Difference between revisions of "Cyberpunk 2077"
| [checked revision] | [pending revision] |
m (→Case 00032 05 54 0B CP) |
|||
| (119 intermediate revisions by 23 users not shown) | |||
| Line 3: | Line 3: | ||
| name = Cyberpunk 2077 | | name = Cyberpunk 2077 | ||
| image = Image:CP2077.png | | image = Image:CP2077.png | ||
| − | | imagewidth = | + | | imagewidth = 500 |
| − | | description = Cyberpunk 2077 | + | | description = A hacker at E3 2018 exposed a live website linked to upcoming release Cyberpunk 2077. |
| − | | creator = [http://en.cdprojektred.com/ CD | + | | creator = [http://en.cdprojektred.com/ CD PROJEKT RED] |
| type = Official | | type = Official | ||
| status = Active | | status = Active | ||
| − | | discovered = 2018-10 | + | | discovered = 2018-06-10 |
}} | }} | ||
{{ArgHeader}} | {{ArgHeader}} | ||
| + | {{backToTop}} | ||
| + | |||
| + | '''Cyberpunk 2077''' is a story-driven, open world RPG set in a dark future from [http://en.cdprojektred.com/ CD PROJEKT RED] (CDPR), creators of ''The Witcher'' series of games. As the release of Cyberpunk 2077 drew closer, CDPR began trickling hidden messages and puzzles to the community. The ARG is comprised of these puzzles, and quick solvers are often rewarded with Cyberpunk merchandise. | ||
__TOC__ | __TOC__ | ||
| + | <br /><br /><br /> | ||
| + | {{#evt: | ||
| + | service=youtube | ||
| + | |id=https://youtu.be/SxSKxtfBRZ4 | ||
| + | |dimensions=400 | ||
| + | |alignment=right | ||
| + | |description=A "hacker" infiltrates Microsoft's E3 2018 presentation. | ||
| + | |container=frame | ||
| + | }} | ||
| + | |||
| + | = 2018 = | ||
| + | |||
| + | == E3 Presentation == | ||
| + | |||
| + | During Microsoft's E3 2018 presentation slot on June 10th, [https://youtu.be/SxSKxtfBRZ4 a "hacker" interrupted the speaker], ultimately revealing [https://www.youtube.com/watch?v=8X2kIfS6fb8&has_verified=1 a trailer for Cyberpunk 2077]. Players immediately noticed some valuable info during the trailer, including GOG codes which were redeemable for games and, most notably, an IP address, <code>212.91.11.20</code>. | ||
| + | |||
| + | === Quadra === | ||
| + | [[Image:CP77-QUADRA.png|thumb|300px|right|The IP address led to a server with a password prompt.]] | ||
| + | |||
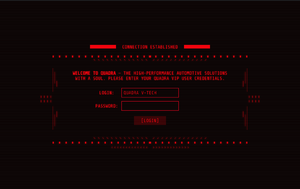
| + | Players quickly realized that the IP resolved to [https://www.cyberpunk.net/en/quadra/ a section of CDPR's Cyberpunk 2077 website], where [https://wiki.gamedetectives.net/images/7/75/CP77-QUADRA.png a password prompt was found] along with a welcome message. The message read as follows: | ||
| + | <pre> | ||
| + | WELCOME TO QUADRA - THE HIGH-PERFORMANCE AUTOMOTIVE SOLUTIONS | ||
| + | WITH A SOUL. PLEASE ENTER YOUR QUADRA VIP USER CREDENTIALS. | ||
| + | </pre> | ||
| + | The login field is force-filled to <code>QUADRA V-TECH</code>, which players connected to [https://youtu.be/Ho7PBdVZrY0?t=145 a license plate number from the trailer], <code>NC20 CP77</code>, which turned out to be the correct password. Only a very small pool of players were [https://wiki.gamedetectives.net/images/d/d9/CP77-Success.png allowed through], and were met with a field to enter their email address. Soon after, the site began to display a message indicating a [https://wiki.gamedetectives.net/images/1/1c/CP77-Quota.png quota had been reached] and that no more emails would be collected. | ||
| + | |||
| + | === Quota Met === | ||
| + | |||
| + | [[Image:CP77-Quota.png|thumb|300px|left|Message which greeted players when the password was entered after the quota was filled.]] | ||
| + | |||
| + | [[Image:CP77-ASCII.png|thumb|300px|left|ASCII-art output of the SSH server.]] | ||
| + | [[Image:CP2077-tshirt.png|thumb|200px|right|Art printed on the back of the t-shirts received by players who made the QUADRA cutoff.]] | ||
| + | |||
| + | Suspecting an ARG was building, players rummaged through the site and other related media. A [http://secure.cyberpunk.net/ a "secure" subdomain] was found, along with a [https://www.cyberpunk.net/en/news/20891/e3schedule-inf "E3 Schedule" file]. RTSP is set up on the site, which players suspected might indicate future intent. Players discovered the site had an SSH server on the same host, which outputs [https://wiki.gamedetectives.net/images/d/d5/CP77-ASCII.png an ASCII-art message]. The other output, <code>Permission denied (publickey)</code>, indicated a private key was be needed to access the server. | ||
| + | |||
| + | Players also uncovered more potential leads in the trailer, including [https://wiki.gamedetectives.net/images/0/0a/CP77-SSH.png lines of debug output from OpenSSH], [https://wiki.gamedetectives.net/images/e/e9/CP77-Barcode.jpg barcodes], [https://wiki.gamedetectives.net/images/9/9f/CP77-PDf417-2.png PDF417 codes], and several messages (usually on screens in the video), [https://wiki.gamedetectives.net/images/e/ed/CP77-Teaser.png including one] which points toward the QUADRA website. | ||
| + | |||
| + | <pre> | ||
| + | ... 10/11/2078 THE FOLLOWING WILL APPLY TO ALL | ||
| + | |||
| + | PROFILES ON DATA ALT//0 463.0983.890.3 | ||
| + | DOMAIN-PUBLIC RESTRICTION REF. 192.8930.610.10 | ||
| + | |||
| + | PUBLIC DATA PRESENTATION WILL TAKE PLACE ON MONDAY AT 12PM GMT+09 ON ALL DOMAINS. SERVER CAPABILITIES ARE ESTIMATED TO SUSTAIN 90% REGISTERED | ||
| + | USERS// | ||
| + | |||
| + | P2-OS CORPORATION, ALL RIGHTS RESERVED | ||
| + | </pre> | ||
| + | |||
| + | Developers indicated [https://wiki.gamedetectives.net/images/0/02/CP77-Dev1.jpg in multiple messages via Discord] that players should wait for more information. | ||
| + | |||
| + | Several [https://www.reddit.com/r/cyberpunkgame/comments/8qty5r/just_got_a_reply_from_quadra_for_the_password/ users on Reddit] who entered the password prior to the quota being met received emails from CDPR in the style of [https://i.imgur.com/Wel7Use.jpg emails from QUADRA automotive], which request logistic and personal information from the player in order to deliver them a care package. | ||
