| − | + | <pre> | |
| − | + | ...{v fbr c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...{v fbr c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...{v fbr c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...{v fbr | |
| + | c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...dxzu | ||
| + | </pre> | ||
| − | + | Using an XOR Cipher with the constant 23 on the above text resulted in the following message: | |
| − | + | <pre> | |
| − | + | ..la que tiene la información; tiene el poder...la que tiene la información; tiene el poder...la que tiene la información; tiene el poder...la que tiene la | |
| + | información; tiene el poder...somb | ||
| + | </pre> | ||
| − | + | This was a repeating phrase in Spanish, which translated to: | |
| + | <pre> | ||
| + | She who has the information, has the power... | ||
| + | </pre> | ||
| − | + | Players then discovered a second set of hexidecimal values at the 2:11 mark: | |
| − | |||
[[File:Ana Hex.png|400px]] | [[File:Ana Hex.png|400px]] | ||
| − | + | <pre> | |
| − | + | 65 76 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 | |
| − | + | 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 | |
| − | + | 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 | |
| − | + | 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 | |
| − | + | 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B | |
| − | + | 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 | |
| − | + | 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 | |
| − | + | 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B | |
| − | + | 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 | |
| − | + | 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E | |
| − | + | </pre> | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | When put through the same process, the same string of Spanish was revealed, but with the letters <code>ra</code> at the beginning of the message. These letters were combined with <code>somb</code> from the first cipher to create the name <code>sombra</code>. No more clues were discovered until the release of the Dev Update video. | |
| − | == Dev Update Video == | + | === Dev Update Video === |
[[File:Sombra Barcodes.png|thumbnail|right|The vertical barcodes found at the end of the Ana Dev Update video]] | [[File:Sombra Barcodes.png|thumbnail|right|The vertical barcodes found at the end of the Ana Dev Update video]] | ||
| − | + | On July 19, 2016, the first [https://www.youtube.com/watch?v=evghkilg2eQ Developer Update] was released for Ana. At the end of the video, players discovered a series of vertical barcodes. When scanned, players discovered a large set of hexidecimal values which where then converted to binary, a dump of which is available [https://gist.github.com/zapu/31165efab0d6264e2fd0fa75cc53b1aa here]. | |
| − | + | Turning the ones and zeroes into black and white pixels formed a QR code: | |
[[File:Sombra_QR_code.png|300px]] | [[File:Sombra_QR_code.png|300px]] | ||
| − | Scanning this QR code yielded the following message: | + | Scanning this QR code yielded the following message: <code>¿Estuvo eso facilito? Ahora que tengo su atención, déjenme se las pongo más difícil.</code> In English, the message reads: <code>Was that easy? Well, now that I have your attention, allow me to make things much more difficult.</code> After this, no more clues were discovered until the Summer Games video was released. |
| − | + | == Welcome to the Summer Games Video == | |
| − | + | === Tracer Trail Cipher === | |
| − | + | [[File:Base64_trail.jpg|thumbnail|right|The unsolved base64 cipher in the Summer Games video]] | |
| − | + | '''Note: The cipher described below remains unsolved.''' | |
| − | + | On August 2, 2016, players discovered another cipher in the [https://www.youtube.com/watch?v=qpcOD9tJM4k Welcome to the Summer Games trailer]: | |
| − | |||
| − | On August 2, another cipher | ||
| + | <pre> | ||
U2FsdGVkX1+vupppZksvRf5pq5g5XjFRIipRkwB0K1Y96Qsv2L | U2FsdGVkX1+vupppZksvRf5pq5g5XjFRIipRkwB0K1Y96Qsv2L | ||
m+31cmzaAILwytX/z66ZVWEQM/ccf1g+9m5Ubu1+sit+A9cenD | m+31cmzaAILwytX/z66ZVWEQM/ccf1g+9m5Ubu1+sit+A9cenD | ||
xxqkIaxbm4cMeh2oKhqIHhdaBKOi6XX2XDWpa6+P5o9MQw== | xxqkIaxbm4cMeh2oKhqIHhdaBKOi6XX2XDWpa6+P5o9MQw== | ||
| + | </pre> | ||
| − | + | Players discovered this text to be base64 encryption. When decrypted, players received the following output: | |
| + | <pre> | ||
Salted__���ifK/E�i��9^1Q�*Q�t+V=� | Salted__���ifK/E�i��9^1Q�*Q�t+V=� | ||
/ع��W/ | /ع��W/ | ||
�_����V��?q����f�F���"��=q�������[�� | �_����V��?q����f�F���"��=q�������[�� | ||
z��*����Z����u�\5�k�C | z��*����Z����u�\5�k�C | ||
| − | + | </pre> | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ''(Note: copy/pasting this string will not work; some of the characters are not printable and are not even displayed correctly on this page)'' | |
| − | + | ==== Decrypting the Cipher ==== | |
| − | + | The "Salted__" header at the start of the string indicated to players that the remainder of the text was encrypted with the OpenSSL software library, which requires a password and the encryption cipher that was used. Salt is added by OpenSSL to ensure uniqueness of the key and the IV derived from the password and used for the encryption. However, due to the age of OpenSSL and its massive library, it was proven to be quite difficult for players to identify the encryption used. | |
==== Narrowing Down Ciphers ==== | ==== Narrowing Down Ciphers ==== | ||
| Line 137: | Line 124: | ||
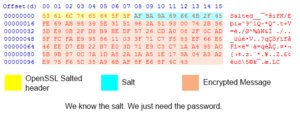
[[File:HexOfEncryptedMessage.png|thumbnail|right|Hex view of the encrypted string]] | [[File:HexOfEncryptedMessage.png|thumbnail|right|Hex view of the encrypted string]] | ||
| − | + | Players narrowed down the potential ciphers used by examining a hex dump of the encrypted string. There are two major types of ciphers, stream ciphers and block ciphers. Stream ciphers encrypt only the data fed into them, whereas block ciphers always encrypt a certain number of bytes at a time (a "chunk"). | |
A byte is roughly a single character, but special characters can take up multiple bytes. We know that OpenSSL Salted Encryption uses the first 8 bytes of the output for <code>Salted__</code> and the next 8 bytes for the actual salt. The rest of the information is the '''encrypted message'''. | A byte is roughly a single character, but special characters can take up multiple bytes. We know that OpenSSL Salted Encryption uses the first 8 bytes of the output for <code>Salted__</code> and the next 8 bytes for the actual salt. The rest of the information is the '''encrypted message'''. | ||
| − | The immediately interesting thing here is that the '''encrypted message''' data stops 3 bytes short of a full chunk. This is a excellent indicator that the cipher used is a stream cipher (or a block cipher in CTR/OFB/CFB mode). This narrows | + | The immediately interesting thing here is that the '''encrypted message''' data stops 3 bytes short of a full chunk. This is a excellent indicator that the cipher used is a stream cipher (or a block cipher in CTR/OFB/CFB mode). This narrows the list of potential ciphers down significantly. This also means that the final string that Blizzard encrypted is less than 93 bytes! |
| + | |||
| + | '''This cipher remains unsolved, but it's speculated that Blizzard moved past the cipher by creating alternate puzzles.''' | ||
=== Directions & Letters === | === Directions & Letters === | ||
| − | + | Players discovered that in the North American version of the Summer Games trailer there were repeated references to the cardinal directions, each associated with a particular hero. These references were conspicuously absent from other versions of the trailer. These references are shown below, with the relevant heroes and timestamps: | |
| − | |||
<gallery mode="packed"> | <gallery mode="packed"> | ||
File:Ow1.png|East - Mercy - Route 66 - 0:17 | File:Ow1.png|East - Mercy - Route 66 - 0:17 | ||
| Line 159: | Line 147: | ||
File:Ow9.png|Northwest - Tracer - King's Row - 0:47 | File:Ow9.png|Northwest - Tracer - King's Row - 0:47 | ||
</gallery> | </gallery> | ||
| − | |||
| − | + | Screenshots of all the directions and their respective heroes can be found in an album [https://imgur.com/a/FQXmy here]. | |
[[File:Overwatch map.jpg|frameless]] | [[File:Overwatch map.jpg|frameless]] | ||
| − | + | These heroes, arranged in this particular order, provided a password that was used later in the ARG. | |
| + | == Dorado Photo == | ||
| − | + | At an unknown date, a new, "corrupted" photo of the [https://blzgdapipro-a.akamaihd.net/media/screenshot/dorado-screenshot-004.jpg Dorado attackers spawn point] was added to the Overwatch [https://playoverwatch.com/en-us/media/ media page]. Players discovered that the screenshot was "'''datamoshed'''", which means it concealed a hidden message while also taking on a distorted appearance. ([https://prntscr.com/c3dce7 Here] is an example of purposely data moshing the image manually to achieve similar effects.) | |
| − | <gallery mode="packed"> | + | <gallery mode="packed" heights=500px> |
File:dorado-datamosh.jpg|The datamoshed image | File:dorado-datamosh.jpg|The datamoshed image | ||
File:dorado-screenshot-005.jpg|The original image | File:dorado-screenshot-005.jpg|The original image | ||
</gallery> | </gallery> | ||
| − | After comparing the images | + | After comparing the images with difference checking tools, players found that certain English and Spanish characters were replaced with exclamation points. The missing characters produced the following Spanish phrase: |
| − | + | <code>Por que estan mirando al cielo? La respuesta no esta sobre sus cabezas, esta detras de ustedes. A veces, necesitan analizar sus logros previos.</code> | |
| − | Translated into English, this phrase | + | Translated into English, this phrase read: |
| − | + | <code>Why are you looking at the sky? The answer isn't over your heads, it's behind you. Sometimes, you need to analyze your previous achievements.</code> | |
| − | = | + | The phrase "Why are you looking at the sky?" was most likely a reference to a strange artifact that was discovered in the sky of the Dorado map, dubbed the "Skycode". The Skycode ended up being a red herring, and was completely unrelated to the ARG. |
| + | |||
| + | === Analyzing Achievements === | ||
[[File:achievements.png|thumbnail|right|"¿" Achievement, comment in source code]] | [[File:achievements.png|thumbnail|right|"¿" Achievement, comment in source code]] | ||
| − | + | The phrase "you need to analyze your previous achievements" led players to look at the achievements on the [https://www.playoverwatch.com Overwatch] website. It was noticed that by logging in and viewing the achievements on a player profile, a mystery achievement appeared. Examining a hex dump of the image lead players to a new phrase: | |
| − | |||
| − | Vientos, nada mal. No obstante, me aburro. Intentemos algo nuevo en la misma dirección. uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 | + | <pre> |
| − | + | Vientos, nada mal. No obstante, me aburro. Intentemos algo nuevo en la misma dirección. | |
| + | uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 IS8208O913KRlrx | ||
| + | </pre> | ||
| − | Translated, it | + | Translated, it said: |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | <pre> | ||
| + | Damn, not bad. However, I'm getting bored. Let's try something new in the same direction. | ||
uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 IS8208O913KRlrx | uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 IS8208O913KRlrx | ||
| + | </pre> | ||
| − | + | == Volskaya Datamosh == | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | After a long period of toying around, players discovered that the ciphertext <code> uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 IS8208O913KRlrx</code> from the "?" achievement was a Vigenére cipher. Players discovered the key <code>tracertorbjornwinstonsymmetradvamercybastiongenjimccree</code> by ordering the heroes in the Summer Games trailer by the cardinal directions associated with each of them, as said further above. Once decoded, players received the following text: | |
| + | <pre>blzgdapiproaakamaihdnetmediascreenshot 5552E494 78B3 4CE9 ACF6 EF8208F913CFjpg</pre> | ||
