Difference between revisions of "Sombra ARG"
| [unchecked revision] | [unchecked revision] |
m (12 days to Sept 5th) |
(→Derivative Works: Unkown Fusion's Youtube video edition) |
||
| Line 556: | Line 556: | ||
|- | |- | ||
| Trap rendition of the skysong || SnerK || Sombra || [https://soundcloud.com/itssnerk/sombra SoundCloud] | | Trap rendition of the skysong || SnerK || Sombra || [https://soundcloud.com/itssnerk/sombra SoundCloud] | ||
| + | |- | ||
| + | | Youtube video with pieces of ARG and SnerK's Trap Skysong || Unknown Fusion || Snerk - Sombra || [https://www.youtube.com/watch?v=VQPe-WFE--0 YouTube] | ||
|- | |- | ||
| Youtube skit on the initial stall || Goose Boose || Sombra ARG in a Nutshell || [https://www.youtube.com/watch?v=b8SY_xDwtUE YouTube] | | Youtube skit on the initial stall || Goose Boose || Sombra ARG in a Nutshell || [https://www.youtube.com/watch?v=b8SY_xDwtUE YouTube] | ||
Revision as of 20:06, 30 August 2016
| Sombra ARG | |
|---|---|
| The Sombra ARG - an ARG involving an unreleased Overwatch hero. | |
| Type | [[List_of_Investigations#Official|Official]] |
| Creator | Blizzard |
| Discovered | 06-12-2016 |
Main Page > List of Investigations
The Sombra ARG is an ARG involving Overwatch, a game made by Blizzard. Sombra is the name of an unreleased Overwatch hero that has been hinted at by Blizzard as being an upcoming playable character. Clues and ciphers referencing Sombra were found in various developer updates and short animations released by Blizzard, and this ARG is comprised of those clues.
At the game's release, there were numerous pieces of in-game information that appeared in Dorado, hinting at a character called Sombra. When Ana was revealed as Overwatch’s newest character, more Sombra clues appeared in Ana's origin video. In the weeks that followed, more clues were discovered.
Contents
Ana Videos
Ana Origin Video
On July 12, 2016, a video for the new Overwatch hero named Ana was released. By pausing the video at the 1:16 time mark, a bunch of hexadecimal numbers were discovered:
2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 64 78 7A 75
A simple Hex to ASCII translation gave us
...{v fbr c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...{v fbr c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...{v fbr c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...{v fbr
c~ryr {v ~yqxezvt~Ô¤y, c~ryr r{ gxsre...dxzu
Using an XOR Cipher with the constant 23 on the above text, we got
..la que tiene la información; tiene el poder...la que tiene la información; tiene el poder...la que tiene la información; tiene el poder...la que tiene la información; tiene el poder...somb
The Spanish translates to
She who has the information, has the power...
A second frame of hexadecimal numbers was discovered at the 2:11 time mark of the video:
65 76 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E 7B 76 20 66 62 72 20 63 7E 72 79 72 20 7B 76 20 7E 79 71 78 65 7A 76 74 7E D4 A4 79 2C 20 63 7E 72 79 72 20 72 7B 20 67 78 73 72 65 2E 2E 2E
When put through the same process, the same string of Spanish was revealed, but with the letters ra at the start. These letters were combined with somb from the other cipher to create sombra, the name of an unreleased hero that has been hinted at by Blizzard in the past. This led us to believe that this ARG was related to Sombra. The ARG was named accordingly, and no more clues were discovered until the release of the Dev Update video.
Dev Update Video
At the end of this video, a series of vertical barcodes were discovered. The barcodes were found to be binary, a dump of which is available here, credit of redditor /u/zapu.
Turning the ones and zeroes into black and white pixels, which formed a QR code:
Scanning this QR code yielded the following message:
"¿Estuvo eso facilito? Ahora que tengo su atención, déjenme se las pongo más difícil."
And translated from Sombra's native language of Spanish into English:
Was that easy? Well, now that I have your attention, allow me to make things much more difficult.
After this, no more clues were discovered until the Summer Games video was released.
