Difference between revisions of "Bradwell Electronics"
| [unchecked revision] | [checked revision] |
| (47 intermediate revisions by 11 users not shown) | |||
| Line 1: | Line 1: | ||
| + | {{WIP}} | ||
| + | |||
{{argbox | {{argbox | ||
| float = right | | float = right | ||
| name = Bradwell Electronics | | name = Bradwell Electronics | ||
| image = File:Bradwell Logo.png | | image = File:Bradwell Logo.png | ||
| − | |||
| description= Better. Brighter. For everyone. | | description= Better. Brighter. For everyone. | ||
| creator = [http://www.bossastudios.com/ Bossa Studios] | | creator = [http://www.bossastudios.com/ Bossa Studios] | ||
| − | | type = | + | | type = Investigation |
| − | | status = | + | | status = Completed |
| − | | discovered = | + | | discovered = 2017-03-05 |
}} | }} | ||
| − | + | {{ArgHeader}} | |
| − | + | {{backToTop}} | |
| − | |||
| Line 21: | Line 21: | ||
== Email Newsletter == | == Email Newsletter == | ||
| − | + | ''Most of the content in this section is a rehash of [https://www.reddit.com/r/gamedetectives/comments/5x113k/bradwell_electronics_bossa_studios/ this Reddit post] by [https://www.reddit.com/u/blackbat24 /u/blackbat24]; all credit goes to him.'' | |
| + | |||
| + | A field on the [https://www.bradwellelectronics.com/ Bradwell Electronics site] was found which allowed usrs to sign up for an e-mail newsletter. A few minutes after signing up, the following message is sent to your email: | ||
Welcome to Bradwell Electronics - Better. Brighter. For Everyone. | Welcome to Bradwell Electronics - Better. Brighter. For Everyone. | ||
| Line 40: | Line 42: | ||
[[File:Bradwell qr.gif|The image revealed when encoding the Base64 in the text of the "corrupted" email]] | [[File:Bradwell qr.gif|The image revealed when encoding the Base64 in the text of the "corrupted" email]] | ||
| − | ''(Note: Amesbury is the location of Stonehenge | + | ''(Note: Amesbury is the location of Stonehenge.)'' |
Reading the QR code reveals the following string: | Reading the QR code reveals the following string: | ||
| Line 61: | Line 63: | ||
Additionally, the final line of text in the red box is a countdown timer, which is counting down to 12:00 PM UTC, on March 8, 2017. | Additionally, the final line of text in the red box is a countdown timer, which is counting down to 12:00 PM UTC, on March 8, 2017. | ||
| − | |||
== /__FILEDATA.ARCHIVE == | == /__FILEDATA.ARCHIVE == | ||
| Line 83: | Line 84: | ||
</pre> | </pre> | ||
| − | This leads to [https://www.bradwellelectronics.com/__FILEDATA.ARCHIVE/ archive page], which contains a [https://www.bradwellelectronics.com/__FILEDATA.ARCHIVE/Bradwell-Press-Release-07022019.pdf press release] about Bradwell's involvement in the restoration of Stonehenge in 2019, while [https://www.bradwellelectronics.com/__FILEDATA.ARCHIVE/BradwellInternalMemo-060702019.zip the other file] is a passworded zip that has yet to be | + | This leads to [https://www.bradwellelectronics.com/__FILEDATA.ARCHIVE/ archive page], which contains a [https://www.bradwellelectronics.com/__FILEDATA.ARCHIVE/Bradwell-Press-Release-07022019.pdf press release] about Bradwell's involvement in the restoration of Stonehenge in 2019, while [https://www.bradwellelectronics.com/__FILEDATA.ARCHIVE/BradwellInternalMemo-060702019.zip the other file] is a passworded zip. In addition, in order to access other parts of the site, a decryption key is needed to be added in the [https://www.bradwellelectronics.com/wp-content/cache/autoptimize/js/autoptimize_5fb1719442f5f2a9ea5584295800051c.js code] of the website. |
| + | |||
| + | Within the js of the website, [http://pastebin.com/Bsr0FWUW large blocks of hex] was found in the code which, when translated, included the decrypted data that was supposed to show only after the insertion of the decryption key. Just a few minutes later the decryption key (<code>together</code>) was found in the same translated js blob. With the [[#2nd_Key|2nd key]] in hand, users unlocked the subsequent data and followed the instructions, but this still left the zip file encrypted and its content sealed. | ||
| + | |||