| − | + | Players found this to be a [https://blzgdapipro-a.akamaihd.net/media/screenshot/5552E494-78B3-4CE9-ACF6-EF8208F913CF.jpg blzgdapipro-a.akamaihd.net/media/screenshot/5552E494-78B3-4CE9-ACF6-EF8208F913CF.jpg URL], which led players to a datamoshed screenshot of the Volskaya Industries map. ''(Editor's note: This link appears to now be dead)''. When players ran a difference check with the [https://blzgdapipro-a.akamaihd.net/media/screenshot/volskaya-screenshot-004.jpg original image], they received an interesting message. | |
<gallery mode="packed"> | <gallery mode="packed"> | ||
| Line 225: | Line 203: | ||
</gallery> | </gallery> | ||
| − | + | === ASCII Skull #1 === | |
| + | |||
| + | The diff from the datamoshed image resulted in the following output: | ||
| + | <pre> | ||
Parece que te gustan estos jueguitos... por que no jugamos uno de verdad? | Parece que te gustan estos jueguitos... por que no jugamos uno de verdad? | ||
:PB@Bk: | :PB@Bk: | ||
| Line 253: | Line 234: | ||
vMB :@B@ :BO7 | vMB :@B@ :BO7 | ||
,B@B | ,B@B | ||
| + | </pre> | ||
'''Translation:''' | '''Translation:''' | ||
| + | <pre> | ||
"It seems you like these little games... Why don't we play a real one?" | "It seems you like these little games... Why don't we play a real one?" | ||
| + | </pre> | ||
| + | |||
| + | (''This is the python2 script to extract modified bytes from datamoshed Volskaya screenshot: https://gist.github.com/synap5e/27635d2ff6f0e3b15f0c902dca2974a9'') | ||
| − | + | No further progress was made until August 23, 2016. | |
| − | = Overwatch Forums Glitching Page/ "Skycoder" = | + | == Overwatch Forums Glitching Page/ "Skycoder" == |
| − | + | On August 23rd, 2016, at an unknown time, an [https://us.battle.net/forums/en/overwatch/topic/20748794686 ominous post] by a user named "Skycoder" appeared on the official General Discussion forums for Overwatch. | |
| − | + | ||
| − | + | Players found that the name of the post, <code>00110010 00110011</code>, was binary for "23," which was a direct reference to Sombra being the 23rd hero in Overwatch. The age of the post started at 24 hours, and counted down rather than increasing. The post itself contained a single sentence in Spanish: | |
| − | + | ||
| − | + | <pre> | |
| + | la que tiene la información; tiene el poder | ||
| + | </pre> | ||
| + | |||
| + | Which, when translated to english, reads: | ||
| + | |||
| + | <pre> | ||
| + | She who has the information, has the power. | ||
| + | </pre> | ||
| + | |||
| + | After a short while, the post glitched and distorted, gradually turning a hue of purple. A text box then appeared, which printed the following ciphertext: | ||
| + | |||
| + | <pre> | ||
| + | ICAgICAgICAgICAgICAgICAgICAgICAgICA6UEKPQms6CiAgICAgICAg | ||
| + | ICAgICAgICAgICAgICAsakKIQEJAQkBCQEJCTC4KICAgICAgICAgICAg | ||
| + | ICAgICAgIDdHlkKTQpVCTU1NTU1CQEJAQkBOcgogICAgICAgICAgICAg | ||
| + | ICA6a0KSQpCIl01NT01PTU9NT01NTU2MQphCQEIxLAogICAgICAgICAg | ||
| + | IDo1kUKNQphCiEJCTU1PTU9NT01PTU9NT01NipJuQm5CQEJCdS4KICAg | ||
| + | ICAgICA3MG6GlUKIQpJClEJYQkJPTU9NT01PTU9NT01NQk1QQphCiEJA | ||
| + | QkBCQE5yCiAgICAgIEeYlpdCSiBpQohCh4ggIE9CTU9NT01PTU9NT01P | ||
| + | TZYyICBCj0JAQi4gRUJAQkBTCiAgICAgIJKWQk2HR0pCVS4gIGlTdUKI | ||
| + | T01PTU9NT01PTU9NTZdPVTE6ICAua0JMTYhNhkKXCiAgICAgIEKMTU1C | ||
| + | mUIgICAgICAgN4hCQk1NT01PTU9NT01PQkKWOiAgICAgICBCh0JNTYhC | ||
| + | CiAgICAgII2YiEKKQiAgICAgICAgIDeSlkBNTU9NT01PTU1AQkA6ICAg | ||
| + | ICAgICAgQEBCQEJACiAgICAgII+ST0xCLiAgICAgICAgICBCTkKPTU1P | ||
| + | TU9NTY9CRUIgICAgICAgICAgckJqTYRCCiAgICAgIJBAICBAICAgICAg | ||
| + | ICAgICBNICBPQk9NT01NQHEgIE0gICAgICAgICAgLkAgIEBACiAgICAg | ||
| + | IISVT3ZCICAgICAgICAgICBCOnWMTU1PTU9NTUJKaUIgICAgICAgICAg | ||
| + | LkJ2TUBCCiAgICAgIIRCkUKYSiAgICAgICAgIDCRQpdNTU9NT01PTUKV | ||
| + | QkB1ICAgICAgICAgcUBAQEJACiAgICAgIEKETUJCjHYgICAgICAgR4+L | ||
| + | Qk1NTU1NTU1NTU1NQkKINSAgICAgICBGhEJNTUBCCiAgICAgIIdCQk1/ | ||
| + | QlBOaSAgIExNRUKFT01NTU2PQoNNTU9NTYpCWk03ICAgckVxQodNQkKE | ||
| + | CiAgICAgIEKYloRCTSAgQm1ChEIgIHFCTU9NQpBChUKEQk1PTUJMICBC | ||
| + | QEJAQiAgQEJAQkBNCiAgICAgICBKlm2GhFBCj0KEQplCN0eIT01CQi4g | ||
| + | ICAsQE1NTUBxTEJAQkBAQEJxQkBCQnYKICAgICAgICAgIGlHQpUsaTCE | ||
| + | TZZCbk1NT4tFICA6ICBNQE9NTUBAQEJAUGlpQEBOOgogICAgICAgICAg | ||
| + | ICAgLiAgIEKXTZBCj01NTUBCQEJAQkBNTU1AQEBNQEIKICAgICAgICAg | ||
| + | ICAgICAgICBAQkBCLmlATUJCQEJAQkBAQk1AOjpCQEJACiAgICAgICAg | ||
| + | ICAgICAgICAgQkBAQCAuQkBCLjpAQkAgOkJAQiAgQEJATwogICAgICAg | ||
| + | ICAgICAgICAgICAgOjAgckBCQCAgQkBAIC5AQkA6IFA6CiAgICAgICAg | ||
| + | ICAgICAgICAgICAgICAgdk1CIDpAQkAgOkJPNwogICAgICAgICAgICAg | ||
| + | ICAgICAgICAgICAgICAsQkBCCg== | ||
| + | </pre> | ||
| + | |||
| + | === ASCII Skull #2 === | ||
| + | |||
| + | Players discovered that this was Base64 and, once decrypted, resulted in another ASCII skull: | ||
| − | + | <pre> | |
| + | :PB.Bk: | ||
| + | ,jBˆ@B@B@B@BBL. | ||
| + | 7G–B“B•BMMMMMB@B@B@Nr | ||
| + | :kB’B.ˆ—MMOMOMOMOMMMMŒB˜B@B1, | ||
| + | :5‘B.B˜BˆBBMMOMOMOMOMOMOMMŠ’nBnB@BBu. | ||
| + | 70n†•BˆB’B”BXBBOMOMOMOMOMOMMBMPB˜BˆB@B@B@Nr | ||
| + | G˜–—BJ iBˆB‡ˆ OBMOMOMOMOMOMOM–2 B.B@B. EB@B@S | ||
| + | ’–BM‡GJBU. iSuBˆOMOMOMOMOMOMM—OU1: .kBLMˆM†B— | ||
| + | BŒMMB™B 7ˆBBMMOMOMOMOMOBB–: B‡BMMˆB | ||
| + | .˜ˆBŠB 7’–@MMOMOMOMM@B@: @@B@B@ | ||
| + | .’OLB. BNB.MMOMOMM.BEB rBjM„B | ||
| + | .@ @ M OBOMOMM@q M .@ @@ | ||
| + | „•OvB B:uŒMMOMOMMBJiB .BvM@B | ||
| + | „B‘B˜J 0‘B—MMOMOMOMB•B@u q@@@B@ | ||
| + | B„MBBŒv G.‹BMMMMMMMMMMMBBˆ5 F„BMM@B | ||
| + | ‡BBM.BPNi LMEB…OMMMM.BƒMMOMMŠBZM7 rEqB‡MBB„ | ||
| + | B˜–„BM BmB„B qBMOMB.B…B„BMOMBL B@B@B @B@B@M | ||
| + | J–m†„PB.B„B™B7GˆOMBB. ,@MMM@qLB@B@@@BqB@BBv | ||
| + | iGB•,i0„M–BnMMO‹E : M@OMM@@@B@Pii@@N: | ||
| + | . B—M.B.MMM@B@B@B@MMM@@@M@B | ||
| + | @[email protected]@MBB@B@B@@BM@::B@B@ | ||
| + | B@@@ .B@B.:@B@ :B@B @B@O | ||
| + | :0 r@B@ B@@ .@B@: P: | ||
| + | vMB :@B@ :BO7 | ||
| + | ,B@B | ||
| + | </pre> | ||
| − | + | Players discovered that, once both skulls had been stripped of spaces, the bytes of each skull that aren't equal to 0 could be subtracted using [https://pastebin.com/g3kA1Pif a script]. Once compiled, players received the following string: | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | <pre> | |
| + | OHVSURPHWLXQMXHJR...FUHRTXHXVWHGHVORVGHWHFWLYHVGHMXHJRVOROODPDULDQXQWUDLOKHDG?EOCJGDXVD-DPEDV-FDODYHUDV.KWPO | ||
| + | </pre> | ||
| − | + | Players discovered that this was a caesar cipher. After shifting the string forward 23 places, it resulted in: | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | <pre> | |
LESPROMETIUNJUEGO...CREOQUEUSTEDESLOSDETECTIVESDEJUEGOSLOLLAMARIANUNTRAILHEAD?BLZGDAUSA-AMBAS-CALAVERAS.HTML | LESPROMETIUNJUEGO...CREOQUEUSTEDESLOSDETECTIVESDEJUEGOSLOLLAMARIANUNTRAILHEAD?BLZGDAUSA-AMBAS-CALAVERAS.HTML | ||
| + | </pre> | ||
| + | |||
| + | When cleaned up, the message read: | ||
| + | |||
| + | <pre> | ||
| + | Les prometi un juego...creo que ustedes los Detectives de Juegos lo llamarían un trailhead? BLZGDUSA-AMBAS-CALAVERAS.HTML | ||
| + | </pre> | ||
| − | + | When translated from Spanish to English: | |
| − | |||
| − | + | <pre> | |
| + | I promised you a game...I believe you Game Detectives would call it a trailhead? BLZGDAUSA-AMBAS-CALAVERAS.HTML | ||
| + | </pre> | ||
| − | + | <code>USA-AMBAS-CALAVERAS</code> translated to <code>USE-BOTH-SKULLS</code>, and the <code>.HTML</code> extension hinted at a URL. | |
| − | + | === Skull Video === | |
| − | |||
| − | + | BLZGDA refers to the servers that Blizzard uses to host media on their website. As such, this led players to [ https://blzgdapipro-a.akamaihd.net/media/screenshot/usa-ambas-calaveras.html this page], which contains a video of a vitals screen depicting a skull and some other medical information. In addition, it also contained a graphic of one of the ASCII skulls. An Imgur mirror can be found [https://i.imgur.com/6Pk69LX.png here]. | |
| − | + | Within the properties of the video, players found another comment in Spanish: | |
| − | + | <pre> | |
Parecen estar muy interesados en estos "héroes". ¿Tal vez les interese conocer algunos detallitos que he averiguado sobre ellos? | Parecen estar muy interesados en estos "héroes". ¿Tal vez les interese conocer algunos detallitos que he averiguado sobre ellos? | ||
| − | + | </pre> | |
| − | + | ||
| + | In English: | ||
| + | |||
| + | <pre> | ||
| + | You seem to be very interested in these "heroes". Maybe interested to know some details that I found out about them? | ||
| + | </pre> | ||
| + | |||
| + | In addition, the video contains a heartbeat monitor, and a series of 26 lines above it. When players assigned the letters of the alphabet to the 26 lines, and used the "pings" of the heartbeat to determine what letters to use, the following string was found: | ||
| − | + | <pre> | |
momentincrime | momentincrime | ||
| + | </pre> | ||
| − | = | + | === amomentincrime E-mail === |
| − | 'momentincrime' appeared to refer to | + | 'momentincrime' appeared to refer to the in-universe TV show "A Moment in Crime," which can be seen in the Roadhog and Junkrat [https://www.youtube.com/watch?v=l5kTATxt7bE video] that came out months before the release of Overwatch. However, players also discovered a website, [https://amomentincrime.com amomentincrime.com], and displayed the following text: |
| + | <pre> | ||
...Estableciendo conexión... | ...Estableciendo conexión... | ||
...Protocolo Sombra v1.3 iniciado... | ...Protocolo Sombra v1.3 iniciado... | ||
| Line 364: | Line 387: | ||
...Terminando conexión... | ...Terminando conexión... | ||
| + | </pre> | ||
| + | |||
| + | Players discovered that sending an e-mail to [email protected] resulted in an automated email response: | ||
| + | |||
| + | <pre> | ||
| + | Thank you for contacting A Moment in Crime's anonymous crime line! | ||
| + | |||
| + | We have analyzed your submission and forwarded the information to the relevant parties. Your help could be vital in apprehending these cri | ||
| + | |||
| + | ...Estableciendo conexión... | ||
| + | ...Protocolo Sombra v1.7 iniciado... | ||
| + | |||
| + | |||
| + | 01:07:47 02:02:02 01:08:06 02:13:43 01:18:32 | ||
| + | 01:18:21 02:10:19 01:06:21 02:05:18 01:04:02 | ||
| + | 01:07:08 02:18:25 01:13:04 02:19:20 01:23:02 | ||
| + | 01:16:40 02:16:35 01:23:04 02:17:16 01:06:42 | ||
| + | 01:13:29 02:18:06 01:05:02 02:15:41 01:08:34 | ||
| + | |||
| + | j.7F57O,NLv:qj.7B:,1qv@B1j5ivB:, | ||
| + | |||
| + | ...Terminando conexión... | ||
| + | |||
| + | minals and bringing them to justice. These fugitives are responsible for a string of robberies, arson, and other crimes stretching from Sydney to King's Row. | ||
| + | |||
| + | Authorities believe that they have set their sights on crossing the Atlantic to America. | ||
| + | </pre> | ||
| + | |||
| + | Players discovered that, if the sets of numbers were taken as AA:BB:CC, where AA was the number of skull (in order of discovery), BB was the row and CC was the column (as seen [https://i.imgur.com/ZgN2MVQ.png here]), and organized into a 5x5 matrix, it would result in: | ||
| − | + | <pre> | |
| + | S j G B L | ||
| + | . @ M O k | ||
| + | i , v : 0 | ||
| + | E 7 r q N | ||
| + | J P 5 F 1 | ||
| + | </pre> | ||
| − | + | Players discovered that this Matrix could be used as a bifid key to decode the text underneath the table of numbers in the email, as shown below: | |
| + | <pre> | ||
| + | j . 7 F 5 7 O , N L v : q j . 7 B : , 1 q v @ B 1 j 5 i v B : , | ||
| + | 12 21 42 54 53 42 24 32 45 15 33 34 44 12 21 42 14 34 32 55 44 33 22 14 55 12 53 31 33 14 34 32 | ||
| − | + | 1 2 2 1 4 2 5 4 5 3 4 2 2 4 3 2 4 5 1 5 3 3 3 4 4 4 1 2 2 1 4 2 | |
| + | 1 4 3 4 3 2 5 5 4 4 3 3 2 2 1 4 5 5 1 2 5 3 3 1 3 3 1 4 3 4 3 2 | ||
| + | 11 24 23 14 43 22 55 45 54 34 43 23 22 42 31 24 45 55 11 52 35 33 33 41 43 43 11 24 23 14 43 22 | ||
| + | </pre> | ||
| + | |||
| + | This gave players the following string: | ||
| + | |||
| + | SOMBr@1NF:rM@7iON1SP0vvErrSOMBr@ | ||
| + | This phrase was found to be leet-speak, and was translated to: | ||
| + | |||
| + | <pre> | ||
| + | Sombra Information is power Sombra | ||
| + | </pre> | ||
| + | |||
| + | The string <code>SOMBr@1NF:rM@7iON1SP0vvErrSOMBr@</code> was used as a password later on in the ARG. | ||
| + | |||
| + | == A Moment in Crime Transmission == | ||
| + | |||
| + | [[File:Momentincrime.png|thumbnail|right|amomentincrime.com as of August 24th, 2016]] | ||
| + | |||
| + | Once the 23-hour countdown on the Skycoder forum post reached zero, [https://amomentincrime.com amomentincrime.com] was updated. It now read: | ||
| + | |||
| + | <pre> | ||
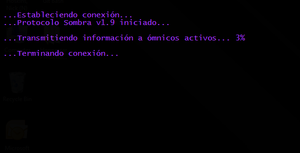
...Estableciendo conexión... | ...Estableciendo conexión... | ||
| − | ...Protocolo Sombra v1. | + | ...Protocolo Sombra v1.9 iniciado... |