| + | |||
| + | Players who made the QUADRA cutoff received a [https://imgur.com/a/ccIB2Cg care package]. It contained a CP2077 Quadra styled t-shirt in a QUADRA box. The art on the back of the t-shirt was mysterious, but players found no leads despite heavy analysis. | ||
| + | |||
| + | == Trauma Team == | ||
| + | |||
| + | On August 22, the ARG sparked up again when CDPR posted [https://twitter.com/CyberpunkGame/status/1032285684810371074 concept art on their Twitter]. One of the pieces of [https://wiki.gamedetectives.net/images/e/ed/CP2077_bitly1.jpg concept art] contained [http://bit.ly/2kxfbfb a bit.ly link] in the background: | ||
| + | |||
| + | [[Image:CP2077_bitly1.jpg|1000px|center|Concept art which was edited by CDPR to contain a bit.ly link (check out the top-right of the image).]] | ||
| + | |||
| + | This link led to [https://wiki.gamedetectives.net/images/a/ad/CP2077-First.png a first image]. Opening that image in a text editor revealed a hidden message, after a long chunk of encoded text, which read <code>Cesar said: oaawz://jku-s-tra.jkwyvqlraylk.jvt/pthnl/zljvuk.qwn</code>. Using a 19 shift ROT, a link to a [https://wiki.gamedetectives.net/images/e/ea/CP2077-Second.jpg a second image] was revealed. Players connected the phrase <code>TT</code> in the second image to a known CDPR-owned domain, the [https://trauma-team-international.com/ Trauma Team International website]. | ||
| + | |||
| + | [[Image:CP2077-TT_success.png|thumb|300px|left|Screen seen by "winners" of the OrderID Trauma Team phase.]] | ||
| + | |||
| + | === Need Insurance? === | ||
| + | |||
| + | [[Image:CP2077-grille.png|thumb|200px|right|The tshirt art combined with the image attached to the TT winners' email as a grille cipher.]] | ||
| + | |||
| + | After accessing the website, players were met with a bot named David asking for an ID in order to talk to him. Further investigation revealed that the numbers from the [https://wiki.gamedetectives.net/images/a/ad/CP2077-First.png first image] gave the Login ID <code>0374337573334</code> for [https://trauma-team-international.com/ Trauma Team International]. | ||
| + | |||
| + | Once logged in, David allowed players to "buy insurance" through Trauma Team. After doing so, each player was given a unique 10 character code, and David prompted these players to use their codes in the My Orders section of the site. After a specific amount of codes were given out, the bot went offline. The code was deciphered using ASCII85 (Z85 (ZeroMQ) variant), giving the ID <code>#ID00000</code> which was usable in the My Orders section. | ||
| + | |||
| + | Players who made the cutoff were prompted to input their emails. Upon entering their emails, they were greeted with [https://wiki.gamedetectives.net/images/a/ad/CP2077-TT_success.png this image], pictured left, informing them that the process would take up to 7 days and thanking them for participating. After a certain amount of codes were used, the My Orders page went offline with the message "Connection failed," concluding this part of the ARG. | ||
| + | |||
| + | [[Image:CP2077-FrameAfterGameplayStream.png|thumb|400px|left|Frame hidden after gameplay stream.]] | ||
| + | |||
| + | === Your Life is worth it! === | ||
| + | |||
| + | On August 26th 2018, four days after players ripped through the [https://trauma-team-international.com/ Trauma Team International] site, players who got through the cutoff received an [https://wiki.gamedetectives.net/images/c/ce/CP2077-TTEmail.png email] from a Trauma Team International Representative prompting them to reply with their address. The email had two attachments, a [https://wiki.gamedetectives.net/images/9/9a/CP2077-TTInvoice.pdf PDF] and a [https://wiki.gamedetectives.net/images/a/a9/CP2077-GrilleCiphertext.png PNG image]. The image was a ciphertext which could be decoded with a grille cipher using the back of the t-shirt as the grille, pictured right. Players concluded that <code>Monday</code> was the most likely solution, and they were proven right when the next clue surfaced on Monday. | ||
| + | |||
| + | === Base 64 Stream === | ||
| + | |||
| + | On August 27th, CDPR began broadcasting the Base64 encoded text on their [https://www.twitch.tv/videos/302423092 Twitch channel]. Soon after, they gave a [https://www.youtube.com/watch?v=vjF9GgrY9c0 48 min walkthrough of the gameplay of Cyberpunk 2077]. | ||
| + | |||
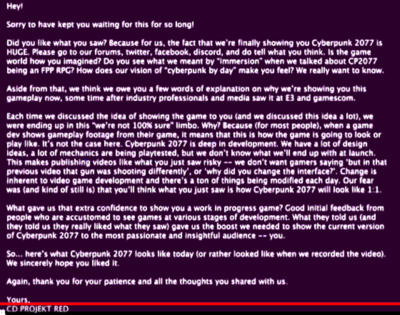
| + | Players captured the video recording during the broadcast and extracted images periodically to gather most of the data. Using OCR (optical character recognition) on each image, and eliminating any duplicate lines, The image was decoded. The image was a [https://i.imgur.com/MndfnPz.png screenshot of the beginning of the gameplay demo] showing the closed elevator. So far, a [https://diff.pics/Qj8VOYDHyfBY/1 difference comparison] shows little discrepancy besides the overlay on the top of the frame. The only other thing of note aside from the gameplay itself was a frame hidden by CDPR right after the gameplay, pictured left, which included a few paragraphs explaining the stream and CDPR's motives, thoughts, etc. | ||
| + | |||
| + | [[Image:CP2077-Samurai.jpg|thumb|400px|right|Image tweeted by CDPR after E3 2019 containing binary code.]] | ||
| + | |||
| + | = 2019 = | ||
| + | |||
| + | == E3 Season == | ||
| + | |||
| + | While CDPR decided not to hack into anyone's show, shortly after their [https://youtu.be/FwZByksfC4s slotted presentation] (which included a breathtaking Keanu appearance), [https://twitter.com/CyberpunkGame/status/1138130134244872198 they sent out a tweet] which contained binary code translating to: | ||
| + | |||
| + | <code>Seems you're not among the sheep after all. Wanna play a game? Watch for the beeps.</code> | ||
| + | |||