| + | [[File:bw1_bookcipher.png|thumbnail|right|The book cipher hidden in the footer of the press release.]] Later that day, a series of numbers in the footer of the [https://www.bradwellelectronics.com/__FILEDATA.ARCHIVE/Bradwell-Press-Release-07022019.pdf press release] was found, which looked like a book cipher. It decoded as <code>w3trusTu</code>, a keyword that unlocked the content of the encrypted zip file. The [https://www.bradwellelectronics.com/__FILEDATA.ARCHIVE/BradwellInternalMemo-060702019.zip internal memo] contains the planned repairs to the A303 tunnel and the Stonehenge museum, but just like the press release it also stored a hidden message, <code>together</code>, the [[#2nd_Key|2nd key]] needed for the advancement. It was later spotted inside the middle diamond, at the end of the footer, in a very small size font, black on black background. | ||
| + | |||
| + | [[File:bw1_together.png|thumbnail|center|The second key, highlighted, hidden in the footer of the 060702019 internal memo.]] | ||
| + | |||
| + | == 2nd Key == | ||
| + | |||
| + | The 2nd key, <code>together</code>, found initially through reverse engineering, when entered into the field produced this output: | ||
| + | |||
| + | <pre> | ||
| + | ##DECRYPTIONKIT############# | ||
| + | ## GRID MINI VM V0.11[ADDRESS REMOVED]## | ||
| + | ################################## | ||
| + | |||
| + | \\>DECR_BRUTE_FORCE << |'fetch grid:[0x424cb726:0xbfe9c31a]/OENQJRYYVHZERCBEG.DAT' | ||
| + | -->BRUTEFORCE NODES STOPPED. | ||
| + | -->BRUTEFORCE DECRYPTION COMPLETED: | ||
| + | ----> ARCHIVE DETECTED (OENQJRYYVHZERCBEG.ARCHIVE) | ||
| + | ----> DECOMPRESSING ARCHIVE... COMPLETED WITH ERRORS: | ||
| + | -------> TOTAL FILES: 10, RECOVERED: 2 | ||
| + | ----> WRAPPING RECOVERED FILES FOR ACCESS: COMPLETED | ||
| + | ----> RECOVERED FILES AVAILABE FOR DOWNLOAD: /__FILEDATA.ARCHIVE/ | ||
| + | -------> ENTER SECONDARY KEY TO DECRYPT REMAINING FILES: ACCEPTED | ||
| + | -->SUBMITTING SECONDARY ENCRYPTION JOB TO GRID SYSTEM: [#####] | ||
| + | ---->DECRYPTION TIME CANNOT BE DETERMINED. | ||
| + | ---->NOTIFICATION ON JOB COMPLETITION AVAILABLE USING SOCIAL MEDIA NETWORKS TO PROTECT ANONYMITY | ||
| + | ------>USE _LINK_ TO POST A TWEET INCLUDING SPECIAL CODE 'BETTERBE2026' | ||
| + | ------>DECRYPTION SYSTEM WILL GET IN TOUCH ONCE JOB HAS BEEN COMPLETED | ||
| + | </pre> | ||
| + | |||
| + | [https://twitter.com/intent/tweet?text=Fresh%20air%20is%20good%20for%20you.%20BETTERBE2026 The link] is a tweet template which says <code>Fresh air is good for you. BETTERBE2026</code>. | ||
| + | After several hours the message was modified, now reading: | ||
| + | |||
| + | <pre> | ||
| + | -->SUBMITTING SECONDARY ENCRYPTION JOB TO GRID SYSTEM: [#####] | ||
| + | ---->DECRYPTION TIME CANNOT BE DETERMINED. | ||
| + | ---->USURPING SOCIAL MEDIA BANDWIDTH TO DECREASE DATA DECRYPTION TIME | ||
| + | ------>_REGISTER_ NODE WITH SYSTEM TO RECEIVE DECRYPTED PACKAGE | ||
| + | ------>DECRYPTED PACKAGE WILL BE DISTRIBUTED TO REGISTERED NODES ON COMPLETION | ||
| + | </pre> | ||
| + | |||
| + | The [https://twitter.com/intent/tweet?text=%40BetterBradwell%20%23BETTERBE2026 REGISTER link] is a different tweet template, now reading <code>@BetterBradwell #BETTERBE2026</code>. It is yet unclear whether the alteration is a different step, or if it has simply being reworded (now reading <code>USURPING SOCIAL MEDIA BANDWIDTH TO DECREASE DATA DECRYPTION TIME</code>) to better instruct the players to tweet the message more. | ||
| + | |||
| + | On March 16, around 15:40 UTC (3:40 pm), users starting receiving mentions. | ||
| + | |||
| + | <pre>@username SEC TRIED TO SLOW US. DECRYPTION PRGRSS. | ||
| + | [######----] 63%. STANDBY</pre> | ||
| + | |||
| + | 3 minutes later, [https://twitter.com/BetterBradwell/ Bradwell Electronics] [https://twitter.com/BetterBradwell/status/842401632319111170 tweeted]: | ||
| + | |||
| + | <pre>Please accept our apologies if you recently received a direct tweet. The intruder has been suppressed and our systems have been updated.</pre> | ||
| + | |||
| + | This could mean that no more tweets will be sent out, and that the updates will appear directly on the _FILEDATA in roughly a week time. | ||
| + | |||
| + | = Bradwell Returns = | ||
| + | |||
| + | At 15:00 UTC on 2018-08-29, the [https://twitter.com/bossastudios Bossa Studios] Twitter account posted a [https://twitter.com/bossastudios/status/1034802858221174785 tweet] which said: | ||
| + | <pre> | ||
| + | PLEASE HELP!! I’m a technician at Bradwell Electronics and have made some important discoveries which need to be brought to light! I’ve managed to hack into the company’s social accounts, but think I’m being watched… Gotta go, but I’ll be back shortly! | ||
| + | </pre> | ||
| + | |||
| + | This tweet was followed by three more tweets at two hour intervals, which can be seen below: | ||
| + | |||