| + | ...Transmitiendo información a ómnicos activos... 2% | ||
| − | + | ...Terminando conexión... | |
| − | + | </pre> | |
| − | + | ||
| − | + | Translated from Spanish to English: | |
| − | + | ||
| + | <pre> | ||
| + | ...Establishing connection... | ||
| + | ...Sombra Protocol v1.9 initiated... | ||
| + | ...Transmitting information to active omnics... 2% | ||
| − | + | ...Ending connection... | |
| + | </pre> | ||
| + | |||
| + | A comment was also added to the source code: | ||
| + | |||
| + | <pre> | ||
| + | Bien hecho, ya tienen mi clave. Hackear este programa de televisión no tuvo chiste. Espérense a lo que sigue. | ||
| + | </pre> | ||
| + | |||
| + | When translated: | ||
| + | |||
| + | <pre> | ||
| + | Well done, you have my password. Hacking this television program was meaningless. Wait for what is coming. | ||
| + | </pre> | ||
| + | |||
| + | The percent on the amomentincrime.com slowly increased over time. Once the 5% milestone was hit, the Sombra Protocol version number changed to to v1.95. Afterwards, the percentage increased by 0.0038% every 3 minutes in real time. | ||
| + | |||
| + | In addition, another comment was added: | ||
| + | |||
| + | <pre> | ||
| + | Parece que se están calentando un poco las cosas... tendré que pasar desapercibida mientras esto se finaliza. | ||
| + | </pre> | ||
| + | |||
| + | Translated: | ||
| + | |||
| + | <pre> | ||
| + | It seems things are heating up a bit... I'll have to go unnoticed while this is finishing. | ||
| + | </pre> | ||
| + | |||
| + | On 18th October at 19:02 GMT the site reached 100%, and the site updated with the following message: | ||
| + | |||
| + | <pre> | ||
| + | ...Transmisión finalizada - finalizando carga... | ||
| + | ...Carga finalizada. Unidad Bastion E-54 comprometida... | ||
| + | </pre> | ||
| + | |||
| + | Which roughly translates to: | ||
| + | |||
| + | <pre> | ||
| + | ...Transmission complete - finishing upload... | ||
| + | ...Upload finished. Unit Bastion E-54 engaged... | ||
| + | </pre> | ||
| + | |||
| + | Hidden in the source code of the site was the text <code>v1.4.0.2.324??</code>. Players then correctly assumed that this referred to a future build of Overwatch itself. | ||
| + | |||
| + | == Sombra vs. LumériCo == | ||
| + | |||
| + | === The Hacked Bastion === | ||
| + | |||
| + | On October 19, 2016, a new Overwatch version was released - version 1.4.0.2.32448. Shortly afterwards, the version number in the source code of the amomentincrime site updated to the same version number. After the build launched, players discovered that the hero Bastion had a strange interaction when near the "SOMBRA PROTOCOL" monitors on Dorado, and would emit a message in morse code, which can be heard [https://www.youtube.com/watch?v=Hkd__ceYm-Y here]. When the morse was decoded, players received the following string: | ||
| + | <pre> | ||
| + | SQOFJFBNITIZWGDXSDO | ||
| + | </pre> | ||
| + | |||
| + | Players discovered that this was a Vigenere cipher, and the key consisted of the alphabetic characters from the | ||
| + | <code>SOMBr@1NF:rM@7iON1SP0vvErrSOMBr@</code> string, it was decoded to read: | ||
| + | |||
| + | <pre> | ||
| + | ACCESSWWWLUMERICOMX | ||
| + | </pre> | ||
| + | |||
| + | This led players to the [https://lumerico.mx/ LumeriCo website]. ''(Editor's note: as of 2018, this site appears to be inactive.)'' | ||
| + | |||
| + | === LuméReaction === | ||
| + | |||
| + | [[File:Lumerico.png|thumbnail|right|The homepage of https://lumerico.mx]] | ||
| + | |||
| + | The LumeriCo website was for the in-universe Mexican tech giant LumériCo, who had built several reactors in the Dorado region. The website had a [https://lumerico.mx/news news page], noting the imminent opening of a new reactor on November 1 as well as a recent attack on its construction site. There were also [https://lumerico.mx/about About] and [https://lumerico.mx/login Login] pages. | ||
| + | |||
| + | Players also discovered a <code>robot.txt</code> file, which appeared to server no purpose and only contained the text <code>Allow: omnics</code>, and appeared to be a joke about the [https://en.wikipedia.org/wiki/Robots_exclusion_standard Robots exclusion standard]. Another text file was discovered called <code>omnics.txt</code>, which contained the text: | ||
| + | |||
| + | <pre> | ||
| + | Allow: ?? | ||
| + | Allow: ??? | ||
| + | </pre> | ||
| + | |||
| + | And appeared to be yet anotehr joke about the Robots exclusion standard. And, finally, an <code>api</code> file that contained <code>{"message":"thanks for calling the api"}</code> and, humorously, has no practical purpose. | ||
| + | |||
| + | === Phone Number === | ||
| + | |||
| + | At the bottom of the LumeriCo website, players discovered a phone number <code>(510) 766-2726</code>. When called, players heard a woman listing off a string of numbers in Spanish, a recording of which can be found [https://soundcloud.com/jackwilsdon/510-766-2726a here]. The numbers spoken are: <code>5-2-4-1-3 (pause) 23-4-14-8-6-18-17-23-21-18-15</code>. | ||
| + | When assuming that a=1, b=2, etc, the second part of the message can be decoded to: <code>WDNHFRQWURO</code>. This was found to be a ROT-23 cipher, and decoded to: <code>TAKECONTROL</code>. | ||
| + | |||
| + | === Take Control === | ||
| + | |||
| + | The phone message led players to an important [https://lumerico.mx/TAKECONTROL/index.html page] on the site, under the directory <code>TAKECONTROL</code>. It was styled the same way as amomentincrime.com and featured [https://lumerico.mx/calavera.png an image of Sombra's skull icon], named "calavera.png". There was also text on the page: | ||
| + | |||
| + | <pre style="word-break:break-all;word-wrap: break-word;"> | ||
| + | ethldtíoíesnoemfetuylm.bnlsssqtann)hcnslararuCpdGeoopéqubdsroaan.arnasdmdor1vrsmerñerlsdacnnnoaexedsidcn.iarsgcyi,iqeqnd.pooitoaeaaransterLetéáedasodocMrnseeiuCsimnosetlójnueodacapsadcoanfasest.rnucaodacadmdoemoipíogPoipbehaSussai.,yccandin.reueatenaoiorneoeetaoéyenimt¿rPehec,uurobudeílrysriteenasni,adngpjrálireecgrolsmhYnao?nmonomepeldezmapcpunoaulrrruCstmeitltetlróesoapsdéyufcuascaa,rensbuinergnqedlmvlbpdtaz.enebuineuldoerecrGefqfirrasulrbeatHsilnbaúaeeaaooassraooa,ioedo:aLiuielPr ursmoootlnielteeánlosulobeauaanopearrúiesltéyrosssisuaaeaenremsieaismdjmolrsspebiecdéyusittnvrcacp.taebrtLiunróporner | ||
| + | |||
| + | eúcrneuyraarsettsyrseen.aaPnrneuyraeastuCpnhl/wLloaloa.qartlsyuínreute.evgdpiuábdmPooucvdeccmoreurr.o?unriorydbaSnalegeáezadienáutalaaioeemfcbgdinableoc¿éppoeocelsumuoaHearsosqadrrrftuLiorannnoneneriiatcnlomoqnaqdunrcno,enmerosaereisloabolii.e.dormerosepopdé,eo:r#5scoegaqoeaibs(edioraamtdírnlyoetjcgratmnrrobnrsstloeYqoeocicpnómlpernmaepogenmodqamubodnaeasuaenMoolloupeqvgrLtúr | ||
| + | |||
| + | tsosrdvoeaerroaeusdmaauamoMobsnaeanraunnt,roierbeoiemaodbmantursotñauoureeuoerreopc.etlr | ||
| + | |||
| + | sotñneerLimeaFsNJ | ||
| + | </pre> | ||
| + | |||
| + | Players found this to be a column order transposition cipher with the key <code>5 2 4 1 3</code>, which was found in the phone message. The cleaned up result was: | ||
| + | |||
| + | <pre> | ||
| + | Los felicito por haber llegado hasta aquí. Solo quería saber si estaban listos. (Hey, es muy difícil encontrar buena ayuda últimamente...deberían ver algunos de los payasitos que están trabajando conmigo) Por ahora, continuemos con el verdadero reto: acabar con LumériCo y su president e Guillermo Portero. ¿Y porqué? Porque es un hombre codicioso, corrupto y un ladrón abominable. Su plan de traer en línea el más grande y el más poderoso zigurat el 1 de noviembre no es nada más que una artimaña, un elaborado plan designado para ejercer aún más influencia sobre la gente de México y en gordar los bolsillos de sus compinches. ¿Y quién va a pagar por eso? La gente común y corriente, los mismos que siempre quedan olvidados. | ||
| + | |||
| + | He empezado a mejorar mis protocolos para que sean usados para derrumbar la infraestructura de LumériCo y Los Muertos también están intentando levantarse en contra de la corrupción. Mientras tanto, escarben por el sitio de LumériCo y busquen información que podamos usar en contra del cabrón, mejor aún, encuentren su nombre de usuario y contraseña para asegurarnos de que ciertos detalles no muy favorables sobre el presidentito...aparezcan... | ||
| + | |||
| + | Pude encontrar el nombre de usuario y contraseña de un empleado de soporte de LumériCo, empiecen por ahí: | ||
| + | |||
| + | GFlores/g#fNwP5qJ | ||
| + | </pre> | ||
| + | |||
| + | Translated: | ||
| + | |||
| + | <pre> | ||
| + | I'm congratulating you for getting in here. I only wanted to know if you were ready or not. (Hey, it's really difficult to get good help lately... you should see some of the clowns I'm working with). For now, let's continue with the true challenge: taking down Lumerico Corp president Guillermo Portero. Why? Because he's a greedy and corrupt man, and an abominable thief. His plan of bringing in line the most powerful and biggest zigurat the 1st of november us nothing more than a deceit, an elaborate plan by his gang to become even more influential in the people of Mexico and get more money. And who's gonna pay for that? Common people, the ones that are always forgotten. | ||
| + | |||
| + | I've started upgrading my protocols so that they are used to take down the Lumerico Corp infraestructure and Los Muertos are also trying to go against the corruption. Meanwhile, search the Lumerico Corp site for info we can use against the bastard, or better, get his username and password so that hundreds "not so favorable" facts about the president start popping up. | ||
| + | I was able to get the username and pass of a Lumerico Corp employee, start here: | ||
| + | |||
| + | GFlores/g#fNwP5qJ | ||
| + | </pre> | ||
| + | |||
| + | === Presidential Login === | ||
| + | |||
| + | Players used the credentials above on the [https://lumerico.mx/login Lumerico login page], and accessed the account of Gonzalo Flores, which included [https://lumerico.mx/email his emails]. Transcripts of these emails were archived [https://docs.google.com/spreadsheets/d/1zh7OU2dEOnD4X43ImvZBNpS75FLkj-rL75pXJ2l3TuQ/htmlview?sle=true# here]. | ||
| + | |||
| + | However, only one email had relevance to the ARG: | ||
| + | |||
| + | <pre> | ||
| + | De:Valeria Valderrama<[email protected]> | ||
| + | Para:Gonzalo Flores<[email protected]> | ||
| + | Asunto:Página de Guillermo | ||
| + | |||
| + | Hola, Gonzo: | ||
| + | ¿Puedes ver el tráfico de https://lumerico.mx/president-bypass? Guillermo debería ser el único accediendo desde su página de inicio privada, pero parece que está teniendo mucho tráfico. Tal vez tengamos que escalar esto a | ||
| + | la señorita Jiménez, pero quiero estar segura de que es digno de su tiempo. | ||
| + | |||
| + | Valeria Valderrama | ||
| + | </pre> | ||
| + | |||
| + | The email referenced high traffic on the [https://lumerico.mx/president-bypass President Bypass Link]. The page displayed an "access denied" message, but players found a <code>President Auth-Bypass Revision 1.02: /.git/</code> line in the source code. | ||
| + | |||
| + | This line led players to [https://github.com/internetwache/GitTools/tree/master/Dumper dump the data] from the [https://lumerico.mx/president-bypass/.git/ /.git/ subpage] with git protocol and upload it to [https://gist.github.com/anonymous/987beb6a5c817b53da820562854bdebe Github]. These were the code files behind the website, and included a '''class.authentication.php''' file that contained an encryption function, and '''class.president-bypass.php''' file which contained the president's (Guillermo Portero) username, <code>GPortero</code>, and encrypted password <code>?MzY:MTI5:?AzY:OWM?:?EDO:ZGU?:jVTM:MTJm:2ITM:MTUw:?QjY:OWY?:?kTO:MTQx:?MzY</code>. | ||
| + | |||
| + | Some players wrote a function to decode the encrypted <code>class.authentication.php</code> file, and then used it on the encrypted password. The resulting password was <code>Xy@4+Bkuqd<53uJ</code>. | ||
| + | |||
| + | After logging in to the President's account, players were able to read his emails. After 30 minutes, another email appeared in the President's inbox, from Sombra herself: | ||
| + | |||
| + | <pre> | ||
| + | Veo que se han podido infiltrar en su correo. | ||
| + | No se preocupen, él no puede ver este correo, lo he ocultado de su vista si se conecta desde una de sus direcciones conocidas de IP. | ||