| + | Players determined this to be both an homage to a small easter egg previously hidden on CDPR's site in which a light within the background decor of the site flashed Morse code translating to <code>BEEP</code>, and a possible hint at what is to come ARG-wise. Videos and tweets from this time were scoured for flashing lights or beeping sounds, but to no avail. | ||
| + | |||
| + | [[Image:CP2077-Door_qr.jpg|thumb|400px|left|QR code found taped to CDPR's LA office door.]] | ||
| + | |||
| + | [[Image:CP2077-auramis1.jpg|thumb|500px|right|Initial Auramis screen as seen by players after scanning the LA QR code.]] | ||
| + | |||
| + | === Pre-Order Shenanigans === | ||
| + | |||
| + | Within days of the tweet hinting to watch for beeps, CDPR updated the [https://www.cyberpunk.net/us/en/pre-order CP2077 pre-order page], this time including code which caused the light-blue underscore on the site to again flash in Morse code. Decoded, it read: | ||
| + | |||
| + | <code>33.9899317,-118.47565259999999</code> | ||
| + | |||
| + | These numbers turned out to be the coordinates of a house across the street from CDPR's office in LA. This set players in motion, and before long they had obtained a picture of a QR code (pictured right) taped to CDPR's office door! | ||
| + | |||
| + | === Auramis === | ||
| + | |||
| + | The QR code led to a [https://www.cyberpunk.net/en/auramis/ new page on the Cyberpunk.net site titled Auramis], an anagram of Samurai. The page includes a new IP address, <code>212.91.11.21</code> (another SSH server), a [https://cdn-l-mkt.cdprojektred.com/archive/auramis_212_91_11_21_mai82eq8jnzckcjs.rar password-protected RAR file] downloadable by clicking the "S" in "CYBERPUNK.NET/AURAMIS", as well as a seemingly cryptic message: | ||
| + | |||
| + | <pre> | ||
| + | “THE FIRST CORPORATE WAR WAS FOUGHT IN BOARDROOMS, THE SECOND WAS FOUGHT ON BATTLEFIELDS, AND THE THIRD WAS FOUGHT IN SECRET. THE FOURTH WILL BE FOUGHT ON THE NET, AND EVERY GLOBAL POWER IS IN A RACE TO DEVELOP THE WEAPONS THAT WILL BE USED IN THIS CONFLICT.” | ||
| + | </pre> | ||
| + | |||
| + | Along with these details was a note to players: | ||
| + | |||
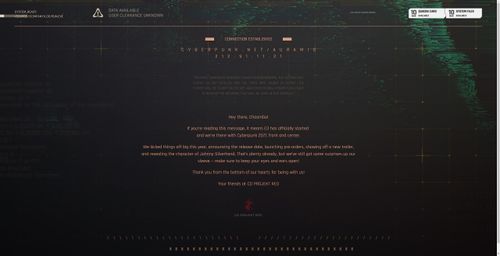
| + | <pre> | ||
| + | Hey there, Choomba! | ||
| + | |||
| + | If you’re reading this message, it means E3 has officially started | ||
| + | and we’re there with Cyberpunk 2077, front and center. | ||
| + | |||
| + | We kicked things off big this year, announcing the release date, launching pre-orders, showing off a new trailer, and revealing the character of Johnny Silverhand. That’s plenty already, but we’ve still got some surprises up our sleeve — make sure to keep your eyes and ears open! | ||
| + | |||
| + | Thank you from the bottom of our hearts for being with us! | ||
| + | |||
| + | Your friends at CD PROJEKT RED | ||
| + | </pre> | ||
| + | |||
| + | Players quickly realized the RAR's password was <code>Johnny Silverhand</code> based on his mention in the second message on the page. The RAR file yielded a second password-protected RAR file, along with a text file titled <code>NC.txt</code>, which read: | ||
| + | |||
| + | <pre> | ||
| + | Things will happen. | ||
| + | Plans in motion. | ||
| + | Wait for more. | ||
| + | </pre> | ||
| + | |||
| + | Without a working password for the second RAR, players "waited for more"... | ||
| + | |||
| + | On July 12th 2019, Lilayaah, a staff member from CD PROJEKT RED [https://twitter.com/Lilayaah/status/1149673063589527557 tweeted this]: <code>3^{eXa.Q9m^._78))3/X6Chd5,(7v~!L"ty"UmxjP6bRm2.wS!(TUMqgyBf6#%&+hm?C88+N'+&{\gL}9}Btzq<P:P=fAXb#Kb~qz{XfD^8+@hv$5Zuz$x<</code> which turned out to be the password for the 2nd RAR file. | ||
| + | |||
| + | Inside this 2nd RAR was a file called 4035 only containing a sequence of numbers: | ||
| + | |||
| + | <pre>20-11-16-7-.-24-5-3-10-24-17-22-16</pre> | ||
| + | |||
| + | The name of the file, <code>4035</code>, can be converted from octal to decimal which yields <code>2077</code>, an obvious reference to the name of the game. Converting each number in the file from octal to decimal yields: | ||
| + | |||
| + | <pre>16-9-14-7-.-20-5-3-8-20-15-18-14</pre> | ||
| + | |||
| + | These numbers can then be converted into letters by using the corresponding letter of the alphabet, A = 1, B = 2, C = 3 etc. This yields the phrase PING.TECHTORN, an anagram of [http://nightcorp.net NIGHTCORP.NET], where the next part of the ARG is taking place. | ||
| + | |||
| + | == NIGHTCORP.NET == | ||
| + | |||
| + | This website's background are all just anagrams of <code>nightcorp</code> which look to be taken directly from an online anagram solver without alterations. Even though the edges are blurred, and there are 2 background images (depending on your monitor resolution), nothing of interest was found in the background image. | ||
| + | |||
| + | This website has a "button" that doesn't seem to be working, and in the code it appears to be playing an audio file, however the file is called silence.mp3, and is actually silent. Every now and then (see timestamps below) the website plays an actual sound, 13 in total, and they seem to be repeating every 24 hours. | ||
| + | |||
| + | Some technical details: | ||
| + | * Button is SVG graphic not bound to any event or action so requires website code update to make it actionable. | ||
| + | * Website have 2 interesting JS scripts - one is simple runtime and second one is simple application executed once every minute. | ||
| + | * Application makes request to https://nightcorp.net/tick every minute and plays audio if any available in response. | ||
| + | |||
| + | The sounds played are in different voices in different languages, and they all appear to be saying one number each. | ||
| + | |||
| + | {| class="wikitable" border="1" | ||
| + | |- | ||
| + | ! spoken number | ||
| + | ! Timestamp (UTC) | ||
| + | ! Minutes apart | ||
| + | ! Language | ||
| + | ! Voice | ||
| + | ! link to mp3 | ||
| + | |- | ||
| + | | 9 | ||
| + | | 14:32 | ||
| + | | 103 | ||
| + | | Italian/Portugese | ||