Welcome to the Summer Games Video
On August 2, another cipher was discovered in this video - this time, the ciphertext was in base64:
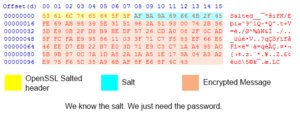
U2FsdGVkX1+vupppZksvRf5pq5g5XjFRIipRkwB0K1Y96Qsv2L m+31cmzaAILwytX/z66ZVWEQM/ccf1g+9m5Ubu1+sit+A9cenD xxqkIaxbm4cMeh2oKhqIHhdaBKOi6XX2XDWpa6+P5o9MQw==
Using a tool to decode the Base64 results in the following output:
Salted__���ifK/E�i��9^1Q�*Q�t+V=�
/ع��W/
�_����V��?q����f�F���"��=q�������[��
z��*����Z����u�\5�k�C
(Note: copy/pasting this string will not work; some of the characters will not paste properly)
Decrypting the Encryption
The "Salted__" header at the start of the string indicates that the remainder of the text is encoded in an OpenSSL cipher, which requires a key and a known cipher. Salts are added to encrypted data to ensure uniqueness.
Since we know the salt, and we know the input data, all we need to decrypt is the password and cipher method. Since OpenSSL has been around for ages, there are many different cipher methods.
A Cipher is a mathematical algorithm to convert data into unreadable binary data.
A Password is key to the box, if you know it you can easily decrypt the data.
Narrowing Down Ciphers
The Cipher used has been narrowed down by looking at a Hex Dump of the encrypted string. There are two major types of ciphers, stream ciphers and block ciphers. Stream ciphers encrypt only the data fed into them, whereas block ciphers will always be a set chunk length.
A byte is roughly a single character, but special characters can take up multiple bytes. We know that OpenSSL Salted Encryption uses the first 8 bytes of the output for Salted__ and the next 8 bytes for the actual salt. The rest of the information is the encrypted message.
The immediately interesting thing here is that the encrypted message data stops 3 bytes short of a full chunk. This is a excellent indicator that the cipher used is a stream cipher (or a block cipher in CTR/OFB/CFB mode). This narrows our cipher list down significantly. This also means that the final string that Blizzard encrypted is less than 93 bytes!
At the time of writing, this cipher remains unsolved; it's speculated that Blizzard moved us past the cipher by giving us hints.
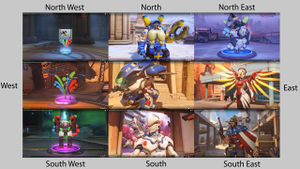
Directions & Letters
There are references to directions that are present in the North American version of the video. These references are conspicuously absent from other versions of the trailer. These references are shown below, with the relevant heroes and timestamps:
Directions
Here are the screencaps, arranged according to their directions.
Dorado Photo
On the Overwatch media page, a new photo of the attacking spawn in Dorado was added. This photo was "datamoshed", which means it concealed a hidden message while also taking on a distorted appearance. (Here is an example of purposely data moshing the image manually to achieve similar effects)
After comparing the images via difference checking tools, it was found that certain English and Spanish characters were replaced with exclamation points, producing a Spanish sentence out of the replaced characters.
"Por que estan mirando al cielo? La respuesta no esta sobre sus cabezas, esta detras de ustedes. A veces, necesitan analizar sus logros previos."
Translated into English, this phrase is
"Why are you looking at the sky? The answer isn't over your heads, it's behind you. Sometimes, you need to analyze your previous achievements."
The phrase "Why are you looking at the sky?" is most likely a reference to a strange artifact that was discovered in the sky of the Dorado map, but various processes of decryption were fruitless.
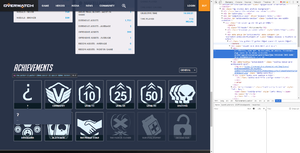
Analyzing Achievements
The phrase "you need to analyze your previous achievements" led us to look at the achievements on the Play Overwatch Website. We noticed that if you logged in and viewed the achievements on your player profile, a mystery achievement appeared. Viewing the source code of the image lead us to a new phrase:
Vientos, nada mal. No obstante, me aburro. Intentemos algo nuevo en la misma dirección. uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 IS8208O913KRlrx
Translated, it says:
Damn, not bad. However, I'm getting bored. Let's try something new in the same direction. uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 IS8208O913KRlrx
Volskaya Datamosh
The following instructions explain the process of how the ASCII Skull and "little games" quote were found:
1. Take the following section of code from the "?" achievement hint above.
uczihriwgsxorxwunaarawryqhbrsfmeqrjjmu 5552E494 78T3 4VM9 OPL6 IS8208O913KRlrx
2. Run it through a Vigenére Cipher
3. Use heroes in the order of their positions on the compass (further above) to get hero names for the passphrase:
tracertorbjornwinstonsymmetradvamercybastiongenjimccree
4. The code received will result in the following url which, when formatted in to a proper URL, becomes the following picture:
blzgdapiproaakamaihdnetmediascreenshot 5552E494 78B3 4CE9 ACF6 EF8208F913CFjpg blzgdapipro-a.akamaihd.net/media/screenshot/5552E494-78B3-4CE9-ACF6-EF8208F913CF.jpg
The distortion on this picture indicates that it, too, is "datamoshed", and that it conceals hidden information. A difference check between the new and original image resulted in an interesting message.
ASCII Skull #1
The diff from the datamosh resulted in the following output:
Parece que te gustan estos jueguitos... por que no jugamos uno de verdad?
:PB@Bk:
,jB@@B@B@B@BBL.
7G@B@B@BMMMMMB@B@B@Nr
:kB@B@@@MMOMOMOMOMMMM@B@B@B1,
:5@B@B@B@BBMMOMOMOMOMOMOMM@@@B@B@BBu.
70@@@B@B@B@BXBBOMOMOMOMOMOMMBMPB@B@B@B@B@Nr
G@@@BJ iB@B@@ OBMOMOMOMOMOMOM@2 B@B@B. EB@B@S
@@BM@GJBU. iSuB@OMOMOMOMOMOMM@OU1: .kBLM@M@B@
B@MMB@B 7@BBMMOMOMOMOMOBB@: B@BMM@B
@@@B@B 7@@@MMOMOMOMM@B@: @@B@B@
@@OLB. BNB@MMOMOMM@BEB rBjM@B
@@ @ M OBOMOMM@q M .@ @@
@@OvB B:u@MMOMOMMBJiB .BvM@B
@B@B@J 0@B@MMOMOMOMB@B@u q@@@B@
B@MBB@v G@@BMMMMMMMMMMMBB@5 F@BMM@B
@BBM@BPNi LMEB@OMMMM@B@MMOMM@BZM7 rEqB@MBB@
B@@@BM B@B@B qBMOMB@B@B@BMOMBL B@B@B @B@B@M
J@@@@PB@B@B@B7G@OMBB. ,@MMM@qLB@B@@@BqB@BBv
iGB@,i0@M@B@MMO@E : M@OMM@@@B@Pii@@N:
. B@M@B@MMM@B@B@B@MMM@@@M@B
@[email protected]@MBB@B@B@@BM@::B@B@
B@@@ .B@B.:@B@ :B@B @B@O
:0 r@B@ B@@ .@B@: P:
vMB :@B@ :BO7
,B@B
Translation:
"It seems you like these little games... Why don't we play a real one?"
This is the python2 script to extract modified bytes from datamoshed volskaya screenshot, https://gist.github.com/synap5e/27635d2ff6f0e3b15f0c902dca2974a9
The ASCII image of the skull seemed to be a dead end, however, as no further progress was made until August 23rd.
Overwatch Forums Glitching Page/ "Skycoder"
A user named 'Skycoder' posted an ominous topic on the official Overwatch forums.
The name of the topic, if translated from binary, says "23"; a reference to Sombra, who is the 23rd character in Overwatch. The time posted on the forums was set at 23h and had since been counting down rather than increasing; it was assumed to be a countdown to something (see below).