| + | * https://twitter.com/bossastudios/status/1034833061047877632 | ||
| + | |||
| + | <pre> | ||
| + | You’ve been led to believe that Bradwell Electronics is a kind and altruistic organisation. It’s not! There are thousands of incriminating files but I can’t access the drives internally, as my cover could be compromised. Hold on, I’m gonna try something... | ||
| + | </pre> | ||
| + | |||
| + | * https://twitter.com/bossastudios/status/1034863254672224257 | ||
| + | |||
| + | <pre> | ||
| + | Phew, that was a close one. A security guard just walked past, so I had to abandon the attempt. One false move and it’s game over. People are counting on me for this information all around the world, and they don’t even know it! About to try again... | ||
| + | </pre> | ||
| + | |||
| + | * https://twitter.com/bossastudios/status/1034893454533382144 | ||
| + | |||
| + | <pre> | ||
| + | Ok, so that didn’t work. I tried accessing the docs by bouncing my connection off an external node but no use. I’m going to have to access a senior staff member’s computer, but how? Wish me luck - we’re all going to need it. | ||
| + | </pre> | ||
| + | |||
| + | This signaled to players that the ARG may be starting up again. This led players back to the [https://www.bradwellelectronics.com/ Bradwell Electronics website]. Players who signed up for the newsletter again received a new email, which can be seen [https://pastebin.com/UAnarEMH here], and appeared to be an uncorrupted version of the email received previously in the ARG. In addition, the metadata of the new email contained the full text of the old, corrupted email. | ||
| + | |||
| + | More tweets were released, which seemed to be building up to a reveal of some sorts: | ||
| + | |||
| + | * https://twitter.com/bossastudios/status/1034923656592465920 | ||
| + | |||
| + | <pre> | ||
| + | Good news - I’m on my way to one of the technician’s offices! I “accidentally” spilt coffee on them at lunch and managed to swipe their key card in the confusion. They’ve popped to the toilets to change but won’t be long. Now might be my only chance! | ||
| + | </pre> | ||
| + | |||
| + | * https://twitter.com/bossastudios/status/1034953848576561152 | ||
| + | |||
| + | <pre> | ||
| + | Success! He’d left his computer unlocked, and I managed to download a file off the internal drives and get out before they returned. It won’t be long before he realises his key card’s missing though, and suspects I’m the reason. Time’s running out! | ||
| + | </pre> | ||
| + | After this tweet, two hour interval has been changed. | ||
| + | |||
| + | * https://twitter.com/bossastudios/status/1034999145403056129 | ||
| + | |||
| + | <pre> | ||
| + | It’s all here, and worse than I ever suspected. | ||
| + | The only way this will get past the internal firewall is if I disguise the information within Bradwell Electronic’s ridiculous recruitment video! Ok… I’m going to need to get creative here. | ||
| + | Stay vigilant, I’ll post again soon! | ||
| + | </pre> | ||
| + | |||
| + | * https://twitter.com/bossastudios/status/1035059546647977984 | ||
| + | |||
| + | <pre> | ||
| + | Ok, progress is slow but I’m nearly there. I’ve managed to sneak some footage into the video but that's all I’ve got time for. Security seems to be on high alert, and it’s only a matter of time until they find me. | ||
| + | </pre> | ||
| + | |||
| + | * https://twitter.com/bossastudios/status/1035135043453243393 | ||
| + | |||
| + | <pre> | ||
| + | My next post will be my last. They know it’s me, and are searching the facility as we speak! | ||
| + | I’m uploading the video now and then you’ll finally learn what’s REALLY happening at Bradwell Electronics. | ||
| + | I don’t know what will happen to me, but at least the truth will be out... | ||
| + | </pre> | ||
| + | |||
| + | Then, at 3:00 PM UTC, Bossa tweeted again with the release of [https://www.youtube.com/watch?v=Gt3TcKn51cM/ the teaser trailer] for a new game, called [https://store.steampowered.com/app/421790/The_Bradwell_Conspiracy/ The Bradwell Conspiracy] : | ||
| + | |||
| + | <pre> | ||
| + | IMP. ALERT: Yesterday, our social platforms were compromised but we’ve since taken back control. | ||
| + | |||
| + | In completely unrelated news 😏... we’re proud to announce our BRAND NEW TITLE, developed by A Brave Plan; The Bradwell Conspiracy. | ||
| + | |||
| + | Check out the trailer! | ||
| + | </pre> | ||
| + | |||
| + | = The Bradwell Conspiracy = | ||
| + | |||
| + | [[File:DiningHall.PNG|thumbnail|right|A snapshot of the dining area from the trailer.]] | ||