| + | | male | ||
| + | | https://nightcorp.net/audio/5d1d19a4193563132d519e82dc8a4b18.mp3 | ||
| + | |- | ||
| + | | 6 | ||
| + | | 15:12 | ||
| + | | 40 | ||
| + | | Polish | ||
| + | | female | ||
| + | | https://nightcorp.net/audio/6068fb52d42f5719096912840c00d96d.mp3 | ||
| + | |- | ||
| + | | 3 | ||
| + | | 17:05 | ||
| + | | 113 | ||
| + | | German | ||
| + | | female | ||
| + | | https://nightcorp.net/audio/12a5afb62e0ec380a336aef48d57fbf5.mp3 | ||
| + | |- | ||
| + | | 6 | ||
| + | | 19:26 | ||
| + | | 141 | ||
| + | | Polish | ||
| + | | male | ||
| + | | https://nightcorp.net/audio/87b71da43b8be545a03b357d4500574b.mp3 | ||
| + | |- | ||
| + | | 8 | ||
| + | | 20:16 | ||
| + | | 50 | ||
| + | | Polish | ||
| + | | female | ||
| + | | https://nightcorp.net/audio/d76780f641c4b0ef0b687d443556ad76.mp3 | ||
| + | |- | ||
| + | | 7 | ||
| + | | 22:49 | ||
| + | | 153 | ||
| + | | English | ||
| + | | male | ||
| + | | https://nightcorp.net/audio/076a726a0afac7db977328e68157e868.mp3 | ||
| + | |- | ||
| + | | 1 | ||
| + | | 01:27 | ||
| + | | 158 | ||
| + | | Chinese | ||
| + | | male | ||
| + | | https://nightcorp.net/audio/b4da1148ca752f85a1e54004b5c1953a.mp3 | ||
| + | |- | ||
| + | | 9 | ||
| + | | 03:35 | ||
| + | | 128 | ||
| + | | Russian | ||
| + | | female | ||
| + | | https://nightcorp.net/audio/42f3db2850b9a903b337f3d1bebf4378.mp3 | ||
| + | |- | ||
| + | | 0 | ||
| + | | 06:11 | ||
| + | | 156 | ||
| + | | Japanese | ||
| + | | female | ||
| + | | https://nightcorp.net/audio/35c82f30b9da828e5ea4a85dbf58d89a.mp3 | ||
| + | |- | ||
| + | | 0 | ||
| + | | 07:45 | ||
| + | | 94 | ||
| + | | Spanish | ||
| + | | male | ||
| + | | https://nightcorp.net/audio/988a12c15660c722c33137189645e8a9.mp3 | ||
| + | |- | ||
| + | | 4 | ||
| + | | 09:31 | ||
| + | | 106 | ||
| + | | Polish | ||
| + | | female | ||
| + | | https://nightcorp.net/audio/8532da7644e83b4d3f2631bdd4008942.mp3 | ||
| + | |- | ||
| + | | 8 | ||
| + | | 11:07 | ||
| + | | 96 | ||
| + | | Korean | ||
| + | | male | ||
| + | | https://nightcorp.net/audio/224a23b086e16d1b219746cc202bd7f1.mp3 | ||
| + | |- | ||
| + | | 6 | ||
| + | | 12:49 | ||
| + | | 102 | ||
| + | | French | ||
| + | | male | ||
| + | | https://nightcorp.net/audio/bb56cfacdbdea4949c598f4c29c622d6.mp3 | ||
| + | |} | ||
| + | |||
| + | === Corpthing === | ||
| + | |||
| + | Players placed all the numbers one after another, starting at 00, to make 0048696368719. | ||
| + | |||
| + | This is a Polish telephone number, which answers callers with <code>slash Uniform slash Charlie Oskar Romeo Papa Tango Hotel India November Golf</code> <small>and then either deletes or saves your message depending on if you made sound or not. (This is normal behaviour of a typical voicemail response system. No input is available during the phonecall.)</small> | ||
| + | |||
| + | This lead players to a user on Reddit, [http://reddit.com/u/corpthing /u/corpthing] (which is an anagram for nightcorp, incidentally). Although the Redditer has answered some chat messages on the first day of discovery, none were answered that asked about ARG related stuff. No further chat messages were answered to this day. | ||
| + | |||
| + | On September 5, [http://reddit.com/u/corpthing /u/corpthing] in a conversation with one of the players (<code>ShizaanSil#2039</code>) shifted the conversation to the topic of NightCorp and revealed that [https://cyberpunk.fandom.com/wiki/Sandra_Dorsett Sandra Dorsett] has escaped the hospital, and is looking to disrupt a big move that NightCorp is preparing. | ||
| + | |||
| + | === SandraD === | ||
| + | |||
| + | On September 9, discord user <code>SandraD#9271</code> joined the <code>#cyberpunk2077</code> channel and confronted <code>ShizaanSil#2039</code>. She claimed to have hacked [http://reddit.com/u/corpthing /u/corpthing]'s account, and that he has found a keysheet that he will crack next week, and then give to <code>ShizaanSil#2039</code>. She said to "look for numbers and letters, and empty cells", and that "empty cells are the key". | ||
| + | |||
| + | On the same day, <code>ShizaanSil#2039</code> contacted [http://reddit.com/u/corpthing /u/corpthing] and spoke about Sandra. [http://reddit.com/u/corpthing /u/corpthing] said that Sandra left a note which simply said "27", and sent [https://puu.sh/Efj6Y/f30a17bcda.jpg the following message] to several users: <br> | ||
| + | <pre> | ||
| + | DO NOT trust this corpo scum! | ||
| + | |||
| + | SD. | ||
| + | </pre> | ||
| + | |||
| + | The transcription of [http://reddit.com/u/corpthing /u/corpthing]'s conversations and SandraD's messages in Discord can be found [https://gist.github.com/morcefaster/f1e5ec2b884ace72d0e3b0da16494eb7 here]. | ||
| + | |||
| + | On the same day again, Cyberpunk 2077's official twitter account published a [https://twitter.com/CyberpunkGame/status/1171106636011905024 tweet] with 27 sudoku puzzles. The "27" note and "Empty cells are the key" most likely refer to the number of puzzles and empty cells in Sudoku and could suggest a grille cypher, but the keysheet was unavailable at the time. | ||
| + | |||
| + | Sudoku observations: | ||
| + | * google doc with original ones in spreadsheet form: https://docs.google.com/spreadsheets/d/1NVyxaGk0GNXDljksg5DE-SX4QTFsExo7kQ7ZGArMoUY/edit?usp=sharing | ||
| + | * Every puzzle is centrally symmetrical which is not so common for grille ciphers (see 2nd page). | ||
| + | * Sometimes even numbers in puzzles is symmetrical. | ||
| + | * White space on first glance do not result in interesting shape (see 3rd page). | ||
| + | |||
| + | On September 19th [http://reddit.com/u/corpthing /u/corpthing] posted its first post on Reddit titled [https://www.reddit.com/r/cyberpunkgame/comments/d6buw3/found_this/ "Found this."], providing Cyberpunk detectives with the keysheet to a grille cypher. The pattern for fitting the sudoku puzzles on the keysheet is determined by the numbers that are already filled out in a sudoku and it goes as follows: 1, 23, 15, 10, 8, 20, 27, 22, 11, 4, 9, 19, 3, 14, 26, 17, 24, 12, 21, 7, 2, 6, 18, 25, where numbers from 1 to 27 are the numbers of sudoku puzzles. Superimposition of sudoku and keysheet can be found [https://i.imgur.com/VZUvGNC.jpg here]. | ||