This topic's page soon begins to glitch and distort, turning a hue of purple before opening a text box stating:
"la que tiene la información; tiene el poder" "She who has the information, has the power"
and typing another code:
ICAgICAgICAgICAgICAgICAgICAgICAgICA6UEKPQms6CiAgICAgICAg ICAgICAgICAgICAgICAsakKIQEJAQkBCQEJCTC4KICAgICAgICAgICAg ICAgICAgIDdHlkKTQpVCTU1NTU1CQEJAQkBOcgogICAgICAgICAgICAg ICA6a0KSQpCIl01NT01PTU9NT01NTU2MQphCQEIxLAogICAgICAgICAg IDo1kUKNQphCiEJCTU1PTU9NT01PTU9NT01NipJuQm5CQEJCdS4KICAg ICAgICA3MG6GlUKIQpJClEJYQkJPTU9NT01PTU9NT01NQk1QQphCiEJA QkBCQE5yCiAgICAgIEeYlpdCSiBpQohCh4ggIE9CTU9NT01PTU9NT01P TZYyICBCj0JAQi4gRUJAQkBTCiAgICAgIJKWQk2HR0pCVS4gIGlTdUKI T01PTU9NT01PTU9NTZdPVTE6ICAua0JMTYhNhkKXCiAgICAgIEKMTU1C mUIgICAgICAgN4hCQk1NT01PTU9NT01PQkKWOiAgICAgICBCh0JNTYhC CiAgICAgII2YiEKKQiAgICAgICAgIDeSlkBNTU9NT01PTU1AQkA6ICAg ICAgICAgQEBCQEJACiAgICAgII+ST0xCLiAgICAgICAgICBCTkKPTU1P TU9NTY9CRUIgICAgICAgICAgckJqTYRCCiAgICAgIJBAICBAICAgICAg ICAgICBNICBPQk9NT01NQHEgIE0gICAgICAgICAgLkAgIEBACiAgICAg IISVT3ZCICAgICAgICAgICBCOnWMTU1PTU9NTUJKaUIgICAgICAgICAg LkJ2TUBCCiAgICAgIIRCkUKYSiAgICAgICAgIDCRQpdNTU9NT01PTUKV QkB1ICAgICAgICAgcUBAQEJACiAgICAgIEKETUJCjHYgICAgICAgR4+L Qk1NTU1NTU1NTU1NQkKINSAgICAgICBGhEJNTUBCCiAgICAgIIdCQk1/ QlBOaSAgIExNRUKFT01NTU2PQoNNTU9NTYpCWk03ICAgckVxQodNQkKE CiAgICAgIEKYloRCTSAgQm1ChEIgIHFCTU9NQpBChUKEQk1PTUJMICBC QEJAQiAgQEJAQkBNCiAgICAgICBKlm2GhFBCj0KEQplCN0eIT01CQi4g ICAsQE1NTUBxTEJAQkBAQEJxQkBCQnYKICAgICAgICAgIGlHQpUsaTCE TZZCbk1NT4tFICA6ICBNQE9NTUBAQEJAUGlpQEBOOgogICAgICAgICAg ICAgLiAgIEKXTZBCj01NTUBCQEJAQkBNTU1AQEBNQEIKICAgICAgICAg ICAgICAgICBAQkBCLmlATUJCQEJAQkBAQk1AOjpCQEJACiAgICAgICAg ICAgICAgICAgQkBAQCAuQkBCLjpAQkAgOkJAQiAgQEJATwogICAgICAg ICAgICAgICAgICAgOjAgckBCQCAgQkBAIC5AQkA6IFA6CiAgICAgICAg ICAgICAgICAgICAgICAgdk1CIDpAQkAgOkJPNwogICAgICAgICAgICAg ICAgICAgICAgICAgICAsQkBCCg==
ASCII Skull #2
The code was recognized to be Base64, which was then translated to a new ASCII image:
:PB.Bk:
,jBˆ@B@B@B@BBL.
7G–B“B•BMMMMMB@B@B@Nr
:kB’B.ˆ—MMOMOMOMOMMMMŒB˜B@B1,
:5‘B.B˜BˆBBMMOMOMOMOMOMOMMŠ’nBnB@BBu.
70n†•BˆB’B”BXBBOMOMOMOMOMOMMBMPB˜BˆB@B@B@Nr
G˜–—BJ iBˆB‡ˆ OBMOMOMOMOMOMOM–2 B.B@B. EB@B@S
’–BM‡GJBU. iSuBˆOMOMOMOMOMOMM—OU1: .kBLMˆM†B—
BŒMMB™B 7ˆBBMMOMOMOMOMOBB–: B‡BMMˆB
.˜ˆBŠB 7’–@MMOMOMOMM@B@: @@B@B@
.’OLB. BNB.MMOMOMM.BEB rBjM„B
.@ @ M OBOMOMM@q M .@ @@
„•OvB B:uŒMMOMOMMBJiB .BvM@B
„B‘B˜J 0‘B—MMOMOMOMB•B@u q@@@B@
B„MBBŒv G.‹BMMMMMMMMMMMBBˆ5 F„BMM@B
‡BBM.BPNi LMEB…OMMMM.BƒMMOMMŠBZM7 rEqB‡MBB„
B˜–„BM BmB„B qBMOMB.B…B„BMOMBL B@B@B @B@B@M
J–m†„PB.B„B™B7GˆOMBB. ,@MMM@qLB@B@@@BqB@BBv
iGB•,i0„M–BnMMO‹E : M@OMM@@@B@Pii@@N:
. B—M.B.MMM@B@B@B@MMM@@@M@B
@[email protected]@MBB@B@B@@BM@::B@B@
B@@@ .B@B.:@B@ :B@B @B@O
:0 r@B@ B@@ .@B@: P:
vMB :@B@ :BO7
,B@B
It should be noted that the skull above shouldn't be used to decode anything, just that it's a skull. Characters do not copy the same for some people due to character sets being different. Instead, a much simpler method is going to be used to achieve this.