| + | |||
| + | The trailer for the game is disguised as a recruitment video that lasts 45 seconds long. Per the infiltrator's promises, the video has been corrupted at many points throughout. Some of the corruptions show parts of the unrealeased game: A digger excavating at [https://youtu.be/Gt3TcKn51cM?t=15/ 0:15], a luggage searching area at [https://youtu.be/Gt3TcKn51cM?t=16/ 0:16], a meeting room at [https://youtu.be/Gt3TcKn51cM?t=18/ 0:18], a dining area at [https://youtu.be/Gt3TcKn51cM?t=20/ 0:20], and an open hallway at [https://youtu.be/Gt3TcKn51cM?t=21/ 0:21]. All other distortions affect the colours and words of the video (e.g inverting the colour scheme of the video on some frames, and changing the words "bradwell electronics" into "brdawlel elketbomcs" at [https://youtu.be/Gt3TcKn51cM?t=28/ 0:29]). | ||
| + | |||
| + | With the release of the trailer, [https://www.bradwellelectronics.com/ The Bradwell Electronics page] was significantly overhauled. The website was now the host to all information regarding Bradwell Electronics, including the products they offer, recent news, the senior members of the company, and what the company is doing to help sustain the planet's future. | ||
| + | |||
| + | A particularly important page of the website is a contacts page. This contains a phone number: +443300431835,and also contains an email address: [email protected]. The email is not real (or not registered yet) and causes and error email to be sent by google. | ||
| + | |||
| + | However, the phone number does work, and plays the following transcript: | ||
| + | |||
| + | <pre> | ||
| + | Hello, and thank you for calling Bradwell Electronics. Better, Brighter, For Everyone. | ||
| + | |||
| + | To speak to a product sales representive, press 1. | ||
| + | To reach a customer support agent, press 2. | ||
| + | To leave us a message, press 3. | ||
| + | For more information about our products and services, please visit us at www.bradwellelectronics.com. | ||
| + | You may also email us at [email protected] | ||
| + | To repeat this message, press 9. | ||
| + | </pre> | ||
| + | |||
| + | Pressing 1 or 2 gives the same response: | ||
| + | |||
| + | <pre> | ||
| + | All our agents are extremely busy at the moment. Please press 1 to leave a message, and we will get back to you as soon as we can. | ||
| + | </pre> | ||
| + | |||
| + | It is unclear whether leaving messages will have any effect on the ARG. | ||
| + | |||
| + | However, there is more to the voicemail than meets the eye. | ||
| + | Pressing * will reveal a secret response: | ||
| + | |||
| + | <pre> | ||
| + | This is the Bradwell Electornics Security Services Secondary Authentication System. Please type in the request code: | ||
| + | </pre> | ||
| + | |||
| + | The code is of an unknown length, and has not been discovered yet. It is unknown whether the code can be figured out now, or whether we must wait for more clues to be given out. | ||
| + | |||
| + | A recording of the number can be found [https://clyp.it/jqwxjdu3/ here]. | ||
| + | |||
| + | [https://www.thebradwellconspiracy.com/ Another website] was also created specifically for the game and the actual real life people that have worked on it. ''This website should not contain any clues related to the progression of the ARG.'' | ||
| + | = EGX 2018 = | ||
| + | The game featured at EGX2018 between 20th-23rd September at The NEC in Birmingham. There was a showcase of the game, and the game could be played by any member of the public. | ||
| + | As part of the advertising of the game, a branded Bradwell water bottle was given to those who went to the showcase. | ||
| + | [[File:Qr_code.PNG|thumb|150x150px| QR code located on bottle]] | ||
| + | [[File:Barcode.png|thumb| Barcode located on bottle(heavily edited)]] | ||
| + | |||
| + | The bottle contained 2 items of interest: A QR code and a barcode. | ||
| + | |||
| + | The QR code, when read, directed the user to the [https://www.bradwellelectronics.com/about/ about] page of the Bradwell website. | ||
| + | |||
| + | The Barcode (after much editing and trial and error), when read, says "Bradwell RnD". | ||
| + | |||
| + | When these 2 pieces of info are combined, they direct to a specific paragraph on the about page: | ||
| + | |||
| + | <pre> | ||
| + | 1995 | ||
| + | |||
| + | Bradwell R&D is created as a separate company by Eliza Bradwell (previously Winters). | ||
| + | Focusing on researching new technology, Eliza always believed that complacency was not an option for Bradwell Electronics. | ||