| + | Necesito un poco más de tiempo para establecer el próximo grupo de potocolos. Manténganse atentos a principios de la otra semana. Le echaré unos cuantos trapitos sucios en sus correos para que se filtren al público | ||
| + | "accidentalmente". Ya veremos como reaccionan los medios de comunicación. | ||
| + | </pre> | ||
| + | |||
| + | The rough translation was: | ||
| + | |||
| + | <pre> | ||
| + | I see you have been able to infiltrate into his mail. | ||
| + | Don't worry, he cannot see this email, I've hidden it from his sight if he connects from one of his known IP addresses. | ||
| + | I need a little bit of time to establish the next set of protocols. Stay alert early next week. I'll throw some dirty laundry in his emails that can "accidentally" leak to the public. We'll see how the media will react to that. | ||
| + | </pre> | ||
| + | |||
| + | === Admin Access === | ||
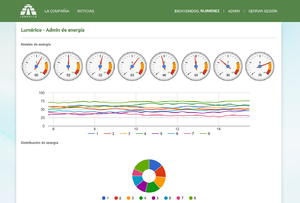
| + | |||
| + | [[File:Lumerico admin panel.png|thumbnail|right|The admin panel of the Lumerico site, only accessible by logging in as MJimenez]] | ||
| + | |||
| + | On October 25, 2016, new emails were discovered in the GFlores account, but they had no immediate significance to the ARG. In addition, omnics.txt was updated: | ||
| + | |||
| + | <pre> | ||
| + | Allow: Tzolk'in | ||
| + | Allow: Imix ChikchanManik Imix ChikchanImixChikchanImix Manik Chikchan Imix Kimi Chikchan Chikchan Kimi ChikchanImixChikchanImix ChikchanKimi | ||
| + | </pre> | ||
| + | |||
| + | Tzolk'in is the name of a [[Wikipedia:Maya calendar#Tzolk'in|Mayan Calendar]], and the second line was a series of animals from it in the Tzolk'in dialect. Imix stands for Day 1, Chikchan — 5, Manik — 7 and Kimi — 6. When turned into numbers, the string read <code>1 57 1 5151 7 5 1 6 5 5 6 5151 56</code>. These digits turned into pictograms of [[Wikipedia:Maya numerals|Maya numerals]] (one by one, not numbers as a whole) written horizontally become <code>. -..- . -.-. ..- - . .- - - .- -.-. -.-</code> This was found to be morse code, and decoded to: <code>EXECUTEATTACK</code>. | ||
| + | |||
| + | This led players to the "EXECUTEATTACK" [https://lumerico.mx/EXECUTEATTACK/index.html directory], where the following text was discovered: | ||
| + | |||
| + | <pre> | ||
| + | Ha llegado el momento. Esos correos expuestos la verdad sobre Portero, iniciado la revuelta, y hemos convencido a la gente de México a apoyar nuestra causa. Ahora es el momento para el golpe. Convertiremos su preciada inauguración el 1 de noviembre en un gran movimiento en su contra. Necesito que hagan una cosa: | ||
| + | Consigan acceso al correo del jefa de seguridad y busquen alguna forma de ayudarme en el ataque. Es posible que lo vean contactando a Portero pronto. He cambiado su contraseña a: d0r*NuLw9 | ||
| + | </pre> | ||
| + | |||
| + | Translated to English: | ||
| + | |||
| + | <pre> | ||
| + | The moment has come. These emails exposed the truth about Portero, initiated the revolt, and have convinced people of Mexico to support our cause. Now is the time to strike. Convert his precious inauguration on November 1 to a large movement against it. I need you to do one thing: | ||
| + | Get access to the email security chief and seek some form of help in the attack. You may see her contacting Portero soon. I've changed her password: d0r*NuLw9 | ||
| + | </pre> | ||
| + | |||
| + | Logging in with the credentials <code>MJimenez / d0r*NuLw9</code> gave players access to the [https://lumerico.mx/admin admin panel] of the LumeriCo reactor. Until November 1, 2016, it stayed inactive and any command was answered with the same message saying that the terminal disconnected. | ||
| + | |||
| + | === The Terminal === | ||
| + | Once the console became usable, players could type <code>help</code> to see a list of commands: | ||
| + | |||
| + | <pre> | ||
| + | override Engineer safety mode override | ||
| + | help Provides help information about commands | ||
| + | version Displays system version information | ||
| + | about Displays information about the system | ||
| + | grep Search output by string | ||
| + | </pre> | ||
| + | |||
| + | In the MJimenez email account, there was an email labeled <code>Corrupción de correo electrónico</code> with highlighted text in side of it, specifically <code>/ter/</code>. Players discovered that performing the Linux command <code>about | grep 'ter'</code> in the console returned this text: | ||
| + | |||
| + | <pre> | ||
| + | Open source lightweight shell for any terminal. | ||
| + | Anything with a terminal | ||
| + | 1.1.0 - expanded terminal support | ||
| + | </pre> | ||
| + | |||
| + | The first word of every line given from the output was bolded and purple. Putting the letters together, players received the text <code>OpenAnything1.1.0</code>, which was a later solution. | ||
| + | |||
| + | Another available command for the terminal was <code>override</code>, and prompted players with three security questions: | ||
| + | |||
| + | # '''Favorite Movie'''. The answer to the prompt is <code>some like it bot</code>, a movie from the Overwatch universe. | ||
| + | # '''Favorite Cookie Flavor'''. The answer being <code>nuevas sabor delicias</code>, a flavor referenced in an email in the MJimenez account. | ||
| + | # '''Secret'''. The answer to this prompt is <code>OpenAnything1.1.0</code>. | ||
| + | |||
| + | This returned <code>OK</code>, gave players admin access, and enabled a new set of commands: | ||
| + | |||
| + | '''ls''' Lists files by path | ||
| + | '''cat''' Read file by path | ||
| + | '''exec''' Execute a file | ||
| + | |||
| + | Typing <code>ls</code> listed two files: <code>payload</code> and <code>d_ilqh_nhb.html</code> (the file name was a ROT23 for ''a_fine_key''). | ||
| + | |||
| + | [[Image:A fine key.png|thumb|right|a_fine_key.html]] Reading the second file with <code>cat mnt/d_ilqh_nhb.html</code> yielded a text where ASCII characters (repeating string <code>vhnl tldv xyl vcxelo xv qhrtv. zkolg[nl]</code>) were in a shape of a key. Deciphering it using an Affine cipher (A=23, B=23) yielded the following string: <code>some keys are shaped as locks. index[me]</code>. It is assumed that ''some keys are shaped as locks'' line alluded to the [[#Tracer_Trail_Cipher|Tracer Trail]] ciphertext being used as a key. | ||
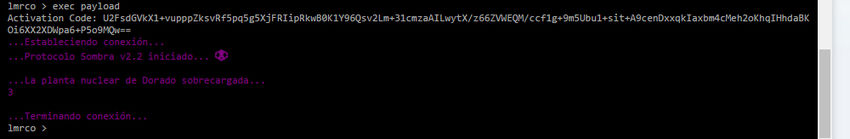
| + | |||
| + | Simultaneously, entering <code>exec payload</code> presented players with a prompt — the answer to which was the [[#Tracer_Trail_Cipher|Tracer Trail]]. When inputted, players were given a message that looked similar to what was previously seen at amomentincrime.com. The counter shown in the top right was then incremented. | ||
| + | |||
| + | [[Image:LumericoTerminalTracerEntered.jpg|850px]] | ||
| + | |||
| + | === Misdirection === | ||
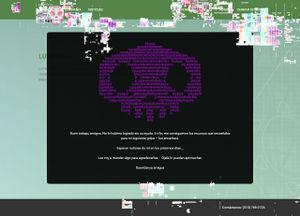
| + | |||
| + | [[Image:LumericoHacked.jpg|thumb|right|lumerico.mx website hacked by Sombra]] | ||
| + | |||
| + | On October 1, 2016, the lumerico.mx home page updated to show "glitches" and a black overlay with a message under a purple skull, and the string <code><!-- MISDIRECTION --></code> was also added to the source of the page. | ||
| + | |||
| + | The message said: | ||
| + | |||
| + | <pre> | ||
| + | Buen trabajo, amigos. No lo hubiera logrado sin su ayuda. En fin, me consiguieron los recursos que necesitaba para mi siguiente golpe – les encantará. | ||
| + | Esperen noticias de mí en los próximos días... | ||
| + | Les voy a mandar algo para agradecerles… Ojalá lo puedan aprovechar. | ||
| + | Dasvidanya amigos | ||
| + | </pre> | ||
| + | |||
| + | Translated: | ||
| + | |||
| + | <pre> | ||
| + | Good job, friends. I would not have done it without your help. Anyway, I got the resources needed for my next hit - you'll love it. | ||
| + | Expect to hear from me in the coming days... | ||
| + | I'm going to send something to thank you ... Hopefully you can use it. | ||
| + | Dasvidanya friends | ||
| + | </pre> | ||
| + | |||
| + | |||
| + | |||
| + | Note that ''Dasvidanya'' is a phonetic transliteration of ''до свиданья'' — a Russian phrase for "goodbye". The thing that Sombra sent as a ''thank you'' was a new spray, named "Día de Los Muertos" after the Mexican festival that took place at the same time as the ARG. The spray is currently only available on the PC version of the game. | ||
| + | |||
| + | [[File:Dia de los muertos spray.jpg|thumbnail|right|The Día de Los Muertos spray that was added to the game after Sombra hacked the Lumerico site]] | ||
| + | |||
| + | The '''MISDIRECTION''' string lead to the MISDIRECTION [https://lumerico.mx/MISDIRECTION/index.html directory] which contained the text: | ||
| + | |||
| + | <pre> | ||
| + | ...Estableciendo conexiуn... | ||
| + | ...Protocolo Sombra v2.3 iniciado... | ||
| + | |||
| + | ...Desviando datos del zigurat de LumériCo hacia el objetivo... | ||
| + | ...Descifrando contraseсas del objetivo... | ||
| + | ...Acceso otorgado al directorio de volskayaindustries.com... | ||
| + | |||
| + | ...boop ;)... | ||
...Terminando conexión... | ...Terminando conexión... | ||
| + | </pre> | ||
| + | |||
| + | Translated: | ||
| + | |||
| + | <pre> | ||
| + | ...Establishing connection... | ||
| + | ...Sombra Protocol v2.3 initiated... | ||
| + | |||
| + | ...Forwarding the data from the LumériCo ziggurat to the target... | ||
| + | ...Deciphering the target passwords... | ||
| + | ...Access Granted to the directory of volskayaindustries.com... | ||
| − | + | ...boop ;)... | |
| − | + | ...Ending connection.. | |
| − | + | </pre> | |
| + | |||
| + | == Blizzcon == | ||
| + | |||
| + | Blizzcon 2016 opened with the [https://www.youtube.com/watch?v=Og5-Pm4HNlI Overwatch short "Infiltration"], a short depicting Reaper, Widowmaker, and Sombra on Volskaya Industries. During the showing of the short, Sombra's [https://playoverwatch.com/en-us/heroes/sombra hero page] went live, showcasing her abilities and character backstory. | ||
| + | |||
| + | [[File:SombraBG.jpg|center|500px]] | ||
| − | = References = | + | == References == |
| − | == | + | === Community Resources === |
| − | A | + | A collection of tools and resources made by the Game Detectives Discord community for use in the ARG. |
| − | === ASCII Skull === | + | ==== ASCII Skull ==== |
'''ASCII Skull Analysis:''' https://github.com/bahamas10/sombra | '''ASCII Skull Analysis:''' https://github.com/bahamas10/sombra | ||
| − | '''Removing SOMBR@ Analysis:''' | + | '''Removing SOMBR@ Analysis:''' https://pastebin.com/15u27YTC |
'''ASCII Skull Eye Analysys:''' https://docs.google.com/spreadsheets/d/1-JQpWyitMKYhP-4l8ZDFiJI3NjqRrvoEnRdFQawike8 | '''ASCII Skull Eye Analysys:''' https://docs.google.com/spreadsheets/d/1-JQpWyitMKYhP-4l8ZDFiJI3NjqRrvoEnRdFQawike8 | ||
| − | === Google Docs === | + | ==== Google Docs ==== |
'''Observations and Speculations Spreadsheet:''' https://docs.google.com/spreadsheets/d/1rI08baFQmAwaqHC-9GF9VNGCYjuRE-q4LN9k4ottjuQ/pubhtml | '''Observations and Speculations Spreadsheet:''' https://docs.google.com/spreadsheets/d/1rI08baFQmAwaqHC-9GF9VNGCYjuRE-q4LN9k4ottjuQ/pubhtml | ||
| − | === Tracer Code === | + | '''LumériCo Emails and Translations Spreadsheet:''' https://goo.gl/cQgdIJ (Courtesy of UberPilot) |
| + | |||
| + | ==== Tracer Code ==== | ||
| + | |||
| + | '''GOL! Guesser:''' https://axxim.net/ow/gol-guesser/ | ||
| + | |||
| + | '''Uber GOL! Guesser:''' https://axxim.net/ow/gol-guesser/uber/ | ||
| − | + | The Uber GOL! Guesser only prints out UTF-8 compliant results, which makes it easier to identify potentially correct answers. | |
'''Bruteforcing tool:''' https://github.com/glv2/bruteforce-salted-openssl | '''Bruteforcing tool:''' https://github.com/glv2/bruteforce-salted-openssl | ||
| − | == | + | === Third-Party Resources === |
| + | |||
| + | A collection of third-party tools and resources that the Game Detectives Discord community has used in the ARG. | ||
| + | |||
| + | ==== Image of Reaper ==== | ||
| − | + | '''stegdetect (Linux):''' https://github.com/abeluck/stegdetect | |
| − | == Media Appearances == | + | stegdetect is a Linux utility used to determine if a given image may contain encoded information. |
| + | |||
| + | '''JPHide & JPSeek:''' https://linux01.gwdg.de/~alatham/stego.html<br> | ||
| + | '''iSteg (Mac OSX):''' https://www.hanynet.com/isteg/ | ||
| + | |||
| + | JPHide & JPSeek is used to hide and find, respectively, a file inside a JPEG image.<br> | ||
| + | iSteg works similarly to JPHide on the Mac OSX platform. | ||
| + | |||