First, you must strip both skulls of spaces, and new characters. You can do this in Notepad++ or any semi-advanced text editor. The strings cannot be shown due to their length, but the idea is to have them be on a single line with no spaces.
The process to get something out of these 2 strings is to subtract each byte from both skulls, and showing the ones that are not 0. A person by the user @Ely#3743 on our Discord has given me a script made in C to automate this hosted on this Pastebin. You can compile it and read the source to get an understanding of what you need.
After subtracting each byte from both skulls, you end up with this string:
OHVSURPHWLXQMXHJR...FUHRTXHXVWHGHVORVGHWHFWLYHVGHMXHJRVOROODPDULDQXQWUDLOKHDG?EOCJGDXVD-DPEDV-FDODYHUDV.KWPO
This string was recognized as a Caesar Cipher. After shifting it 23 places, it resulted in:
LESPROMETIUNJUEGO...CREOQUEUSTEDESLOSDETECTIVESDEJUEGOSLOLLAMARIANUNTRAILHEAD?BLZGDAUSA-AMBAS-CALAVERAS.HTML
Alternative method to arrive at a similar string to the above, verified by Discord user Per
Decoding the Base64 string, extracting all of the non-UTF-8 characters, and subtracting 0x23 from the value of each character yields:
lesprometiunjuegocreoqueustedeslosdetectivesdejuegoslollamarianuntrailheadblzgdausaambascalaverashtml
This process is similar to a Ceaser Cipher, so it is arguable that either one of the methods could have been intended.
When cleaned up and translated, the message reads:
Les prometi un juego...creo que ustedes los Detectives de Juegos lo llamarían un trailhead? BLZGDUSA-AMBAS-CALAVERAS.HTML I promised you a game...I believe you Game Detectives would call it a trailhead? BLZGDAUSA-AMBAS-CALAVERAS.HTML
"USA-AMBAS-CALAVERAS" translates to "USE-BOTH-SKULLS".
With that said, you may also notice "BLZGDAUSA-AMBAS-CALVERAS.HTML" is familiar looking. It was assumed there is a page on their CDN that contained more information, in the Skull Video section, you can see that it was true.
Skull Video
BLZGDA is Blizzard's server for hosting media, using full URL we get:
https://blzgdapipro-a.akamaihd.net/media/screenshot/usa-ambas-calaveras.html
This link leads to a video which clearly shows an image of a skull, along with a dossier of info:

In the video properties you can find:
Parecen estar muy interesados en estos "héroes". ¿Tal vez les interese conocer algunos detallitos que he averiguado sobre ellos? You seem to be very interested in these "heroes". Maybe interested to know some details that I found out about them?
There is also a heartbeat monitor in the video - by looking at which lines it "pings" on, and by assigning letters to these lines, we get:
momentincrime
amomentincrime E-mail
'momentincrime' appeared to refer to the Roadhog and Junkrat video A Moment in Crime, which came out months before the release of Overwatch. A site: amomentincrime.com was also found, where you can find information about configuration made to automatic mail response:
...Estableciendo conexión... ...Protocolo Sombra v1.3 iniciado... ...Infiltrando la respuesta automática del email de pistas... ...Terminando conexión...
It was discovered that sending an e-mail to [email protected] resulted in an automated response via email:
Thank you for contacting A Moment in Crime's anonymous crime line! We have analyzed your submission and forwarded the information to the relevant parties. Your help could be vital in apprehending these cri ...Estableciendo conexión... ...Protocolo Sombra v1.7 iniciado... 01:07:47 02:02:02 01:08:06 02:13:43 01:18:32 01:18:21 02:10:19 01:06:21 02:05:18 01:04:02 01:07:08 02:18:25 01:13:04 02:19:20 01:23:02 01:16:40 02:16:35 01:23:04 02:17:16 01:06:42 01:13:29 02:18:06 01:05:02 02:15:41 01:08:34 j.7F57O,NLv:qj.7B:,1qv@B1j5ivB:, ...Terminando conexión... minals and bringing them to justice. These fugitives are responsible for a string of robberies, arson, and other crimes stretching from Sydney to King's Row. Authorities believe that they have set their sights on crossing the Atlantic to America.