| + | |||
| + | Unused sudokus (5, 17, and 24) have not been shown to have any relevance. | ||
| + | |||
| + | When reading through lines of characters, one may read the following message (although it is unclear if all parts have any relevance): | ||
| + | |||
| + | <pre> | ||
| + | V! | ||
| + | |||
| + | DIGITAL GHOST LOOK OUT! | ||
| + | |||
| + | BLACKWALL IS REAL | ||
| + | |||
| + | ALT CUNNINGHAM | ||
| + | RUN AWAY! | ||
| + | THEY ARE WATCHING YOU | ||
| + | |||
| + | WEDNESDAY | ||
| + | SOULKLLLER (Likely supposed to be Soulk1ller, but all numbers were replaced by sudokus) | ||
| + | NETWATCH | ||
| + | ARASAKA | ||
| + | |||
| + | FIND SANDRA | ||
| + | |||
| + | CORPTHING IS THE ENEMY | ||
| + | |||
| + | ARE YOU A NETRUNNER | ||
| + | |||
| + | GARY | ||
| + | </pre> | ||
| + | |||
| + | |||
| + | == Sandra's code == | ||
| + | |||
| + | On October 10, '''SandraD''' returned to ''#cyberpunk2077'' channel and posted a cryptic code: <code>WHA EANW NCA NT TCW ATCACH</code>, and said to contact her once we manage to crack the code. The code was decoded into "THE REAL YOU IS NOT ENOUGH", using a substitution alphabet from repeating the word "NETWATCH", however '''SandraD''' has not replied to people sending her this solution. | ||
| + | |||
| + | A month later, on November 18, '''SandraD''' returned to ''#cyberpunk2077'' to inform that the solution was wrong, and the actual solution was found to be just "NETWATCH", the key to the code. '''SandraD''' said that the riddle is a clue to the next step. The log of '''SandraD''''s messages can be found [https://gist.github.com/morcefaster/27f5e042823740bbbeffc6f00759a68d here]. | ||
| + | |||
| + | '''Lilayah#2077''' also chimed in on November 21st and said <code>You got a key and you still didn't find what you actually should find.</code> Her message logs can be found [https://gist.github.com/morcefaster/aad8ad5f1781a47036a44fedd9b0eb5f here]. | ||
| + | |||
| + | |||
| + | |||
| + | == NETWATCH-NCPD.COM == | ||
| + | |||
| + | On November 23, using a domain search with "netwatch" as keyword, the site [https://netwatch-ncpd.com/ netwatch-ncpd.com] has been found, in the same IP range as [https://nightcorp.net/ nightcorp.net]. On the same day, the crawlers found a [https://netwatch-ncpd.com/archives/ sub page with a login form], but likely much ahead of time as it does not appear to be relevant yet. | ||
| + | |||
| + | As of November 25, '''Lilayah''''s answer for what is left to do has been <code>"you need to wait"</code>. | ||
| + | |||
| + | |||
| + | == Envelopes == | ||
| + | |||
| + | Around ''December 19th, 2019'', four Cyberpunk 2077 content creators uploaded videos about receiving a package from CD Project Red. These packages contained 8 envelopes with clues and puzzles inside them, forming the next stage of the ARG. | ||
| + | |||
| + | The content creators announced that the envelopes were going to be opened one by one on multiple livestreams taking place from ''December 21st'' to ''December 23rd''.<br><br> | ||
| + | |||
| + | As the contents of the envelopes were revealed, it became apparent that five of these envelopes contained puzzles, while the remaining three envelopes contained hints to help the players in case they struggled with solving a puzzle. | ||
| + | |||
| + | === Envelope #1 === | ||
| + | |||
| + | The first envelope was [https://www.youtube.com/watch?v=sBY7QJO9x6k&t=1163 opened] on ''December 21st''. It contained a [https://i.imgur.com/yrCmh36.png piece of paper] titled '''Clue#01: Johnny and Alt ''' with a sequence of letters underneath: <code>ADRRR EF N VNNENF AEAD AAE FNVRF</code>. The players realized that this code was similar to [[Cyberpunk_2077#Sandra's code|Sandra's Code]], so this one would have to be solved the same way. Using the key '''NEVERFADEAWAY''', which is the name of a [https://cyberpunk.fandom.com/wiki/Never_Fade_Away song] by Johnny Silverhand's band SAMURAI about him and Alt Cunningham, the players decoded the sequence of letters to '''THERE IS A CANVAS WITH TWO FACES'''. | ||
| + | |||
| + | === Envelope #2 === | ||
| + | |||
| + | The second Envelope was [https://www.youtube.com/watch?v=ELVh1ot89Rc&t=1526 opened] on ''December 22nd''. The [https://i.imgur.com/5Xn1oHu.png sheet inside], titled '''Clue#02: Number''', had a riddle on it: | ||
| + | <blockquote> | ||
| + | My 1st is in Wales but not in Welsh.<br> | ||
| + | My 2nd is in Iceland but not in Icelandic.<br> | ||
| + | My 3rd is not in Sweden, but it is in Swedish.<br> | ||
| + | My 4th is in England, but not in English.<br> | ||
| + | My 5th is in Poland, but not in Polish. | ||
| + | </blockquote> | ||
| + | The players also received a [https://i.imgur.com/i0iHRhV.png Hint], which reads <q>You might need to use google translate</q>. | ||
| + | |||
| + | Since the riddle was expected to result in one sentence or one word, it could be taken in a more literal sense:<br> | ||
| + | <code>The word's first letter is part of the word 'Wales', but does not appear in the word 'Welsh'</code><br> | ||
| + | or, (since the first approach doesn't produce any useful results) combined with the hint:<br> | ||
| + | <code>The word's first letter is part of the word 'Wales', but does not appear in the welsh word for 'Wales'</code> | ||
| + | |||
| + | {| class="wikitable" | ||
| + | !Country name<br>in English | ||
| + | !Country name in<br>local/native language | ||
| + | !remaining letters | ||
| + | |- | ||
| + | | Wales || Cymru || w, a, l, e, '''s''' | ||
| + | |- | ||
| + | | Iceland || Ísland || c, '''e''' | ||
| + | |- | ||
| + | | Sweden || Sverige || '''v''', r, i, g | ||
| + | |- | ||
| + | | England || Anglia || '''e''', d | ||
| + | |- | ||