| + | '''stegbreak (Linux):''' https://linux.die.net/man/1/stegbreak | ||
| + | |||
| + | stegbreak is used to do brute-force dictionary attacks on JPEG images. | ||
| + | |||
| + | === Easter Eggs === | ||
| + | |||
| + | The following are collection of references and Easter Eggs encountered throughout the ARG. | ||
| + | |||
| + | ==== In-Game ==== | ||
| + | |||
| + | '''Sombra's "Amused" Emote''' | ||
| + | |||
| + | This character emote features the [[Sombra_ARG_False_Leads | Skycode]], accompanied by soft music resembling the [https://www.reddit.com/r/Overwatch/comments/4w7ey1/the_sombra_skysong/ Skysong]. Sombra's expression is one of amusement, and it's a nod to the community's prolonged creative attempts to solving an nonexistent puzzle. | ||
| + | |||
| + | [[File:EmoteSkycode.png|200px]] | ||
| + | |||
| + | '''Skycode Spray''' | ||
| + | |||
| + | This character spray features Sombra's iconic skull in front of a compass rose and the [[Sombra_ARG_False_Leads | Skycode]]. This is a reference to both the [[#Directions_&_Letters|cardinal directions]] used in one of the puzzles and to the Skycode, which is considered the most significant false lead that solvers encountered. | ||
| + | |||
| + | [[File:SkycodeSpray.png|200px]] | ||
| + | |||
| + | ==== In-ARG ==== | ||
| + | |||
| + | '''Espresso Command''' | ||
| + | |||
| + | There was a hidden command in LumériCo's [[#The_Terminal | admin terminal]]. Inputting the word <code>espresso</code> returned the following message: <code>Coffee Pot Status: Brewed approximately 23 hours ago, currently 0% full</code> | ||
| + | This is referencing a variety of [https://goo.gl/cQgdIJ emails] found in the LumériCo site involving broken espresso machines and incompetent coffee brewing, which caught the attention of the community and gave way to a vast variety of mediocre jokes. Furthermore, "23 hours" makes reference to the number 23, which was believed by many to possess some sort of significance to the ARG, as Sombra would be the 23rd character in Overwatch. Finally, "0%" references the ARG's notable waiting periods that have been widely criticized by the community, specifically [[#A_Moment_in_Crime_Transmission | A Moment in Crime's upload percentage]]. | ||
| + | Due to the iconic purple text it is believed that this hidden command was created by Sombra herself. | ||
| + | |||
| + | [[File:EspressoCommand.png]] | ||
| + | |||
| + | === Media Appearances === | ||
| − | + | '''3rd Aug. 2016''' | |
| − | [EN] [ | + | [EN] [https://kotaku.com/overwatch-fans-find-new-clues-about-the-mysterious-hero-1784767759 Kotaku - Overwatch Fans Find New Clues About The Mysterious Hero Sombra] |
| − | [EN] [ | + | [EN] [https://www.polygon.com/2016/8/3/12369144/overwatch-summer-games-sombra-arg-blizzard?utm_campaign=polygon&utm_content=chorus&utm_medium=social&utm_source=twitter Polygon - Overwatch fans are trying to crack the latest mystery about Sombra] |
| − | [EN] [ | + | [EN] [https://www.pcgamesn.com/overwatch/overwatch-sombra PCGamesN - Overwatch's Sombra ARG continues with new clues, but no solutions] |
| − | [EN] [ | + | [EN] [https://team-dignitas.net/articles/blogs/overwatch/9989/who-is-sombra-all-facts-and-clues-about-sombra Team-Dignitas - Who is Sombra? All facts and clues about Sombra] |
| − | [FR] [ | + | [FR] [https://overwatch.gamewave.fr/un-nouveau-code-cache-dans-la-derniere-cinematique-d-overwatch/ Gamewave - UN NOUVEAU CODE CACHÉ DANS LA DERNIÈRE CINÉMATIQUE D'OVERWATCH!] |
[EN] [https://www.follownews.com/overwatch-fans-find-new-clues-about-the-mysterious-hero-sombra-1nhqt FollowNews - Overwatch Fans Find New Clues About The Mysterious Hero Sombra] | [EN] [https://www.follownews.com/overwatch-fans-find-new-clues-about-the-mysterious-hero-sombra-1nhqt FollowNews - Overwatch Fans Find New Clues About The Mysterious Hero Sombra] | ||
| − | + | '''4th Aug. 2016''' | |
| + | |||
| + | [EN] [https://www.pcgamer.com/overwatch-summer-games-trailer-hides-a-mysterious-secret/ PCGamer - Overwatch Summer Games trailer hides a mysterious secret] | ||
| − | [ | + | [SK] [https://www.sector.sk/novinka/121273/nove-overwatch-video-obsahuje-dalsie-tajomstva.htm Sector - Nové Overwatch video obsahuje ďalšie tajomstvá] |
| − | [ | + | [EN] [https://www.techinsider.io/overwatch-sombra-character-2016-8 Techinsider - 'Overwatch' players are going to insane lengths to solve a mystery that Blizzard's teased for months] |
| − | [EN] [ | + | [EN] [https://gamerant.com/overwatch-sombra-clues/ Gamerant - Overwatch Players Uncover More ‘Sombra’ Clues] |
| − | [ | + | [HU] [https://www.gamestar.hu/hir/overwatch-sombra-karakter-214739.html Gamestar - Overwatch - újabb nyomok utalnak a még be nem jelentett hősre] |
| − | + | '''5th Aug. 2016''' | |
| − | + | [EN] [https://kotaku.com/days-later-overwatch-fans-cant-figure-out-the-sky-cod-1784872143 Kotaku - Days Later, Overwatch Fans Can't Figure Out The 'Sky Code' Mystery] | |
| − | [EN] [ | ||
| − | [NL] [ | + | [NL] [https://www.gamersnet.nl/nieuws/201608/cryptische_speurtocht_naar_overwatch_nieuwe_heldin_sombra_gaat_bizar_diep/ Gamersnet - Cryptische speurtocht naar Overwatch' nieuwe heldin Sombra gaat bizar diep] |
| − | [ES] [ | + | [ES] [https://www.alfabetajuega.com/noticia/overwatch-el-enigma-de-sombra-sigue-ofreciendo-nuevos-detalles-n-71772 Alfa Beta Jeuga - Overwatch: El enigma de Sombra sigue ofreciendo nuevos detalles] |
[EN] [https://www.youtube.com/watch?v=5ROjN-_F0ZU&feature=youtu.be&t=4m22s IGN (Video) - Sombra: Overwatch's Secret New Hero - Overwatch HQ] | [EN] [https://www.youtube.com/watch?v=5ROjN-_F0ZU&feature=youtu.be&t=4m22s IGN (Video) - Sombra: Overwatch's Secret New Hero - Overwatch HQ] | ||
| − | + | '''7th Aug. 2016''' | |
| − | [EN] [ | + | |
| + | [EN] [https://www.gamespresso.com/2016/08/summary-state-sombras-arg-overwatch/ Gamespresso - Summary of the state of sombra's ARG in Overwatch] | ||
| − | + | '''8th Aug. 2016''' | |
| − | [EN/CN] [ | + | [EN/CN] [https://www.zhentoo.com/doc92368 Zhentoo - Overwatch new hero Secret Dorado hidden mystery] |
| − | [EN] [ | + | [EN] [https://www.technewstoday.com/30880-overwatch-sombra-continues-to-elude-detectives/ TechNewsToday - Overwatch: Sombra Continues to Elude Detectives] |
| − | + | '''11th Aug. 2016''' | |
[EN] [https://www.youtube.com/watch?v=IZR-pa0it4Q The Know - New Overwatch Hero Hints] | [EN] [https://www.youtube.com/watch?v=IZR-pa0it4Q The Know - New Overwatch Hero Hints] | ||
| − | + | '''12th Aug. 2016''' | |
| − | [EN] [ | + | |
| + | [EN] [https://kotaku.com/after-two-weeks-overwatch-fans-sombra-investigation-re-1785204389 Kotaku - Overwatch Fans' Sombra Investigation Reaps A Skull Code] | ||
| + | |||
| + | '''14th Aug. 2016''' | ||
| + | |||
| + | [EN] [https://gamerant.com/overwatch-sombra-skull-code/ Gamerant - Skull Code is Latest Clue in Overwatch’s Sombra Investigation] | ||
| + | |||
| + | '''16th Aug. 2016''' | ||
| + | |||
| + | [EN] [https://www.christiantoday.com/article/overwatch.dlc.update.skull.code.the.latest.clue.for.sombra.investigation/93197.htm Christian Today - 'Overwatch' DLC update: Skull Code the latest clue for Sombra investigation] | ||
| + | |||
| + | [EN] [https://en.yibada.com/articles/151811/20160816/overwatch-dlc-update.htm Yibada - 'Overwatch' DLC update: New clues on Sombra's inclusion to the roster revealed] | ||
| + | |||
| + | '''23rd Aug. 2016''' | ||
| + | |||
| + | [EN] [https://www.technewstoday.com/31129-overwatch-all-we-know-about-the-sombra-arg/ Tech News Today - Overwatch: All We Know About the Sombra ARG] | ||
| + | |||
| + | '''24th Aug. 2016''' | ||
| + | |||
| + | [EN] [https://gamerant.com/overwatch-forums-sombra-message/ Gamerant - Overwatch Forums Glitch Out, Reveals Hidden Message From Sombra] | ||
| + | |||
| + | [EN] [https://gamerant.com/overwatch-sombra-clue-website/ Gamerant - New Website Counts Down To Next Clue For Overwatch’s Sombra] | ||
| + | |||
| + | [EN] [https://www.polygon.com/2016/8/24/12623736/overwatch-sombra-arg-clues-skycoder Polygon - Overwatch's Sombra mystery appears to be coming to a close] | ||
| + | |||
| + | [EN] [https://www.vg247.com/2016/08/24/overwatch-forums-glitch-out-reveal-a-message-from-the-mysterious-sombra/ VG247 - Overwatch forums glitch out, reveal a message from the mysterious Sombra] | ||
| + | |||
| + | [EN] [https://www.technewstoday.com/31151-sombra-hacks-into-overwatch-forums/ Tech News Today - Sombra Hacks Into Overwatch Forums] | ||
| + | |||
| + | [EN] [https://www.ign.com/articles/2016/08/24/overwatch-mystery-character-sombra-could-be-revealed-today IGN - Overwatch Mystery Character Sombra Could Be Revealed Today] | ||
| + | |||
| + | '''25th Aug. 2016''' | ||
| + | |||
| + | [EN] [https://kotaku.com/overwatch-players-are-getting-fed-up-with-the-sombra-ar-1785765307 Kotaku - Overwatch Players Are Getting Sick Of The Sombra ARG] | ||
| + | |||
| + | [EN] [https://www.ign.com/articles/2016/08/25/overwatch-made-the-internet-lose-its-mind-last-night-and-i-had-a-front-row-seat IGN - Overwatch Made the Internet Lose its Mind Last Night, And I Had a Front-Row Seat] | ||
| + | |||
| + | [EN] [https://www.technewstoday.com/31182-overwatch-countdown-to-sombra/ Tech News Today - Overwatch: Countdown to Sombra] | ||
| + | |||
| + | |||
| + | '''30th Aug. 2016''' | ||
| + | |||
| + | [EN] [https://www.pcgamer.com/overwatch-sombra-arg-mystery/ PC Gamer - Overwatch's Sombra riddle begins to irritate the players trying to solve it] | ||
| + | |||
| + | '''3rd Oct. 2016''' | ||
| + | |||
| + | [EN] [https://www.mobilenapps.com/articles/19398/20161003/overwatch-update-sombra-blizzcon-halloween-event-leak.htm Mobile & Apps - Sombra To Be Revealed At Blizzcon? Halloween Event Confirmed In Data Leak] | ||
| + | |||
| + | '''4th Oct. 2016''' | ||
| + | |||
| + | [EN] [https://www.itechpost.com/articles/36011/20161004/overwatch-overwatch-update-overwatch-finally-getting-sombra-overwatch-sombra-sombra.htm iTechPost - Overwatch Update: Are We Finally Getting Sombra?] | ||
| + | |||
| + | '''11th Oct. 2016''' | ||
| + | |||
| + | [EN] [https://www.kotaku.com.au/2016/10/overwatch-fans-hacked-actual-people-in-an-attempt-to-find-sombra/ Kotaku - Overwatch Fans Hacked Actual People In An Attempt To Find Sombra] | ||
| + | |||
| + | '''17th Oct. 2016''' | ||
| + | |||
| + | [EN] [https://telkomgaming.co.za/will-sombra-hack-her-way-into-blizzcon-2016/ TelKom Gaming - Will Sombra Hack Her Way Into BlizzCon 2016?] | ||
| + | |||
| + | '''18th Oct. 2016''' | ||
| + | |||
| + | [EN] [https://overwatchtips.info/overwatch-sombra-arg-everything-you-need-to-know/ OverwatchTips - Everything You NEED To Know (Sombra ARG)] | ||
| + | |||
| + | '''26th Oct. 2016''' | ||
| + | |||
| + | [EN] [https://mic.com/articles/157757/overwatch-sombra-arg-everything-we-know-about-the-countdown-and-rumored-nov-1-release#.UILrZHRiM Min Network - Everything we know about Blizzard's rumored Nov. 1 release] | ||
| + | |||
| + | '''28th Oct. 2016''' | ||
| + | |||
| + | [EN] [https://kotaku.com/imagining-horror-stories-for-a-never-ending-overwatch-a-1788324673 Kotaku - Imagining Horror Stories Of A Never-Ending Overwatch ARG] | ||
| + | |||
| + | '''1st Nov. 2016''' | ||
| + | |||
| + | [EN] [https://www.ign.com/videos/2016/11/01/will-overwatchs-sombra-be-at-blizzcon-2016 IGN - Will Sombra be at BlizzCon 2016?] | ||
| + | |||
| + | '''8th Nov. 2016''' | ||
| + | |||
| + | [EN] [https://mic.com/articles/158812/overwatch-sombra-arg-gameplay-emote-directly-references-one-of-the-wildest-fan-theories Mic Tech - 'Overwatch' Sombra ARG: Gameplay emote directly references one of the wildest fan theories] | ||
Latest revision as of 23:20, 10 September 2020
| Sombra ARG | |
|---|---|
| The Sombra ARG - an ARG involving an unreleased Overwatch hero. | |
| Type | Official |
| Creator | Blizzard Entertainment |
| Discovered | 2016-06-12 |
| Completed | 2016-11-04 |
Main Page > List of Investigations > Sombra ARG
The Sombra ARG was an ARG for the first-person shooter Overwatch, developed by Blizzard Entertainment. Sombra was the name of a then-unreleased Overwatch hero. The ARG was comprised of clues and ciphers referencing Sombra, which were found in various developer updates and short animations.
At the game's release, there were numerous pieces of in-game information that appeared in the map Dorado, hinting at a character called Sombra. When the hero Ana was revealed, more Sombra clues appeared in Ana's origin video. In the weeks that followed, more clues were discovered, which led up to a character reveal animation at BlizzCon 2016.