If the timestamp-looking numbers are taken as AA:BB:CC, where AA is the number of skull, BB is the row and CC is the column (as illustrated here), the 5x5 table would look like this:
S j G B L . @ M O k i , v : 0 E 7 r q N J P 5 F 1
(although, note that these symbols are the same in both skulls).
If this is used as the key for the Bifid cipher for the string below the table:
j . 7 F 5 7 O , N L v : q j . 7 B : , 1 q v @ B 1 j 5 i v B : , 12 21 42 54 53 42 24 32 45 15 33 34 44 12 21 42 14 34 32 55 44 33 22 14 55 12 53 31 33 14 34 32 1 2 2 1 4 2 5 4 5 3 4 2 2 4 3 2 4 5 1 5 3 3 3 4 4 4 1 2 2 1 4 2 1 4 3 4 3 2 5 5 4 4 3 3 2 2 1 4 5 5 1 2 5 3 3 1 3 3 1 4 3 4 3 2 11 24 23 14 43 22 55 45 54 34 43 23 22 42 31 24 45 55 11 52 35 33 33 41 43 43 11 24 23 14 43 22
SOMBr@1NF:rM@7iON1SP0vvErrSOMBr@
This phrase is leet-speak, when translated, it becomes
Sombra Information is power Sombra
Meanwhile, the countdown on the Blizzard forum post approached zero...
A Moment in Crime Transmission
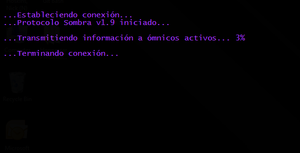
Once the countdown on the Skycoder forum post reached zero, amomentincrime.com was updated. It now says (same colours as were in the forum post)
...Estableciendo conexión... ...Protocolo Sombra v1.9 iniciado... ...Transmitiendo información a ómnicos activos... 2% ...Terminando conexión...
Translating the text on the page becomes:
...Establishing connection... ...Sombra Protocol v1.9 initiated... ...Transmitting information to active omnics... 2% ...Ending connection...
A comment was added in the source code:
Bien hecho, ya tienen mi clave. Hackear este programa de televisión no tuvo chiste. Espérense a lo que sigue. Well done, you have my password. Hacking this television program was meaningless. Wait for what is coming.
Due to confusions during translation, "no tuvo chiste" does directly translate to "You did not joke." But after asking someone who speaks Mexican Spanish, the phrase was clarified to mean "there was no point in it." There are more translation confusions that do not properly convey the tone of the message. Originally, it was "Hacking this television program was meaningless. Wait for what follows." The tone of that though was seemingly trying to show off what she will do. It should be noted that she also implied hacking the television program was easy.
The percent number on the amomentincrime.com seems to be going up slowly. Note that it's not updating for everybody at the same time, probably due to the caching tech employed for the amomentincrime.com.
There is an uncached version of the website discovered by Discord user "Mino" that can be found here.
Over time the percentage rose, and the Sombra Protocol version number went to v1.95 after 5% was hit. Since then the percentage increases by 0.0038 every 3 minutes. It is predicted that this will reach 100% on Oct. 16th-17th, a good few days before BlizzCon on Nov 4th - 5th. Alternatively the % will hit 23, an important Sombra number, on September 5th, when Season 2 starts.
Another comment was added to the source code as well:
Parece que se están calentando un poco las cosas... tendré que pasar desapercibida mientras esto se finaliza. It seems that things are are warming up a little... gotta go unnoticed while it completes.
As of Aug. 27th @ 7:0654 sec PST the percentage number has stopped increasing. As of Aug. 27th @ 12:44 09 sec PST the percentage number has started increasing again.
Image of Reaper
The Sombra-ARG Discord server created a datamoshed image as a message to Sombra, and popular Overwatch YouTuber Muselk sent the image to @PlayOverwatch. An Imgur version of this image can be found here.
The base image for the datamosh that was sent can be seen here.