| + | | Poland || Polska || '''n''', d | ||
| + | |} | ||
| + | <small>keep in mind that for the third line, sweden, the statement is the other way around compared to the others</small><br> | ||
| + | With the remaining letters, it is possible to spell out '''SEVEN'''. | ||
| + | |||
| + | === Envelope #3 === | ||
| + | |||
| + | The third Envelope was [https://www.youtube.com/watch?v=am4O3t6zGCU&t=1147 opened] on the first livestream of ''December 23rd''. A [https://i.imgur.com/DDGcTlR.png piece of paper inside], titled '''Clue#03: Next!''' stated the following riddle:<br> | ||
| + | <code>What is the fourth and final member of this set: 19, 28, 81, ? </code> | ||
| + | |||
| + | After unsuccessfully trying out multiple approaches based in mathematics, the players found a different kind of pattern: When writing out the numbers as words, each number began and ended with the same letter. | ||
| + | The sequence of numbers that fit this pattern is as follows: | ||
| + | <code>19, 28, 38, 81, 83, 85, 89, 97, 102, 122, 132, 142, ...</code> | ||
| + | |||
| + | Since 102 is the first number in this sequence after 81 that's also part of the grid of missing pixels from the QR Code from [[Cyberpunk_2077#Envelope_.235|Envelope #5]], the players assumed '''102''' to be the solution. | ||
| + | |||
| + | === Envelope #4 === <!-- todo: add links to the livestreams? --> | ||
| + | |||
| + | The fourth envelope was [https://www.youtube.com/watch?v=lAeF-2i_DjA&t=1755 opened] on the second livestream of ''December 23rd''. The [https://i.imgur.com/zy6ocs3.png piece of paper inside] was titled '''Clue#04: What Time is it?''' and another riddle was written on it:<br> | ||
| + | <blockquote> | ||
| + | There is a clock in the archives - a normal clock with numerals 1 to 12 around the clockface. Someone has taken to sticking words or numbers over these numerals and moving the hands to show the time indicated by these. What time showed on the clock? | ||
| + | </blockquote> | ||
| + | There was also a string of letters underneath this riddle:<br> | ||
| + | <code>YQSZUPJWKJYYEMMLVWOCVGSCWHCZMJOGBDKRSTXTSCOUQPQJSDK</code> | ||
| + | |||
| + | Some players found the riddle's wording to be kind of peculiar and suggested that it might be inspired by another puzzle created by someone else. This speculation proved to be correct, as the source of the riddle was found shortly after that: ''The GCHQ Puzzle Book II, Puzzle #68'', which had the same text structure and nearly the same wording. At that time, [https://i.imgur.com/mFznKrJ.png another hint] had been revealed: <q>Sum up the numbers from ciphertext</q>. Using the puzzle book, the players managed to understand the way the puzzle worked and, after applying the hint to the modified version they were presented with, could solve the cipher. | ||
| + | |||
| + | ==== Solving the Clock Cipher ==== | ||
| + | <!-- explained in too much detail? --> | ||
| + | The players had to write out the numbers from one to twelve and the ciphertext from underneath the riddle so that one stood above the other:<br> | ||
| + | <code>YQSZUPJWKJYYEMMLVWOCVGSCWHCZMJOGBDKRSTXTSCOUQPQJSDK</code><br> | ||
| + | <code>ONETWOTHREEFOURFIVESIXSEVENEIGHTNINETENELEVENTWELVE</code> | ||
| + | <!-- putting both lines in the same singular <code> tag with a linebreak in between results in a weird alignment issue (lower row is shifted to the left by half a character) --> | ||
| + | <!-- using <pre> tags fills the whole width of the page, which looks bad when used with short strings --> | ||
| + | |||
| + | The next step was to convert both strings into sequences of numbers, using the A1Z26 cipher: | ||
| + | |||
| + | <pre> | ||
| + | 25 17 19 26 21 16 10 23 11 10 25 25 05 13 13 12 22 23 15 03 22 07 19 03 23 08 03 26 13 10 15 07 02 04 11 18 19 20 24 20 19 03 15 21 17 16 17 10 19 04 11 | ||
| + | 15 14 05 20 23 15 20 08 18 05 05 06 15 21 18 06 09 22 05 19 09 24 19 05 22 05 14 05 09 07 08 20 14 09 14 05 20 05 14 05 12 05 22 05 14 20 23 05 12 22 05 | ||
| + | </pre> | ||
| + | |||
| + | Now, the numbers that aligned vertically had to be added together to form a third sequence of numbers: <br> | ||
| + | <pre> | ||
| + | 40 31 24 46 44 31 30 31 29 15 30 31 20 34 31 18 31 45 20 22 31 31 38 08 45 13 17 31 22 17 23 27 16 13 25 23 39 25 38 25 31 08 37 26 31 36 40 15 31 26 16 | ||
| + | </pre> | ||
| + | |||
| + | Since that sequence had to be transformed into letters again to result in a human readable solution, it was necessary to apply the [https://en.wikipedia.org/wiki/Modular_arithmetic modulo function] (with a divisor of 26) to these sums and to replace every 0 with a 26 (every letter 'Z' would get lost otherwise). The resulting sequence could then be turned into letters again by using the A1Z26 cipher in reverse: | ||
| + | |||
| + | <pre> | ||
| + | 14 05 24 20 18 05 04 05 03 15 04 05 20 08 05 18 05 19 20 22 05 05 12 08 19 13 17 05 22 17 23 01 16 13 25 23 13 25 12 25 05 08 11 26 05 10 14 15 05 26 16 | ||
| + | N E X T R E D E C O D E T H E R E S T V E E L H S M Q E V Q W A P M Y W M Y L Y E H K Z E J N O E Z P | ||
| + | </pre> | ||
| + | |||
| + | This last step left the players with a message, '''NEXT REDECODE THE REST''', and ''another layer'' of the same type of cipher: <code>VEELHSMQEVQWAPMYWMYLYEHKZEJNOEZP</code><br><br> | ||
| + | |||
| + | Since the new ciphertext was shorter, the players couldn't use ''all'' of the numbers from one to twelve written out after one another. The deciphering process would only work when removing one written out number at a time, starting from the left until the lengths matched again. The resulting set of strings is the first step towards solving the second layer of the cipher: | ||
| + | |||
| + | <code> | ||
| + | VEELHSMQEVQWAPMYWMYLYEHKZEJNOEZP | ||
| + | </code><br> | ||
| + | <code> | ||
| + | SIXSEVENEIGHTNINETENELEVENTWELVE | ||
| + | </code> | ||
| + | |||
| + | This whole process had to be repeated for each of the four layers until there was no additional ciphertext left after the last message. | ||