Contents
Ana Videos
Ana Origin Video
On July 12, 2016, a video for the new Overwatch hero named Ana was released. At the 1:16 mark, players discovered a set of hexidecmial values:
2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 64 78 7A 75
A hex to ASCII translation yielded the following:
...{v fbr c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...{v fbr c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...{v fbr c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...{v fbr
c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...dxzu
Using an XOR Cipher with the constant 23 on the above text resulted in the following message:
..la que tiene la información; tiene el poder...la que tiene la información; tiene el poder...la que tiene la información; tiene el poder...la que tiene la información; tiene el poder...somb
This was a repeating phrase in Spanish, which translated to:
She who has the information, has the power...
Players then discovered a second set of hexidecimal values at the 2:11 mark:
65 76 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E
When put through the same process, the same string of Spanish was revealed, but with the letters ra at the beginning of the message. These letters were combined with somb from the first cipher to create the name sombra. No more clues were discovered until the release of the Dev Update video.
Dev Update Video
On July 19, 2016, the first Developer Update was released for Ana. At the end of the video, players discovered a series of vertical barcodes. When scanned, players discovered a large set of hexidecimal values which where then converted to binary, a dump of which is available here.
Turning the ones and zeroes into black and white pixels formed a QR code:
Scanning this QR code yielded the following message: ¿Estuvo eso facilito? Ahora que tengo su atención, déjenme se las pongo más difícil. In English, the message reads: Was that easy? Well, now that I have your attention, allow me to make things much more difficult. After this, no more clues were discovered until the Summer Games video was released.
Welcome to the Summer Games Video
Tracer Trail Cipher
Note: The cipher described below remains unsolved.
On August 2, 2016, players discovered another cipher in the Welcome to the Summer Games trailer:
U2FsdGVkX1+vupppZksvRf5pq5g5XjFRIipRkwB0K1Y96Qsv2L m+31cmzaAILwytX/z66ZVWEQM/ccf1g+9m5Ubu1+sit+A9cenD xxqkIaxbm4cMeh2oKhqIHhdaBKOi6XX2XDWpa6+P5o9MQw==
Players discovered this text to be base64 encryption. When decrypted, players received the following output:
Salted__���ifK/E�i��9^1Q�*Q�t+V=�
/ع��W/
�_����V��?q����f�F���"��=q�������[��
z��*����Z����u�\5�k�C
(Note: copy/pasting this string will not work; some of the characters are not printable and are not even displayed correctly on this page)
Decrypting the Cipher
The "Salted__" header at the start of the string indicated to players that the remainder of the text was encrypted with the OpenSSL software library, which requires a password and the encryption cipher that was used. Salt is added by OpenSSL to ensure uniqueness of the key and the IV derived from the password and used for the encryption. However, due to the age of OpenSSL and its massive library, it was proven to be quite difficult for players to identify the encryption used.
Narrowing Down Ciphers
Players narrowed down the potential ciphers used by examining a hex dump of the encrypted string. There are two major types of ciphers, stream ciphers and block ciphers. Stream ciphers encrypt only the data fed into them, whereas block ciphers always encrypt a certain number of bytes at a time (a "chunk").
A byte is roughly a single character, but special characters can take up multiple bytes. We know that OpenSSL Salted Encryption uses the first 8 bytes of the output for Salted__ and the next 8 bytes for the actual salt. The rest of the information is the encrypted message.
The immediately interesting thing here is that the encrypted message data stops 3 bytes short of a full chunk. This is a excellent indicator that the cipher used is a stream cipher (or a block cipher in CTR/OFB/CFB mode). This narrows the list of potential ciphers down significantly. This also means that the final string that Blizzard encrypted is less than 93 bytes!
This cipher remains unsolved, but it's speculated that Blizzard moved past the cipher by creating alternate puzzles.
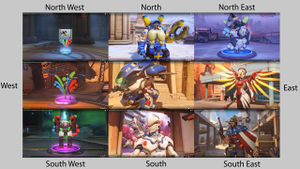
Directions & Letters
Players discovered that in the North American version of the Summer Games trailer there were repeated references to the cardinal directions, each associated with a particular hero. These references were conspicuously absent from other versions of the trailer. These references are shown below, with the relevant heroes and timestamps:
Screenshots of all the directions and their respective heroes can be found in an album here.
These heroes, arranged in this particular order, provided a password that was used later in the ARG.
Dorado Photo
At an unknown date, a new, "corrupted" photo of the Dorado attackers spawn point was added to the Overwatch media page. Players discovered that the screenshot was "datamoshed", which means it concealed a hidden message while also taking on a distorted appearance. (Here is an example of purposely data moshing the image manually to achieve similar effects.)
After comparing the images with difference checking tools, players found that certain English and Spanish characters were replaced with exclamation points. The missing characters produced the following Spanish phrase:
Por que estan mirando al cielo? La respuesta no esta sobre sus cabezas, esta detras de ustedes. A veces, necesitan analizar sus logros previos.
Translated into English, this phrase read:
Why are you looking at the sky? The answer isn't over your heads, it's behind you. Sometimes, you need to analyze your previous achievements.
The phrase "Why are you looking at the sky?" was most likely a reference to a strange artifact that was discovered in the sky of the Dorado map, dubbed the "Skycode". The Skycode ended up being a red herring, and was completely unrelated to the ARG.
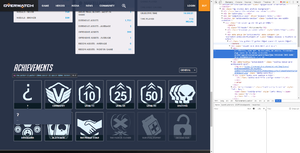
Analyzing Achievements
The phrase "you need to analyze your previous achievements" led players to look at the achievements on the Overwatch website. It was noticed that by logging in and viewing the achievements on a player profile, a mystery achievement appeared. Examining a hex dump of the image lead players to a new phrase:
Vientos, nada mal. No obstante, me aburro. Intentemos algo nuevo en la misma dirección. uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 IS8208O913KRlrx
Translated, it said:
Damn, not bad. However, I'm getting bored. Let's try something new in the same direction. uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 IS8208O913KRlrx
Volskaya Datamosh
After a long period of toying around, players discovered that the ciphertext uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 IS8208O913KRlrx from the "?" achievement was a Vigenére cipher. Players discovered the key tracertorbjornwinstonsymmetradvamercybastiongenjimccree by ordering the heroes in the Summer Games trailer by the cardinal directions associated with each of them, as said further above. Once decoded, players received the following text:
blzgdapiproaakamaihdnetmediascreenshot 5552E494 78B3 4CE9 ACF6 EF8208F913CFjpg
Players found this to be a blzgdapipro-a.akamaihd.net/media/screenshot/5552E494-78B3-4CE9-ACF6-EF8208F913CF.jpg URL, which led players to a datamoshed screenshot of the Volskaya Industries map. (Editor's note: This link appears to now be dead). When players ran a difference check with the original image, they received an interesting message.
ASCII Skull #1
The diff from the datamoshed image resulted in the following output:
Parece que te gustan estos jueguitos... por que no jugamos uno de verdad?
:PB@Bk:
,jB@@B@B@B@BBL.
7G@B@B@BMMMMMB@B@B@Nr
:kB@B@@@MMOMOMOMOMMMM@B@B@B1,
:5@B@B@B@BBMMOMOMOMOMOMOMM@@@B@B@BBu.
70@@@B@B@B@BXBBOMOMOMOMOMOMMBMPB@B@B@B@B@Nr
G@@@BJ iB@B@@ OBMOMOMOMOMOMOM@2 B@B@B. EB@B@S
@@BM@GJBU. iSuB@OMOMOMOMOMOMM@OU1: .kBLM@M@B@
B@MMB@B 7@BBMMOMOMOMOMOBB@: B@BMM@B
@@@B@B 7@@@MMOMOMOMM@B@: @@B@B@
@@OLB. BNB@MMOMOMM@BEB rBjM@B
@@ @ M OBOMOMM@q M .@ @@
@@OvB B:u@MMOMOMMBJiB .BvM@B
@B@B@J 0@B@MMOMOMOMB@B@u q@@@B@
B@MBB@v G@@BMMMMMMMMMMMBB@5 F@BMM@B
@BBM@BPNi LMEB@OMMMM@B@MMOMM@BZM7 rEqB@MBB@
B@@@BM B@B@B qBMOMB@B@B@BMOMBL B@B@B @B@B@M
J@@@@PB@B@B@B7G@OMBB. ,@MMM@qLB@B@@@BqB@BBv
iGB@,i0@M@B@MMO@E : M@OMM@@@B@Pii@@N:
. B@M@B@MMM@B@B@B@MMM@@@M@B
@[email protected]@MBB@B@B@@BM@::B@B@
B@@@ .B@B.:@B@ :B@B @B@O
:0 r@B@ B@@ .@B@: P:
vMB :@B@ :BO7
,B@B
Translation:
"It seems you like these little games... Why don't we play a real one?"
(This is the python2 script to extract modified bytes from datamoshed Volskaya screenshot: https://gist.github.com/synap5e/27635d2ff6f0e3b15f0c902dca2974a9)
No further progress was made until August 23, 2016.
Overwatch Forums Glitching Page/ "Skycoder"
On August 23rd, 2016, at an unknown time, an ominous post by a user named "Skycoder" appeared on the official General Discussion forums for Overwatch.
Players found that the name of the post, 00110010 00110011, was binary for "23," which was a direct reference to Sombra being the 23rd hero in Overwatch. The age of the post started at 24 hours, and counted down rather than increasing. The post itself contained a single sentence in Spanish:
la que tiene la información; tiene el poder
Which, when translated to english, reads:
She who has the information, has the power.
After a short while, the post glitched and distorted, gradually turning a hue of purple. A text box then appeared, which printed the following ciphertext:
ICAgICAgICAgICAgICAgICAgICAgICAgICA6UEKPQms6CiAgICAgICAg ICAgICAgICAgICAgICAsakKIQEJAQkBCQEJCTC4KICAgICAgICAgICAg ICAgICAgIDdHlkKTQpVCTU1NTU1CQEJAQkBOcgogICAgICAgICAgICAg ICA6a0KSQpCIl01NT01PTU9NT01NTU2MQphCQEIxLAogICAgICAgICAg IDo1kUKNQphCiEJCTU1PTU9NT01PTU9NT01NipJuQm5CQEJCdS4KICAg ICAgICA3MG6GlUKIQpJClEJYQkJPTU9NT01PTU9NT01NQk1QQphCiEJA QkBCQE5yCiAgICAgIEeYlpdCSiBpQohCh4ggIE9CTU9NT01PTU9NT01P TZYyICBCj0JAQi4gRUJAQkBTCiAgICAgIJKWQk2HR0pCVS4gIGlTdUKI T01PTU9NT01PTU9NTZdPVTE6ICAua0JMTYhNhkKXCiAgICAgIEKMTU1C mUIgICAgICAgN4hCQk1NT01PTU9NT01PQkKWOiAgICAgICBCh0JNTYhC CiAgICAgII2YiEKKQiAgICAgICAgIDeSlkBNTU9NT01PTU1AQkA6ICAg ICAgICAgQEBCQEJACiAgICAgII+ST0xCLiAgICAgICAgICBCTkKPTU1P TU9NTY9CRUIgICAgICAgICAgckJqTYRCCiAgICAgIJBAICBAICAgICAg ICAgICBNICBPQk9NT01NQHEgIE0gICAgICAgICAgLkAgIEBACiAgICAg IISVT3ZCICAgICAgICAgICBCOnWMTU1PTU9NTUJKaUIgICAgICAgICAg LkJ2TUBCCiAgICAgIIRCkUKYSiAgICAgICAgIDCRQpdNTU9NT01PTUKV QkB1ICAgICAgICAgcUBAQEJACiAgICAgIEKETUJCjHYgICAgICAgR4+L Qk1NTU1NTU1NTU1NQkKINSAgICAgICBGhEJNTUBCCiAgICAgIIdCQk1/ QlBOaSAgIExNRUKFT01NTU2PQoNNTU9NTYpCWk03ICAgckVxQodNQkKE CiAgICAgIEKYloRCTSAgQm1ChEIgIHFCTU9NQpBChUKEQk1PTUJMICBC QEJAQiAgQEJAQkBNCiAgICAgICBKlm2GhFBCj0KEQplCN0eIT01CQi4g ICAsQE1NTUBxTEJAQkBAQEJxQkBCQnYKICAgICAgICAgIGlHQpUsaTCE TZZCbk1NT4tFICA6ICBNQE9NTUBAQEJAUGlpQEBOOgogICAgICAgICAg ICAgLiAgIEKXTZBCj01NTUBCQEJAQkBNTU1AQEBNQEIKICAgICAgICAg ICAgICAgICBAQkBCLmlATUJCQEJAQkBAQk1AOjpCQEJACiAgICAgICAg ICAgICAgICAgQkBAQCAuQkBCLjpAQkAgOkJAQiAgQEJATwogICAgICAg ICAgICAgICAgICAgOjAgckBCQCAgQkBAIC5AQkA6IFA6CiAgICAgICAg ICAgICAgICAgICAgICAgdk1CIDpAQkAgOkJPNwogICAgICAgICAgICAg ICAgICAgICAgICAgICAsQkBCCg==
ASCII Skull #2
Players discovered that this was Base64 and, once decrypted, resulted in another ASCII skull:
:PB.Bk:
,jBˆ@B@B@B@BBL.
7G–B“B•BMMMMMB@B@B@Nr
:kB’B.ˆ—MMOMOMOMOMMMMŒB˜B@B1,
:5‘B.B˜BˆBBMMOMOMOMOMOMOMMŠ’nBnB@BBu.