| + | </pre> | ||
| + | |||
| + | Immediately below this is a one character link that takes you to a [https://www.bradwellelectronics.com/int@docnode@access/ login screen]. | ||
| − | + | It asks for a login and a password. Until 10/17/2018, this was not solved. | |
| + | |||
| + | = Discovery of Bradwellium = | ||
| + | |||
| + | However, eventually, the correct login was input, and within a few minutes, so was the password. | ||
| + | |||
| + | Through trial and error of using the first initial and full last name, the login <code> gmcnamara </code> was discovered. | ||
| + | Eventually, after enough incorrect passwords were inputted, a hint for the password was given: | ||
| + | <code> Clarke #3 </code> | ||
| + | This is a reference to the most famous of [https://en.wikipedia.org/wiki/Clarke%27s_three_laws Clarke's three laws]: | ||
<pre> | <pre> | ||
| − | + | Any sufficiently advanced technology is indistinguishable from magic. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
</pre> | </pre> | ||
| − | + | This turned out to be the password, and the account of gmcnamara was unlocked. | |
| + | |||
| + | Upon logging in, using the help command will list all available commands: | ||
| + | * ls to list files | ||
| + | * status to display the status of the current node | ||
| + | * retr to retrieve documents by id | ||
| + | * dbg to debug documents | ||
| + | |||
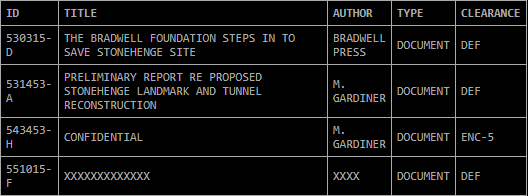
| + | using ls lists 4 documents: | ||
| + | [[File:FileTable.png]] | ||
| + | |||
| + | All of the documents can be found [https://drive.google.com/open?id=10WpkjGoXUJeAj6N597kzxxybb8SGOndw here]. | ||
| + | |||
| + | The first 2 PDFs can be accessed by just using the retr command. | ||
| + | |||
| + | The zip requires a code from the "SECONDARY AUTHENTICATION MECHANISM". Using the code given (<code>9415</code>) in the Secondary Authentication System on the Bradwell Electronics Phone Number, another code(<code>AF52426544</code>) is given that can be used to open the document. | ||
| + | |||
| + | The final document requires the use of the dbg command. It requires 10 hashes to be decoded, 2 already given. | ||
| + | |||
| + | It was initially unknown how to get these hashes. However, it was soon discovered that each person logged into the account was connected to 1 of 5 nodes, with each node giving 2 different hashes. | ||
| + | |||
| + | After every node was accounted for, the final command to unlock the document was: | ||
| + | <code> | ||
| + | |||
| + | dbg 551015-F | ||
| + | 1:0x3402ACFFF6F46C1 | ||
| + | |||
| + | 2:0x4DA26D081BCE2E4 | ||
| + | |||
| + | 3:0x2377EDC8FF102E5 | ||
| + | |||
| + | 4:0xC29892DD64FF9FB | ||
| + | |||
| + | 5:0xD1459C410C0414C | ||
| + | |||
| + | 6:0x83B81ADA185DD16 | ||
| + | |||
| + | 7:0x37FA9E245F80974 | ||
| + | |||
| + | 8:0x183FA457D40B32B | ||
| + | |||
| + | 9:0x496AA953CB3FCF1 | ||
| + | |||
| + | 10:0x2A337C4BE5F304D | ||
| + | |||
| + | </code> | ||
| + | |||
| + | The First PDF seems to take the form of a press release about Bradwell Electronics stepping in to save Stonehenge. | ||
| + | |||
| + | The Second PDF is a confidential analysis on said Stonehenge Museum repair. | ||
| + | |||
| + | The ZIP contains 2 audio recordings of test results and lists the field report of 03/25/18 | ||
| + | |||
| + | Finally, the Final PDF contains an analysis on said test results. This is the most significant of all the documents, as it implies the discovery of the element that is mentioned in the promo video, "Bradwellium". This may also be a key plot point for the game's release. | ||
Latest revision as of 23:39, 22 July 2024
| This page is a work in progress and will be updated as new developments emerge. If you have information you think should be added, please create an account to enable page edits or contact a Wiki Editor. |
| Bradwell Electronics | |
|---|---|
| Better. Brighter. For everyone. | |
| Type | Investigation |
| Creator | Bossa Studios |
| Discovered | 2017-03-05 |
Main Page > List of Investigations > Bradwell Electronics
Bradwell Electronics is a promotional website released by Bossa Studios, a British game developer responsible for Surgeon Simulator and I Am Bread. At this time, the purpose of the site is unknown, but it is speculated to be an in-fiction promotional website for Bossa Studios' next game.
Contents
Email Newsletter
Most of the content in this section is a rehash of this Reddit post by /u/blackbat24; all credit goes to him.