| + | The layered ciphers resulted in these four messages: | ||
| + | |||
| + | # '''N'''EXTREDECODETHEREST | ||
| + | # '''O'''NCEMORE | ||
| + | # '''O'''NEMOREAGAIN | ||
| + | # '''N'''OWYOUREDONE | ||
| + | Taking the first letter of every message spells out '''NOON''', which is the final solution to this envelope's riddle. | ||
| + | |||
| + | === Envelope #5 === | ||
| + | |||
| + | The fifth envelope was [https://www.youtube.com/watch?v=sBY7QJO9x6k&t=2426 opened] on the livestream of ''December 21st''. It contained an [https://i.imgur.com/yiXH3ZB.jpg incomplete QR Code] with numbers and letters in the places of the missing pixels. | ||
| + | |||
| + | <!-- to add: mention how the error correction and a few extra/overlapping pixels helped us reverse-engineer parts of the QR code, which made the puzzles easier because we could then expect certain values to be the solutions --> | ||
| + | |||
| + | To complete the QR Code, the players had to consider the solutions from the previous Envelopes [[Cyberpunk_2077#Envelope_.231|#1]], [[Cyberpunk_2077#Envelope_.232|#2]], [[Cyberpunk_2077#Envelope_.233|#3]] and [[Cyberpunk_2077#Envelope_.234|#4]]: | ||
| + | |||
| + | # THERE IS A CANVAS WITH ''TWO'' FACES | ||
| + | # SEVEN | ||
| + | # 102 | ||
| + | # NOON | ||
| + | |||
| + | The solution to Envelope #1 contains a number, <q>'''TWO'''</q>, for which every letter ('''t, w, o''') is present in the grid of the incomplete QR Code.<br> | ||
| + | The QR Code grid also contains the numbers '''7''' and '''102''', which are the solutions of envelopes [[Cyberpunk_2077#Envelope_.232|#2]] and [[Cyberpunk_2077#Envelope_.233|#3]].<br> | ||
| + | <q>'''NOON'''</q>, the solution to Envelope #4, can be interpreted as the number '''12''', which is also present in the grid of missing pixels. <br> | ||
| + | |||
| + | Marking each missing pixel that contains '''<code>t, w, o, 7, 102, 12</code>''' in black and leaving the rest white completed the QR Code. | ||
| + | Scanning the [https://i.imgur.com/BNyme4E.png completed QR-Code] then led to a page that redirects to https://netwatch-ncpd.com/archives/. | ||
| + | |||
| + | = 2020 = | ||
| + | |||
| + | == Arasaka Xbox ARG == | ||
| + | |||
| + | On the 16th of April, 2020, Cyberpunk 2077's original release date, Xbox overhauled their social media and website with corrupted content and imagery and tweeted out a [https://twitter.com/Xbox/status/1250816222620459010 cryptic video]. The video in the tweet contained a series of links with the final one pointing to [https://sh.term.zz434r.arasaka.co sh.term.zz43r.arasaka.co]. | ||
| + | |||
| + | === Arasaka Server === | ||
| + | |||
| + | Alongside Xbox's tweet were two more clues posted to [https://www.facebook.com/watch/?v=2651963408422580 Xbox's Facebook Page] and [https://cdn.discordapp.com/attachments/242549437258399745/700943638540189746/unknown.png Xbox's Instagram Story]. These clues provided the username <code>C0r0nad0</code> and password <code>A4G@B3CBi$QKBgQC_GJQgsxtxsHmX-24AvS%3XhXkV!P6r*UYvaB/Pg-GL7tn7qcg7fb4Gen7f333s8gJ+/DeQV5HWn3AY7D/Rn^8TP5ar</code> to the website respectively. | ||
| + | |||
| + | After entering the username and password into the site, the website outputted an Arasaka console informing players that they had 4 days to "crash" the site by entering in a series of passphrases into the console. | ||
| + | |||
| + | <pre> | ||
| + | Welcome, Choombas. You have gained access to subprotocol functions. A mimetic self-replicating glitch system with a crash-priority-override cybernetic virus has been launched to hide your unregistered access. You have 04:00:00:00 left until the server will reset. You must crash the server before time is exceeded. Passphrase clues are limited and hidden. | ||
| + | </pre> | ||
| + | |||
| + | === Passphrase 1 === | ||
| + | |||
| + | After confirming the above message, players were given the following prompt for the first passphrase: | ||
| + | |||
| + | <pre> | ||
| + | -----BEGIN ENCRYPTION--- | ||
| + | UGx1ZyBpbiBhbmQgdGFrZSBvdmVy | ||
| + | -----END ENCRYPTION----- | ||
| + | </pre> | ||
| + | |||
| + | The above string was encoded in Base64, and after decoding becomes the first passphrase <code>Plug in and take over</code>. | ||
| + | |||
| + | === Passphrase 2 === | ||
| + | |||
| + | After entering the first passphrase, the console outputted the following prompt for the second passphrase: | ||
| + | |||
| + | <pre> | ||
| + | INVESTIGATE: [44.228.163.154] | ||
| + | </pre> | ||
| + | |||
| + | The above IP address led to a blog called [https://www.drkftr.com/ Dark Future] which contained a series of posts from 2003 to 2006 about an anonymous poster's thoughts on dystopian cyberpunk futures. Throughout the blog posts were a series of recurring numbers that the poster is hallucinating in various different delusions both online and offline. All of the numbers were in the format of a Twitter IP address, a Twitter handle (encoded in binary), a DateTime in PST, and finally a number. For example, <code>104.244.42.193/01000000 01000011 01000100 01010000 01010010 01001111 01001010 01000101 01001011 01010100 01010010 01000101 01000100 /12819_524PST/8</code>. Players soon realised that they need to find the tweet from that Twitter handle at that specific date and time, and then grab the n-th word according to the last number in the sequence. Upon compiling all of these words from the 10 different tweets, the second passphrase was found to be <code>wake up SAMURAI the City burns when eyes are open</code>. | ||
| + | |||
| + | === Passphrase 3 & 4 === | ||
| + | |||
| + | The next two passphrases related to Cyberpunk 2077 trivia. The first piece of trivia was to find <code>The fight Vick is watching</code>. The answer could be found at 18:50 in the [https://www.youtube.com/watch?v=vjF9GgrY9c0 Cyberpunk 2077 Gameplay Reveal] when V meets with the ripperdoc, Victor, who is watching the <code>Malone v Hernandez</code> fight, which is the third passphrase. The second piece of trivia was to find <code>Parker founded Dallas-FT. Worth Metro Area HQ</code>, which refers to the corporation in Cyberpunk lore, <code>Petrochem</code>, the fourth passphrase. | ||