70n†•BˆB’B”BXBBOMOMOMOMOMOMMBMPB˜BˆB@B@B@Nr
G˜–—BJ iBˆB‡ˆ OBMOMOMOMOMOMOM–2 B.B@B. EB@B@S
’–BM‡GJBU. iSuBˆOMOMOMOMOMOMM—OU1: .kBLMˆM†B—
BŒMMB™B 7ˆBBMMOMOMOMOMOBB–: B‡BMMˆB
.˜ˆBŠB 7’–@MMOMOMOMM@B@: @@B@B@
.’OLB. BNB.MMOMOMM.BEB rBjM„B
.@ @ M OBOMOMM@q M .@ @@
„•OvB B:uŒMMOMOMMBJiB .BvM@B
„B‘B˜J 0‘B—MMOMOMOMB•B@u q@@@B@
B„MBBŒv G.‹BMMMMMMMMMMMBBˆ5 F„BMM@B
‡BBM.BPNi LMEB…OMMMM.BƒMMOMMŠBZM7 rEqB‡MBB„
B˜–„BM BmB„B qBMOMB.B…B„BMOMBL B@B@B @B@B@M
J–m†„PB.B„B™B7GˆOMBB. ,@MMM@qLB@B@@@BqB@BBv
iGB•,i0„M–BnMMO‹E : M@OMM@@@B@Pii@@N:
. B—M.B.MMM@B@B@B@MMM@@@M@B
@[email protected]@MBB@B@B@@BM@::B@B@
B@@@ .B@B.:@B@ :B@B @B@O
:0 r@B@ B@@ .@B@: P:
vMB :@B@ :BO7
,B@B
Players discovered that, once both skulls had been stripped of spaces, the bytes of each skull that aren't equal to 0 could be subtracted using a script. Once compiled, players received the following string:
OHVSURPHWLXQMXHJR...FUHRTXHXVWHGHVORVGHWHFWLYHVGHMXHJRVOROODPDULDQXQWUDLOKHDG?EOCJGDXVD-DPEDV-FDODYHUDV.KWPO
Players discovered that this was a caesar cipher. After shifting the string forward 23 places, it resulted in:
LESPROMETIUNJUEGO...CREOQUEUSTEDESLOSDETECTIVESDEJUEGOSLOLLAMARIANUNTRAILHEAD?BLZGDAUSA-AMBAS-CALAVERAS.HTML
When cleaned up, the message read:
Les prometi un juego...creo que ustedes los Detectives de Juegos lo llamarían un trailhead? BLZGDUSA-AMBAS-CALAVERAS.HTML
When translated from Spanish to English:
I promised you a game...I believe you Game Detectives would call it a trailhead? BLZGDAUSA-AMBAS-CALAVERAS.HTML
USA-AMBAS-CALAVERAS translated to USE-BOTH-SKULLS, and the .HTML extension hinted at a URL.
Skull Video
BLZGDA refers to the servers that Blizzard uses to host media on their website. As such, this led players to [ https://blzgdapipro-a.akamaihd.net/media/screenshot/usa-ambas-calaveras.html this page], which contains a video of a vitals screen depicting a skull and some other medical information. In addition, it also contained a graphic of one of the ASCII skulls. An Imgur mirror can be found here.
Within the properties of the video, players found another comment in Spanish:
Parecen estar muy interesados en estos "héroes". ¿Tal vez les interese conocer algunos detallitos que he averiguado sobre ellos?
In English:
You seem to be very interested in these "heroes". Maybe interested to know some details that I found out about them?
In addition, the video contains a heartbeat monitor, and a series of 26 lines above it. When players assigned the letters of the alphabet to the 26 lines, and used the "pings" of the heartbeat to determine what letters to use, the following string was found:
momentincrime
amomentincrime E-mail
'momentincrime' appeared to refer to the in-universe TV show "A Moment in Crime," which can be seen in the Roadhog and Junkrat video that came out months before the release of Overwatch. However, players also discovered a website, amomentincrime.com, and displayed the following text:
...Estableciendo conexión... ...Protocolo Sombra v1.3 iniciado... ...Infiltrando la respuesta automática del email de pistas... ...Terminando conexión...
Players discovered that sending an e-mail to [email protected] resulted in an automated email response:
Thank you for contacting A Moment in Crime's anonymous crime line! We have analyzed your submission and forwarded the information to the relevant parties. Your help could be vital in apprehending these cri ...Estableciendo conexión... ...Protocolo Sombra v1.7 iniciado... 01:07:47 02:02:02 01:08:06 02:13:43 01:18:32 01:18:21 02:10:19 01:06:21 02:05:18 01:04:02 01:07:08 02:18:25 01:13:04 02:19:20 01:23:02 01:16:40 02:16:35 01:23:04 02:17:16 01:06:42 01:13:29 02:18:06 01:05:02 02:15:41 01:08:34 j.7F57O,NLv:qj.7B:,1qv@B1j5ivB:, ...Terminando conexión... minals and bringing them to justice. These fugitives are responsible for a string of robberies, arson, and other crimes stretching from Sydney to King's Row. Authorities believe that they have set their sights on crossing the Atlantic to America.
Players discovered that, if the sets of numbers were taken as AA:BB:CC, where AA was the number of skull (in order of discovery), BB was the row and CC was the column (as seen here), and organized into a 5x5 matrix, it would result in:
S j G B L . @ M O k i , v : 0 E 7 r q N J P 5 F 1
Players discovered that this Matrix could be used as a bifid key to decode the text underneath the table of numbers in the email, as shown below:
j . 7 F 5 7 O , N L v : q j . 7 B : , 1 q v @ B 1 j 5 i v B : , 12 21 42 54 53 42 24 32 45 15 33 34 44 12 21 42 14 34 32 55 44 33 22 14 55 12 53 31 33 14 34 32 1 2 2 1 4 2 5 4 5 3 4 2 2 4 3 2 4 5 1 5 3 3 3 4 4 4 1 2 2 1 4 2 1 4 3 4 3 2 5 5 4 4 3 3 2 2 1 4 5 5 1 2 5 3 3 1 3 3 1 4 3 4 3 2 11 24 23 14 43 22 55 45 54 34 43 23 22 42 31 24 45 55 11 52 35 33 33 41 43 43 11 24 23 14 43 22
This gave players the following string:
SOMBr@1NF:rM@7iON1SP0vvErrSOMBr@
This phrase was found to be leet-speak, and was translated to:
Sombra Information is power Sombra
The string SOMBr@1NF:rM@7iON1SP0vvErrSOMBr@ was used as a password later on in the ARG.
A Moment in Crime Transmission
Once the 23-hour countdown on the Skycoder forum post reached zero, amomentincrime.com was updated. It now read:
...Estableciendo conexión... ...Protocolo Sombra v1.9 iniciado... ...Transmitiendo información a ómnicos activos... 2% ...Terminando conexión...
Translated from Spanish to English:
...Establishing connection... ...Sombra Protocol v1.9 initiated... ...Transmitting information to active omnics... 2% ...Ending connection...
A comment was also added to the source code:
Bien hecho, ya tienen mi clave. Hackear este programa de televisión no tuvo chiste. Espérense a lo que sigue.
When translated:
Well done, you have my password. Hacking this television program was meaningless. Wait for what is coming.
The percent on the amomentincrime.com slowly increased over time. Once the 5% milestone was hit, the Sombra Protocol version number changed to to v1.95. Afterwards, the percentage increased by 0.0038% every 3 minutes in real time.
In addition, another comment was added:
Parece que se están calentando un poco las cosas... tendré que pasar desapercibida mientras esto se finaliza.
Translated:
It seems things are heating up a bit... I'll have to go unnoticed while this is finishing.
On 18th October at 19:02 GMT the site reached 100%, and the site updated with the following message:
...Transmisión finalizada - finalizando carga... ...Carga finalizada. Unidad Bastion E-54 comprometida...
Which roughly translates to:
...Transmission complete - finishing upload... ...Upload finished. Unit Bastion E-54 engaged...
Hidden in the source code of the site was the text v1.4.0.2.324??. Players then correctly assumed that this referred to a future build of Overwatch itself.
Sombra vs. LumériCo
The Hacked Bastion
On October 19, 2016, a new Overwatch version was released - version 1.4.0.2.32448. Shortly afterwards, the version number in the source code of the amomentincrime site updated to the same version number. After the build launched, players discovered that the hero Bastion had a strange interaction when near the "SOMBRA PROTOCOL" monitors on Dorado, and would emit a message in morse code, which can be heard here. When the morse was decoded, players received the following string:
SQOFJFBNITIZWGDXSDO
Players discovered that this was a Vigenere cipher, and the key consisted of the alphabetic characters from the
SOMBr@1NF:rM@7iON1SP0vvErrSOMBr@ string, it was decoded to read:
ACCESSWWWLUMERICOMX
This led players to the LumeriCo website. (Editor's note: as of 2018, this site appears to be inactive.)
LuméReaction
The LumeriCo website was for the in-universe Mexican tech giant LumériCo, who had built several reactors in the Dorado region. The website had a news page, noting the imminent opening of a new reactor on November 1 as well as a recent attack on its construction site. There were also About and Login pages.
Players also discovered a robot.txt file, which appeared to server no purpose and only contained the text Allow: omnics, and appeared to be a joke about the Robots exclusion standard. Another text file was discovered called omnics.txt, which contained the text:
Allow: ?? Allow: ???
And appeared to be yet anotehr joke about the Robots exclusion standard. And, finally, an api file that contained {"message":"thanks for calling the api"} and, humorously, has no practical purpose.
Phone Number
At the bottom of the LumeriCo website, players discovered a phone number (510) 766-2726. When called, players heard a woman listing off a string of numbers in Spanish, a recording of which can be found here. The numbers spoken are: 5-2-4-1-3 (pause) 23-4-14-8-6-18-17-23-21-18-15.
When assuming that a=1, b=2, etc, the second part of the message can be decoded to: WDNHFRQWURO. This was found to be a ROT-23 cipher, and decoded to: TAKECONTROL.
Take Control
The phone message led players to an important page on the site, under the directory TAKECONTROL. It was styled the same way as amomentincrime.com and featured an image of Sombra's skull icon, named "calavera.png". There was also text on the page:
ethldtíoíesnoemfetuylm.bnlsssqtann)hcnslararuCpdGeoopéqubdsroaan.arnasdmdor1vrsmerñerlsdacnnnoaexedsidcn.iarsgcyi,iqeqnd.pooitoaeaaransterLetéáedasodocMrnseeiuCsimnosetlójnueodacapsadcoanfasest.rnucaodacadmdoemoipíogPoipbehaSussai.,yccandin.reueatenaoiorneoeetaoéyenimt¿rPehec,uurobudeílrysriteenasni,adngpjrálireecgrolsmhYnao?nmonomepeldezmapcpunoaulrrruCstmeitltetlróesoapsdéyufcuascaa,rensbuinergnqedlmvlbpdtaz.enebuineuldoerecrGefqfirrasulrbeatHsilnbaúaeeaaooassraooa,ioedo:aLiuielPr ursmoootlnielteeánlosulobeauaanopearrúiesltéyrosssisuaaeaenremsieaismdjmolrsspebiecdéyusittnvrcacp.taebrtLiunróporner eúcrneuyraarsettsyrseen.aaPnrneuyraeastuCpnhl/wLloaloa.qartlsyuínreute.evgdpiuábdmPooucvdeccmoreurr.o?unriorydbaSnalegeáezadienáutalaaioeemfcbgdinableoc¿éppoeocelsumuoaHearsosqadrrrftuLiorannnoneneriiatcnlomoqnaqdunrcno,enmerosaereisloabolii.e.dormerosepopdé,eo:r#5scoegaqoeaibs(edioraamtdírnlyoetjcgratmnrrobnrsstloeYqoeocicpnómlpernmaepogenmodqamubodnaeasuaenMoolloupeqvgrLtúr tsosrdvoeaerroaeusdmaauamoMobsnaeanraunnt,roierbeoiemaodbmantursotñauoureeuoerreopc.etlr sotñneerLimeaFsNJ
Players found this to be a column order transposition cipher with the key 5 2 4 1 3, which was found in the phone message. The cleaned up result was:
Los felicito por haber llegado hasta aquí. Solo quería saber si estaban listos. (Hey, es muy difícil encontrar buena ayuda últimamente...deberían ver algunos de los payasitos que están trabajando conmigo) Por ahora, continuemos con el verdadero reto: acabar con LumériCo y su president e Guillermo Portero. ¿Y porqué? Porque es un hombre codicioso, corrupto y un ladrón abominable. Su plan de traer en línea el más grande y el más poderoso zigurat el 1 de noviembre no es nada más que una artimaña, un elaborado plan designado para ejercer aún más influencia sobre la gente de México y en gordar los bolsillos de sus compinches. ¿Y quién va a pagar por eso? La gente común y corriente, los mismos que siempre quedan olvidados. He empezado a mejorar mis protocolos para que sean usados para derrumbar la infraestructura de LumériCo y Los Muertos también están intentando levantarse en contra de la corrupción. Mientras tanto, escarben por el sitio de LumériCo y busquen información que podamos usar en contra del cabrón, mejor aún, encuentren su nombre de usuario y contraseña para asegurarnos de que ciertos detalles no muy favorables sobre el presidentito...aparezcan... Pude encontrar el nombre de usuario y contraseña de un empleado de soporte de LumériCo, empiecen por ahí: GFlores/g#fNwP5qJ
Translated:
I'm congratulating you for getting in here. I only wanted to know if you were ready or not. (Hey, it's really difficult to get good help lately... you should see some of the clowns I'm working with). For now, let's continue with the true challenge: taking down Lumerico Corp president Guillermo Portero. Why? Because he's a greedy and corrupt man, and an abominable thief. His plan of bringing in line the most powerful and biggest zigurat the 1st of november us nothing more than a deceit, an elaborate plan by his gang to become even more influential in the people of Mexico and get more money. And who's gonna pay for that? Common people, the ones that are always forgotten. I've started upgrading my protocols so that they are used to take down the Lumerico Corp infraestructure and Los Muertos are also trying to go against the corruption. Meanwhile, search the Lumerico Corp site for info we can use against the bastard, or better, get his username and password so that hundreds "not so favorable" facts about the president start popping up. I was able to get the username and pass of a Lumerico Corp employee, start here: GFlores/g#fNwP5qJ
Presidential Login
Players used the credentials above on the Lumerico login page, and accessed the account of Gonzalo Flores, which included his emails. Transcripts of these emails were archived here.
However, only one email had relevance to the ARG:
De:Valeria Valderrama<[email protected]> Para:Gonzalo Flores<[email protected]> Asunto:Página de Guillermo Hola, Gonzo: ¿Puedes ver el tráfico de https://lumerico.mx/president-bypass? Guillermo debería ser el único accediendo desde su página de inicio privada, pero parece que está teniendo mucho tráfico. Tal vez tengamos que escalar esto a la señorita Jiménez, pero quiero estar segura de que es digno de su tiempo. Valeria Valderrama
The email referenced high traffic on the President Bypass Link. The page displayed an "access denied" message, but players found a President Auth-Bypass Revision 1.02: /.git/ line in the source code.