Discord user 'LazyGamer' was able to obtain an original uncompressed copy of the datamosh we sent to Blizzard from Sombra-ARG Discord user 'tece', allowing us to reverse engineer and confirm the message that we sent.
The message was as follows:
Bueno Sombra, jugemos un juegito y depaso nos das algo con que jugar Okay Sombra, let's play a little game and in return you can give us something to play with
A more in depth history of the message we sent can be found in this Imgur gallery.
We received no response from Sombra until a post by Skycoder appeared on the US Battle.net forums. During the destruction of the website itself, you can see an image fly around on the page. This image appeared on the forum post a few hours after the post originally appeared, and many have chalked this up to a mistake on Blizzard's part. This image depicts Reaper on Temple of Anubis, and is quite similar to the image that Muselk sent to Sombra via twitter, although it does appear to have immediately noticeable differences. Namely, the file size is much bigger and there is a visible shift of the image to the left towards the bottom of the image.
Discord user 'jsha' explained to the investigative group that it's impossible to interpret the response image as a diff-based datamosh, due to the larger size, the missing unmoshed version and the clear re-encoding of the image. He went on to say that optional RST markers present in the response are enough to determine that the image was re-encoded after it was moshed, eliminating the possibility to reconstruct the pre-encoded response.
The idea that this is not a datamosh is not surprising, as Twitter and Imgur image compression would make it impossible for Sombra to decode our message, not to mention that Blizzard has already used datamoshing techniques twice during the course of this ARG.
Additional attempts have been made by Discord users 'LazyGamer', 'Per' and others to interpret the response as a steganographic transmission, and the JPEG data was scoured using tools to determine if any files had been hidden. No usable data from the image has been found.
Discord user 'DelBliss' is attempting to fix the response by manipulating MCUs in the image with a hex editor. Further details can be found here.
References
Community Resources
A collection of tools and resources made by the Game Detectives Discord community for use in the ARG.
ASCII Skull
ASCII Skull Analysis: https://github.com/bahamas10/sombra
Removing SOMBR@ Analysis: http://pastebin.com/15u27YTC
ASCII Skull Eye Analysys: https://docs.google.com/spreadsheets/d/1-JQpWyitMKYhP-4l8ZDFiJI3NjqRrvoEnRdFQawike8
Google Docs
Observations and Speculations Spreadsheet: https://docs.google.com/spreadsheets/d/1rI08baFQmAwaqHC-9GF9VNGCYjuRE-q4LN9k4ottjuQ/pubhtml
Tracer Code
GOL! Guesser: http://axxim.net/ow/gol-guesser/
Uber GOL! Guesser: http://axxim.net/ow/gol-guesser/uber/
The Uber GOL! Guesser only prints out UTF-8 compliant results, which makes it easier to identify potentially correct answers.
Bruteforcing tool: https://github.com/glv2/bruteforce-salted-openssl
Third-Party Resources
A collection of third-party tools and resources that the Game Detectives Discord community has used in the ARG.
Image of Reaper
stegdetect (Linux): https://github.com/abeluck/stegdetect
stegdetect is a Linux utility used to determine if a given image may contain encoded information.
JPHide & JPSeek: http://linux01.gwdg.de/~alatham/stego.html
iSteg (Mac OSX): http://www.hanynet.com/isteg/
JPHide & JPSeek is used to hide and find, respectively, a file inside a JPEG image.
iSteg works similarly to JPHide on the Mac OSX platform.
stegbreak (Linux): http://linux.die.net/man/1/stegbreak
stegbreak is used to do brute-force dictionary attacks on JPEG images.
Old / False Leads
Click here for all of the false leads that the community came across while trying to solve the Sombra ARG!
Derivative Works
The long road to solving the ARG have sparked several people into creating pieces of media as a joke or just as a spark of creativity. Most notably is the skysong; the misinterpreted skycode that had been interpreted as a piece of music by Gingerware. The following derivate works have been inspired by this.