A field on the Bradwell Electronics site was found which allowed usrs to sign up for an e-mail newsletter. A few minutes after signing up, the following message is sent to your email:
Welcome to Bradwell Electronics - Better. Brighter. For Everyone. Thank you for registering your interest for the upcoming relaunch of the Bradwell Electronics website. When John Bradwell founded Bradwell Electronics over 62 years ago in 1964, he never imagined that the family business would become one of the most recognized brands worldwi$"%"$"!£2/.&%...
From this point onwards, the message is "corrupted", and is mostly comprised of Base64 ciphertext. For the full text of the email, check this Reddit post. At one point, the message becomes legible again:
>>INTERRUPT STREAM ----------This is a mayday alert. --------------------It is of concern to all of us. ------------------------------We ask you to trust us. ----------------------------------------We cannot do this alone. << END OF INTERRUPT
Encoding the Base64 in the text of the email yields an image which includes a QR code:
(Note: Amesbury is the location of Stonehenge.)
Reading the QR code reveals the following string:
/?decrypt50726f6a65637441
(Note: 50726f6a65637441 is hexadecimal for ProjectA, but this is not yet relevant to the investigation.)
Countdown Timer
Appending /?decrypt50726f6a65637441 to the http://bradwellelectronics.com URL reveals a red box (link), containing this text:
\\>DECR_BRUTE_FORCE << |'fetch grid:[0x424cb726:0xbfe9c31a]/OENQJRYYVHZERCBEG.DAT' -->BRUTEFORCE NODES RUNNING... -->ESTIMATED BRUTEFORCE DECRYPTION COMPLETED IN: _d __h __m __s
The first line of the text contains the string OENQJRYYVHZERCBEG; this can be deciphered using ROT13 to obtain BRADWELLIUMREPORT. The significance of this is currently unknown.
Additionally, the final line of text in the red box is a countdown timer, which is counting down to 12:00 PM UTC, on March 8, 2017.
/__FILEDATA.ARCHIVE
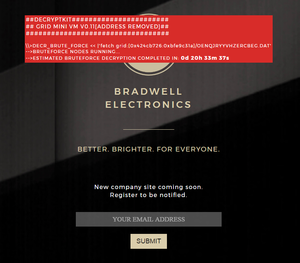
On March 8, 2017, the text on the login page of "Decryptkit" changed:
##DECRYPTIONKIT############# ## GRID MINI VM V0.11[ADDRESS REMOVED]## ################################## \\>DECR_BRUTE_FORCE << |'fetch grid:[0x424cb726:0xbfe9c31a]/OENQJRYYVHZERCBEG.DAT' -->BRUTEFORCE NODES STOPPED. -->BRUTEFORCE DECRYPTION COMPLETED: ----> ARCHIVE DETECTED (OENQJRYYVHZERCBEG.ARCHIVE) ----> DECOMPRESSING ARCHIVE... COMPLETED WITH ERRORS: -------> TOTAL FILES: 10, RECOVERED: 2 ----> WRAPPING RECOVERED FILES FOR ACCESS: COMPLETED ----> RECOVERED FILES AVAILABE FOR DOWNLOAD: /__FILEDATA.ARCHIVE/ -------> ENTER SECONDARY KEY TO DECRYPT REMAINING FILES:
This leads to archive page, which contains a press release about Bradwell's involvement in the restoration of Stonehenge in 2019, while the other file is a passworded zip. In addition, in order to access other parts of the site, a decryption key is needed to be added in the code of the website.
Within the js of the website, large blocks of hex was found in the code which, when translated, included the decrypted data that was supposed to show only after the insertion of the decryption key. Just a few minutes later the decryption key (together) was found in the same translated js blob. With the 2nd key in hand, users unlocked the subsequent data and followed the instructions, but this still left the zip file encrypted and its content sealed.
w3trusTu, a keyword that unlocked the content of the encrypted zip file. The internal memo contains the planned repairs to the A303 tunnel and the Stonehenge museum, but just like the press release it also stored a hidden message, together, the 2nd key needed for the advancement. It was later spotted inside the middle diamond, at the end of the footer, in a very small size font, black on black background.
2nd Key
The 2nd key, together, found initially through reverse engineering, when entered into the field produced this output:
##DECRYPTIONKIT############# ## GRID MINI VM V0.11[ADDRESS REMOVED]## ################################## \\>DECR_BRUTE_FORCE << |'fetch grid:[0x424cb726:0xbfe9c31a]/OENQJRYYVHZERCBEG.DAT' -->BRUTEFORCE NODES STOPPED. -->BRUTEFORCE DECRYPTION COMPLETED: ----> ARCHIVE DETECTED (OENQJRYYVHZERCBEG.ARCHIVE) ----> DECOMPRESSING ARCHIVE... COMPLETED WITH ERRORS: -------> TOTAL FILES: 10, RECOVERED: 2 ----> WRAPPING RECOVERED FILES FOR ACCESS: COMPLETED ----> RECOVERED FILES AVAILABE FOR DOWNLOAD: /__FILEDATA.ARCHIVE/ -------> ENTER SECONDARY KEY TO DECRYPT REMAINING FILES: ACCEPTED -->SUBMITTING SECONDARY ENCRYPTION JOB TO GRID SYSTEM: [#####] ---->DECRYPTION TIME CANNOT BE DETERMINED. ---->NOTIFICATION ON JOB COMPLETITION AVAILABLE USING SOCIAL MEDIA NETWORKS TO PROTECT ANONYMITY ------>USE _LINK_ TO POST A TWEET INCLUDING SPECIAL CODE 'BETTERBE2026' ------>DECRYPTION SYSTEM WILL GET IN TOUCH ONCE JOB HAS BEEN COMPLETED
The link is a tweet template which says Fresh air is good for you. BETTERBE2026.