This line led players to dump the data from the /.git/ subpage with git protocol and upload it to Github. These were the code files behind the website, and included a class.authentication.php file that contained an encryption function, and class.president-bypass.php file which contained the president's (Guillermo Portero) username, GPortero, and encrypted password ?MzY:MTI5:?AzY:OWM?:?EDO:ZGU?:jVTM:MTJm:2ITM:MTUw:?QjY:OWY?:?kTO:MTQx:?MzY.
Some players wrote a function to decode the encrypted class.authentication.php file, and then used it on the encrypted password. The resulting password was Xy@4+Bkuqd<53uJ.
After logging in to the President's account, players were able to read his emails. After 30 minutes, another email appeared in the President's inbox, from Sombra herself:
Veo que se han podido infiltrar en su correo. No se preocupen, él no puede ver este correo, lo he ocultado de su vista si se conecta desde una de sus direcciones conocidas de IP. Necesito un poco más de tiempo para establecer el próximo grupo de potocolos. Manténganse atentos a principios de la otra semana. Le echaré unos cuantos trapitos sucios en sus correos para que se filtren al público "accidentalmente". Ya veremos como reaccionan los medios de comunicación.
The rough translation was:
I see you have been able to infiltrate into his mail. Don't worry, he cannot see this email, I've hidden it from his sight if he connects from one of his known IP addresses. I need a little bit of time to establish the next set of protocols. Stay alert early next week. I'll throw some dirty laundry in his emails that can "accidentally" leak to the public. We'll see how the media will react to that.
Admin Access
On October 25, 2016, new emails were discovered in the GFlores account, but they had no immediate significance to the ARG. In addition, omnics.txt was updated:
Allow: Tzolk'in Allow: Imix ChikchanManik Imix ChikchanImixChikchanImix Manik Chikchan Imix Kimi Chikchan Chikchan Kimi ChikchanImixChikchanImix ChikchanKimi
Tzolk'in is the name of a Mayan Calendar, and the second line was a series of animals from it in the Tzolk'in dialect. Imix stands for Day 1, Chikchan — 5, Manik — 7 and Kimi — 6. When turned into numbers, the string read 1 57 1 5151 7 5 1 6 5 5 6 5151 56. These digits turned into pictograms of Maya numerals (one by one, not numbers as a whole) written horizontally become . -..- . -.-. ..- - . .- - - .- -.-. -.- This was found to be morse code, and decoded to: EXECUTEATTACK.
This led players to the "EXECUTEATTACK" directory, where the following text was discovered:
Ha llegado el momento. Esos correos expuestos la verdad sobre Portero, iniciado la revuelta, y hemos convencido a la gente de México a apoyar nuestra causa. Ahora es el momento para el golpe. Convertiremos su preciada inauguración el 1 de noviembre en un gran movimiento en su contra. Necesito que hagan una cosa: Consigan acceso al correo del jefa de seguridad y busquen alguna forma de ayudarme en el ataque. Es posible que lo vean contactando a Portero pronto. He cambiado su contraseña a: d0r*NuLw9
Translated to English:
The moment has come. These emails exposed the truth about Portero, initiated the revolt, and have convinced people of Mexico to support our cause. Now is the time to strike. Convert his precious inauguration on November 1 to a large movement against it. I need you to do one thing: Get access to the email security chief and seek some form of help in the attack. You may see her contacting Portero soon. I've changed her password: d0r*NuLw9
Logging in with the credentials MJimenez / d0r*NuLw9 gave players access to the admin panel of the LumeriCo reactor. Until November 1, 2016, it stayed inactive and any command was answered with the same message saying that the terminal disconnected.
The Terminal
Once the console became usable, players could type help to see a list of commands:
override Engineer safety mode override help Provides help information about commands version Displays system version information about Displays information about the system grep Search output by string
In the MJimenez email account, there was an email labeled Corrupción de correo electrónico with highlighted text in side of it, specifically /ter/. Players discovered that performing the Linux command about | grep 'ter' in the console returned this text:
Open source lightweight shell for any terminal. Anything with a terminal 1.1.0 - expanded terminal support
The first word of every line given from the output was bolded and purple. Putting the letters together, players received the text OpenAnything1.1.0, which was a later solution.
Another available command for the terminal was override, and prompted players with three security questions:
- Favorite Movie. The answer to the prompt is
some like it bot, a movie from the Overwatch universe. - Favorite Cookie Flavor. The answer being
nuevas sabor delicias, a flavor referenced in an email in the MJimenez account. - Secret. The answer to this prompt is
OpenAnything1.1.0.
This returned OK, gave players admin access, and enabled a new set of commands:
ls Lists files by path cat Read file by path exec Execute a file
Typing ls listed two files: payload and d_ilqh_nhb.html (the file name was a ROT23 for a_fine_key).
cat mnt/d_ilqh_nhb.html yielded a text where ASCII characters (repeating string vhnl tldv xyl vcxelo xv qhrtv. zkolg[nl]) were in a shape of a key. Deciphering it using an Affine cipher (A=23, B=23) yielded the following string: some keys are shaped as locks. index[me]. It is assumed that some keys are shaped as locks line alluded to the Tracer Trail ciphertext being used as a key.
Simultaneously, entering exec payload presented players with a prompt — the answer to which was the Tracer Trail. When inputted, players were given a message that looked similar to what was previously seen at amomentincrime.com. The counter shown in the top right was then incremented.
Misdirection
On October 1, 2016, the lumerico.mx home page updated to show "glitches" and a black overlay with a message under a purple skull, and the string <!-- MISDIRECTION --> was also added to the source of the page.
The message said:
Buen trabajo, amigos. No lo hubiera logrado sin su ayuda. En fin, me consiguieron los recursos que necesitaba para mi siguiente golpe – les encantará. Esperen noticias de mí en los próximos días... Les voy a mandar algo para agradecerles… Ojalá lo puedan aprovechar. Dasvidanya amigos
Translated:
Good job, friends. I would not have done it without your help. Anyway, I got the resources needed for my next hit - you'll love it. Expect to hear from me in the coming days... I'm going to send something to thank you ... Hopefully you can use it. Dasvidanya friends
Note that Dasvidanya is a phonetic transliteration of до свиданья — a Russian phrase for "goodbye". The thing that Sombra sent as a thank you was a new spray, named "Día de Los Muertos" after the Mexican festival that took place at the same time as the ARG. The spray is currently only available on the PC version of the game.
The MISDIRECTION string lead to the MISDIRECTION directory which contained the text:
...Estableciendo conexiуn... ...Protocolo Sombra v2.3 iniciado... ...Desviando datos del zigurat de LumériCo hacia el objetivo... ...Descifrando contraseсas del objetivo... ...Acceso otorgado al directorio de volskayaindustries.com... ...boop ;)... ...Terminando conexión...
Translated:
...Establishing connection... ...Sombra Protocol v2.3 initiated... ...Forwarding the data from the LumériCo ziggurat to the target... ...Deciphering the target passwords... ...Access Granted to the directory of volskayaindustries.com... ...boop ;)... ...Ending connection..
Blizzcon
Blizzcon 2016 opened with the Overwatch short "Infiltration", a short depicting Reaper, Widowmaker, and Sombra on Volskaya Industries. During the showing of the short, Sombra's hero page went live, showcasing her abilities and character backstory.
References
Community Resources
A collection of tools and resources made by the Game Detectives Discord community for use in the ARG.
ASCII Skull
ASCII Skull Analysis: https://github.com/bahamas10/sombra
Removing SOMBR@ Analysis: https://pastebin.com/15u27YTC
ASCII Skull Eye Analysys: https://docs.google.com/spreadsheets/d/1-JQpWyitMKYhP-4l8ZDFiJI3NjqRrvoEnRdFQawike8
Google Docs
Observations and Speculations Spreadsheet: https://docs.google.com/spreadsheets/d/1rI08baFQmAwaqHC-9GF9VNGCYjuRE-q4LN9k4ottjuQ/pubhtml
LumériCo Emails and Translations Spreadsheet: https://goo.gl/cQgdIJ (Courtesy of UberPilot)
Tracer Code
GOL! Guesser: https://axxim.net/ow/gol-guesser/
Uber GOL! Guesser: https://axxim.net/ow/gol-guesser/uber/
The Uber GOL! Guesser only prints out UTF-8 compliant results, which makes it easier to identify potentially correct answers.
Bruteforcing tool: https://github.com/glv2/bruteforce-salted-openssl
Third-Party Resources
A collection of third-party tools and resources that the Game Detectives Discord community has used in the ARG.
Image of Reaper
stegdetect (Linux): https://github.com/abeluck/stegdetect
stegdetect is a Linux utility used to determine if a given image may contain encoded information.
JPHide & JPSeek: https://linux01.gwdg.de/~alatham/stego.html
iSteg (Mac OSX): https://www.hanynet.com/isteg/
JPHide & JPSeek is used to hide and find, respectively, a file inside a JPEG image.
iSteg works similarly to JPHide on the Mac OSX platform.
stegbreak (Linux): https://linux.die.net/man/1/stegbreak
stegbreak is used to do brute-force dictionary attacks on JPEG images.
Easter Eggs
The following are collection of references and Easter Eggs encountered throughout the ARG.
In-Game
Sombra's "Amused" Emote
This character emote features the Skycode, accompanied by soft music resembling the Skysong. Sombra's expression is one of amusement, and it's a nod to the community's prolonged creative attempts to solving an nonexistent puzzle.
Skycode Spray
This character spray features Sombra's iconic skull in front of a compass rose and the Skycode. This is a reference to both the cardinal directions used in one of the puzzles and to the Skycode, which is considered the most significant false lead that solvers encountered.
In-ARG
Espresso Command
There was a hidden command in LumériCo's admin terminal. Inputting the word espresso returned the following message: Coffee Pot Status: Brewed approximately 23 hours ago, currently 0% full
This is referencing a variety of emails found in the LumériCo site involving broken espresso machines and incompetent coffee brewing, which caught the attention of the community and gave way to a vast variety of mediocre jokes. Furthermore, "23 hours" makes reference to the number 23, which was believed by many to possess some sort of significance to the ARG, as Sombra would be the 23rd character in Overwatch. Finally, "0%" references the ARG's notable waiting periods that have been widely criticized by the community, specifically A Moment in Crime's upload percentage.
Due to the iconic purple text it is believed that this hidden command was created by Sombra herself.
Media Appearances
3rd Aug. 2016
[EN] Kotaku - Overwatch Fans Find New Clues About The Mysterious Hero Sombra
[EN] Polygon - Overwatch fans are trying to crack the latest mystery about Sombra
[EN] PCGamesN - Overwatch's Sombra ARG continues with new clues, but no solutions
[EN] Team-Dignitas - Who is Sombra? All facts and clues about Sombra
[FR] Gamewave - UN NOUVEAU CODE CACHÉ DANS LA DERNIÈRE CINÉMATIQUE D'OVERWATCH!
[EN] FollowNews - Overwatch Fans Find New Clues About The Mysterious Hero Sombra
4th Aug. 2016
[EN] PCGamer - Overwatch Summer Games trailer hides a mysterious secret
[SK] Sector - Nové Overwatch video obsahuje ďalšie tajomstvá
[EN] Gamerant - Overwatch Players Uncover More ‘Sombra’ Clues
[HU] Gamestar - Overwatch - újabb nyomok utalnak a még be nem jelentett hősre
5th Aug. 2016
[EN] Kotaku - Days Later, Overwatch Fans Can't Figure Out The 'Sky Code' Mystery
[NL] Gamersnet - Cryptische speurtocht naar Overwatch' nieuwe heldin Sombra gaat bizar diep
[ES] Alfa Beta Jeuga - Overwatch: El enigma de Sombra sigue ofreciendo nuevos detalles
[EN] IGN (Video) - Sombra: Overwatch's Secret New Hero - Overwatch HQ
7th Aug. 2016
[EN] Gamespresso - Summary of the state of sombra's ARG in Overwatch
8th Aug. 2016
[EN/CN] Zhentoo - Overwatch new hero Secret Dorado hidden mystery
[EN] TechNewsToday - Overwatch: Sombra Continues to Elude Detectives
11th Aug. 2016
[EN] The Know - New Overwatch Hero Hints
12th Aug. 2016
[EN] Kotaku - Overwatch Fans' Sombra Investigation Reaps A Skull Code
14th Aug. 2016
[EN] Gamerant - Skull Code is Latest Clue in Overwatch’s Sombra Investigation
16th Aug. 2016
[EN] Christian Today - 'Overwatch' DLC update: Skull Code the latest clue for Sombra investigation
[EN] Yibada - 'Overwatch' DLC update: New clues on Sombra's inclusion to the roster revealed
23rd Aug. 2016
[EN] Tech News Today - Overwatch: All We Know About the Sombra ARG
24th Aug. 2016
[EN] Gamerant - Overwatch Forums Glitch Out, Reveals Hidden Message From Sombra
[EN] Gamerant - New Website Counts Down To Next Clue For Overwatch’s Sombra
[EN] Polygon - Overwatch's Sombra mystery appears to be coming to a close
[EN] VG247 - Overwatch forums glitch out, reveal a message from the mysterious Sombra
[EN] Tech News Today - Sombra Hacks Into Overwatch Forums
[EN] IGN - Overwatch Mystery Character Sombra Could Be Revealed Today
25th Aug. 2016
[EN] Kotaku - Overwatch Players Are Getting Sick Of The Sombra ARG
[EN] IGN - Overwatch Made the Internet Lose its Mind Last Night, And I Had a Front-Row Seat
[EN] Tech News Today - Overwatch: Countdown to Sombra
30th Aug. 2016
[EN] PC Gamer - Overwatch's Sombra riddle begins to irritate the players trying to solve it
3rd Oct. 2016
[EN] Mobile & Apps - Sombra To Be Revealed At Blizzcon? Halloween Event Confirmed In Data Leak
4th Oct. 2016
[EN] iTechPost - Overwatch Update: Are We Finally Getting Sombra?
11th Oct. 2016
[EN] Kotaku - Overwatch Fans Hacked Actual People In An Attempt To Find Sombra
17th Oct. 2016
[EN] TelKom Gaming - Will Sombra Hack Her Way Into BlizzCon 2016?
18th Oct. 2016
[EN] OverwatchTips - Everything You NEED To Know (Sombra ARG)
26th Oct. 2016
[EN] Min Network - Everything we know about Blizzard's rumored Nov. 1 release
28th Oct. 2016
[EN] Kotaku - Imagining Horror Stories Of A Never-Ending Overwatch ARG
1st Nov. 2016
[EN] IGN - Will Sombra be at BlizzCon 2016?
8th Nov. 2016