| Description | Author | Title | Work |
|---|---|---|---|
| Original thread on how the OP thought the skycode was music | Gingerware | Skysong | SoundCloud (Notable examples "Ordered 60 Upsidedown Loop", "Skysong 120 tempo looped" and Sombra Skysong - Overwatch) |
| Trap rendition of the skysong | SnerK | Sombra | SoundCloud |
| Youtube video with pieces of ARG and SnerK's Trap Skysong | Unknown Fusion | Snerk - Sombra | YouTube |
| Youtube skit on the initial stall | Goose Boose | Sombra ARG in a Nutshell | YouTube |
| An opensource android app to keep up with the Sombra ARG. | Jasona99 and CyanogenBot | Sombra Checker | GitHub (Download the .apk file in the root folder for the compiled app) |
| Fanart using the skull and skycode | Pocketomi | Sombra Interpretation | 
|
| Sombra fanart | Pocketomi | Booty Queen | DeviantArt |
| Sombra fanart | Pocketomi | Sombra x Athena | DeviantArt |
| Sombra fanart with mask as focus | Pocketomi | Mask | DeviantArt |
| Sombra 4K wallpaper | Palas | Wallpaper | DeviantArt |
| Fanart | Orroko | Sombra on Dorado | DeviantArt |
| Fanart | Orroko | Sombra 2.0 | DeviantArt |
| Fanart | Sadhira | Sombra Uncloaked | DeviantArt |
| Fanart | Laken | Interpretation | |
| Twitch overlay for OBS Studio | Akihabara | GD Twitch overlay | Mega |
Media Appearances
3rd Aug. 2016
[EN] Kotaku - Overwatch Fans Find New Clues About The Mysterious Hero Sombra
[EN] Polygon - Overwatch fans are trying to crack the latest mystery about Sombra
[EN] PCGamesN - Overwatch's Sombra ARG continues with new clues, but no solutions
[EN] Team-Dignitas - Who is Sombra? All facts and clues about Sombra
[FR] Gamewave - UN NOUVEAU CODE CACHÉ DANS LA DERNIÈRE CINÉMATIQUE D'OVERWATCH!
[EN] FollowNews - Overwatch Fans Find New Clues About The Mysterious Hero Sombra
4th Aug. 2016
[EN] PCGamer - Overwatch Summer Games trailer hides a mysterious secret
[SK] Sector - Nové Overwatch video obsahuje ďalšie tajomstvá
[EN] Gamerant - Overwatch Players Uncover More ‘Sombra’ Clues
[HU] Gamestar - Overwatch - újabb nyomok utalnak a még be nem jelentett hősre
5th Aug. 2016
[EN] Kotaku - Days Later, Overwatch Fans Can't Figure Out The 'Sky Code' Mystery
[NL] Gamersnet - Cryptische speurtocht naar Overwatch' nieuwe heldin Sombra gaat bizar diep
[ES] Alfa Beta Jeuga - Overwatch: El enigma de Sombra sigue ofreciendo nuevos detalles
[EN] IGN (Video) - Sombra: Overwatch's Secret New Hero - Overwatch HQ
7th Aug. 2016
[EN] Gamespresso - Summary of the state of sombra's ARG in Overwatch
8th Aug. 2016
[EN/CN] Zhentoo - Overwatch new hero Secret Dorado hidden mystery
[EN] TechNewsToday - Overwatch: Sombra Continues to Elude Detectives
11th Aug. 2016
[EN] The Know - New Overwatch Hero Hints
12th Aug. 2016
[EN] Kotaku - Overwatch Fans' Sombra Investigation Reaps A Skull Code
14th Aug. 2016
[EN] Gamerant - Skull Code is Latest Clue in Overwatch’s Sombra Investigation
16th Aug. 2016
[EN] Christian Today - 'Overwatch' DLC update: Skull Code the latest clue for Sombra investigation
[EN] Yibada - 'Overwatch' DLC update: New clues on Sombra's inclusion to the roster revealed
23rd Aug. 2016
[EN] Tech News Today - Overwatch: All We Know About the Sombra ARG
24th Aug. 2016
[EN] Gamerant - Overwatch Forums Glitch Out, Reveals Hidden Message From Sombra
[EN] Gamerant - New Website Counts Down To Next Clue For Overwatch’s Sombra
[EN] Polygon - Overwatch's Sombra mystery appears to be coming to a close
[EN] VG247 - Overwatch forums glitch out, reveal a message from the mysterious Sombra
[EN] Tech News Today - Sombra Hacks Into Overwatch Forums
[EN] IGN - Overwatch Mystery Character Sombra Could Be Revealed Today
25th Aug. 2016
[EN] Kotaku - Overwatch Players Are Getting Sick Of The Sombra ARG
[EN] IGN - Overwatch Made the Internet Lose its Mind Last Night, And I Had a Front-Row Seat