After several hours the message was modified, now reading:
-->SUBMITTING SECONDARY ENCRYPTION JOB TO GRID SYSTEM: [#####] ---->DECRYPTION TIME CANNOT BE DETERMINED. ---->USURPING SOCIAL MEDIA BANDWIDTH TO DECREASE DATA DECRYPTION TIME ------>_REGISTER_ NODE WITH SYSTEM TO RECEIVE DECRYPTED PACKAGE ------>DECRYPTED PACKAGE WILL BE DISTRIBUTED TO REGISTERED NODES ON COMPLETION
The REGISTER link is a different tweet template, now reading @BetterBradwell #BETTERBE2026. It is yet unclear whether the alteration is a different step, or if it has simply being reworded (now reading USURPING SOCIAL MEDIA BANDWIDTH TO DECREASE DATA DECRYPTION TIME) to better instruct the players to tweet the message more.
On March 16, around 15:40 UTC (3:40 pm), users starting receiving mentions.
@username SEC TRIED TO SLOW US. DECRYPTION PRGRSS. [######----] 63%. STANDBY
3 minutes later, Bradwell Electronics tweeted:
Please accept our apologies if you recently received a direct tweet. The intruder has been suppressed and our systems have been updated.
This could mean that no more tweets will be sent out, and that the updates will appear directly on the _FILEDATA in roughly a week time.
Bradwell Returns
At 15:00 UTC on 2018-08-29, the Bossa Studios Twitter account posted a tweet which said:
PLEASE HELP!! I’m a technician at Bradwell Electronics and have made some important discoveries which need to be brought to light! I’ve managed to hack into the company’s social accounts, but think I’m being watched… Gotta go, but I’ll be back shortly!
This tweet was followed by three more tweets at two hour intervals, which can be seen below:
You’ve been led to believe that Bradwell Electronics is a kind and altruistic organisation. It’s not! There are thousands of incriminating files but I can’t access the drives internally, as my cover could be compromised. Hold on, I’m gonna try something...
Phew, that was a close one. A security guard just walked past, so I had to abandon the attempt. One false move and it’s game over. People are counting on me for this information all around the world, and they don’t even know it! About to try again...
Ok, so that didn’t work. I tried accessing the docs by bouncing my connection off an external node but no use. I’m going to have to access a senior staff member’s computer, but how? Wish me luck - we’re all going to need it.
This signaled to players that the ARG may be starting up again. This led players back to the Bradwell Electronics website. Players who signed up for the newsletter again received a new email, which can be seen here, and appeared to be an uncorrupted version of the email received previously in the ARG. In addition, the metadata of the new email contained the full text of the old, corrupted email.
More tweets were released, which seemed to be building up to a reveal of some sorts:
Good news - I’m on my way to one of the technician’s offices! I “accidentally” spilt coffee on them at lunch and managed to swipe their key card in the confusion. They’ve popped to the toilets to change but won’t be long. Now might be my only chance!
Success! He’d left his computer unlocked, and I managed to download a file off the internal drives and get out before they returned. It won’t be long before he realises his key card’s missing though, and suspects I’m the reason. Time’s running out!
After this tweet, two hour interval has been changed.
It’s all here, and worse than I ever suspected. The only way this will get past the internal firewall is if I disguise the information within Bradwell Electronic’s ridiculous recruitment video! Ok… I’m going to need to get creative here. Stay vigilant, I’ll post again soon!
Ok, progress is slow but I’m nearly there. I’ve managed to sneak some footage into the video but that's all I’ve got time for. Security seems to be on high alert, and it’s only a matter of time until they find me.
My next post will be my last. They know it’s me, and are searching the facility as we speak! I’m uploading the video now and then you’ll finally learn what’s REALLY happening at Bradwell Electronics. I don’t know what will happen to me, but at least the truth will be out...
Then, at 3:00 PM UTC, Bossa tweeted again with the release of the teaser trailer for a new game, called The Bradwell Conspiracy :
IMP. ALERT: Yesterday, our social platforms were compromised but we’ve since taken back control. In completely unrelated news 😏... we’re proud to announce our BRAND NEW TITLE, developed by A Brave Plan; The Bradwell Conspiracy. Check out the trailer!
The Bradwell Conspiracy
The trailer for the game is disguised as a recruitment video that lasts 45 seconds long. Per the infiltrator's promises, the video has been corrupted at many points throughout. Some of the corruptions show parts of the unrealeased game: A digger excavating at 0:15, a luggage searching area at 0:16, a meeting room at 0:18, a dining area at 0:20, and an open hallway at 0:21. All other distortions affect the colours and words of the video (e.g inverting the colour scheme of the video on some frames, and changing the words "bradwell electronics" into "brdawlel elketbomcs" at 0:29).
With the release of the trailer, The Bradwell Electronics page was significantly overhauled. The website was now the host to all information regarding Bradwell Electronics, including the products they offer, recent news, the senior members of the company, and what the company is doing to help sustain the planet's future.
A particularly important page of the website is a contacts page. This contains a phone number: +443300431835,and also contains an email address: [email protected]. The email is not real (or not registered yet) and causes and error email to be sent by google.
However, the phone number does work, and plays the following transcript:
Hello, and thank you for calling Bradwell Electronics. Better, Brighter, For Everyone. To speak to a product sales representive, press 1. To reach a customer support agent, press 2. To leave us a message, press 3. For more information about our products and services, please visit us at www.bradwellelectronics.com. You may also email us at [email protected] To repeat this message, press 9.
Pressing 1 or 2 gives the same response:
All our agents are extremely busy at the moment. Please press 1 to leave a message, and we will get back to you as soon as we can.
It is unclear whether leaving messages will have any effect on the ARG.
However, there is more to the voicemail than meets the eye. Pressing * will reveal a secret response:
This is the Bradwell Electornics Security Services Secondary Authentication System. Please type in the request code:
The code is of an unknown length, and has not been discovered yet. It is unknown whether the code can be figured out now, or whether we must wait for more clues to be given out.
A recording of the number can be found here.
Another website was also created specifically for the game and the actual real life people that have worked on it. This website should not contain any clues related to the progression of the ARG.
EGX 2018
The game featured at EGX2018 between 20th-23rd September at The NEC in Birmingham. There was a showcase of the game, and the game could be played by any member of the public. As part of the advertising of the game, a branded Bradwell water bottle was given to those who went to the showcase.
The bottle contained 2 items of interest: A QR code and a barcode.
The QR code, when read, directed the user to the about page of the Bradwell website.
The Barcode (after much editing and trial and error), when read, says "Bradwell RnD".
When these 2 pieces of info are combined, they direct to a specific paragraph on the about page:
1995 Bradwell R&D is created as a separate company by Eliza Bradwell (previously Winters). Focusing on researching new technology, Eliza always believed that complacency was not an option for Bradwell Electronics.
Immediately below this is a one character link that takes you to a login screen.
It asks for a login and a password. Until 10/17/2018, this was not solved.
Discovery of Bradwellium
However, eventually, the correct login was input, and within a few minutes, so was the password.
Through trial and error of using the first initial and full last name, the login gmcnamara was discovered.
Eventually, after enough incorrect passwords were inputted, a hint for the password was given:
Clarke #3
This is a reference to the most famous of Clarke's three laws:
Any sufficiently advanced technology is indistinguishable from magic.
This turned out to be the password, and the account of gmcnamara was unlocked.
Upon logging in, using the help command will list all available commands:
- ls to list files
- status to display the status of the current node
- retr to retrieve documents by id
- dbg to debug documents
All of the documents can be found here.
The first 2 PDFs can be accessed by just using the retr command.
The zip requires a code from the "SECONDARY AUTHENTICATION MECHANISM". Using the code given (9415) in the Secondary Authentication System on the Bradwell Electronics Phone Number, another code(AF52426544) is given that can be used to open the document.
The final document requires the use of the dbg command. It requires 10 hashes to be decoded, 2 already given.
It was initially unknown how to get these hashes. However, it was soon discovered that each person logged into the account was connected to 1 of 5 nodes, with each node giving 2 different hashes.
After every node was accounted for, the final command to unlock the document was:
dbg 551015-F 1:0x3402ACFFF6F46C1
2:0x4DA26D081BCE2E4
3:0x2377EDC8FF102E5
4:0xC29892DD64FF9FB
5:0xD1459C410C0414C
6:0x83B81ADA185DD16
7:0x37FA9E245F80974
8:0x183FA457D40B32B
9:0x496AA953CB3FCF1
10:0x2A337C4BE5F304D
The First PDF seems to take the form of a press release about Bradwell Electronics stepping in to save Stonehenge.
The Second PDF is a confidential analysis on said Stonehenge Museum repair.
The ZIP contains 2 audio recordings of test results and lists the field report of 03/25/18
Finally, the Final PDF contains an analysis on said test results. This is the most significant of all the documents, as it implies the discovery of the element that is mentioned in the promo video, "Bradwellium". This may also be a key plot point for the game's release.