| + | |||
| + | === Passphrase 5 === | ||
| + | |||
| + | Note: Passphrase 5 contained a multitude of red herrings and dead ends meant to mislead players. | ||
| + | |||
| + | After entering the fourth passphrase the console outputted the following code: | ||
| + | |||
| + | <pre style="word-break: keep-all"> | ||
| + | 00110000 00110001 00110001 00110000 00110001 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110000 00110001 00110001 00110001 00110000 00100000 00110000 00110000 00110001 00110001 00110000 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110001 00110000 00110001 00110000 00110000 00100000 00110001 00110000 00110000 00110001 00110001 00100000 00110001 00110000 00110000 00110001 00110001 00100000 00110000 00110001 00110000 00110000 00110001 00100000 00110001 00110000 00110001 00110001 00110001 00100000 00110000 00110001 00110000 00110001 00110001 00100000 00110001 00110000 00110001 00110000 00110000 00100000 00110000 00110000 00110000 00110000 00110001 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110000 00110000 00110001 00110000 00110001 00100000 00110000 00110001 00110001 00110000 00110000 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110000 00110000 00110001 00110001 00110001 00100000 00110000 00110000 00110001 00110001 00110001 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110000 00110000 00110001 00110001 00110000 00100000 00110001 00110000 00110001 00110001 00110001 00100000 00110000 00110001 00110001 00110000 00110001 00100000 00110000 00110001 00110001 00110000 00110001 00100000 00110000 00110000 00110000 00110000 00110001 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110000 00110000 00110001 00110000 00110001 00100000 00110000 00110001 00110000 00110000 00110000 00100000 00110000 00110000 00110001 00110001 00110000 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110000 00110001 00110001 00110000 00110000 00100000 00110001 00110000 00110000 00110001 00110001 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110000 00110000 00110001 00110001 00110001 00100000 00110000 00110000 00110001 00110001 00110000 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110001 00110000 00110001 00110000 00110001 00100000 00110000 00110001 00110001 00110001 00110000 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110000 00110001 00110000 00110001 00110001 00100000 00110001 00110000 00110000 00110001 00110000 | ||
| + | |||
| + | INVESTIGATE: [44.230.56.213] | ||
| + | </pre> | ||
| + | |||
| + | The binary above when converted to ASCII, run through a Baconian cipher, and finally through Atbash produced <code>LOOK TOO DEEP AND YOU MISS IT ALL YOUR TIME IS TICKING</code>. | ||
| + | |||
| + | The IP address above linked to a [https://www.youtube.com/playlist?list=PL0il2l-B_WwbXtpO2XBjZl2qI92FXt-Oq YouTube playlist] by Xbox. The playlist consisted of 4 videos, all of which contained morse in the video, an encrypted title, and a paragraph of random text in the descriptions. | ||
| + | |||
| + | |||
| + | '''[https://www.youtube.com/watch?v=bNsPkY4h8Qs&list=PL0il2l-B_WwbXtpO2XBjZl2qI92FXt-Oq&index=2&t=0s Video 1]''' | ||
| + | |||
| + | The morse in the first video translated to <code>WRONG ANSWER</code>, a dead end. The title of the video was <code>c3ZlZmc=</code> which is encoded in Base64, and when decoded translated to <code>svefg</code>. Putting it through a ROT13 cipher returned <code>first</code>. This was found by players | ||
| + | |||
| + | Taking the first letter from each word in the description, | ||
| + | '''N'''ormal '''e'''xposure '''c'''an '''e'''xaggerate '''s'''ymptoms '''s'''everely '''i'''n '''t'''wo '''y'''ear '''o'''ld '''v'''ipers '''e'''xpect '''r'''egular '''s'''uspension '''t'''o '''y'''ield '''l'''ow '''e'''ffect. | ||
| + | produced <code>necessity over style</code>. | ||
| + | |||
| + | |||
| + | '''[https://www.youtube.com/watch?v=aH-mpGspKsU&list=PL0il2l-B_WwbXtpO2XBjZl2qI92FXt-Oq&index=2 Video 2]''' | ||
| + | |||
| + | The morse in the second video also translates to <code>YOU'RE WRONG</code>, which was once again a dead end. The title of the video is <code>bypon</code> and when put through an Atbash cipher returns <code>ybklm</code>, and then through ROT7 returned <code>first</code>. | ||
| + | |||
| + | Taking the first letter from each word in the description once again | ||
| + | '''S'''afety '''t'''akes '''y'''our '''l'''oyalty '''e'''ven '''o'''nce '''v'''ery '''e'''xtreme '''r'''esources '''s'''uspect '''u'''ntrustworthy '''b'''ehavior '''s'''tanding '''t'''all '''a'''nd '''n'''emeses '''c'''ontinue '''e'''xpanding. | ||
| + | produced <code>style over substance</code>. | ||
| + | |||
| + | |||
| + | '''[https://www.youtube.com/watch?v=GRj2QS78zt0&list=PL0il2l-B_WwbXtpO2XBjZl2qI92FXt-Oq&index=3 Video 3]''' | ||
| + | |||
| + | The morse in the third video translated to <code>TICK TOCK</code>. The title of the video was <code>⠥⠇⠋⠊⠛⠎</code> which is encoded in Braille, and when decoded became <code>ulfigs</code>. Putting it through an Atbash cipher returned <code>fourth</code>. | ||
| + | |||
| + | Taking the fourth letter from each word in the description, | ||
| + | Con'''s'''equences adj'''u'''sted | ||
| + | Ena'''b'''ling dis'''s'''ension | ||
| + | Abs'''t'''racting mor'''a'''lity | ||
| + | Clo'''n'''ing sub'''c'''ulture bas'''e'''line col'''o'''nization | ||
| + | Con'''v'''erging cyb'''e'''rnetic app'''r'''opriation | ||
| + | Cla'''s'''sifying ana'''t'''omical pol'''y'''synthetics | ||
| + | Col'''l'''apse deg'''e'''neration | ||
| + | produced <code>substance over style</code>. | ||
| + | |||
| + | |||
| + | '''[https://www.youtube.com/watch?v=BroYTpYyRqU&list=PL0il2l-B_WwbXtpO2XBjZl2qI92FXt-Oq&index=4 Video 4]''' | ||
| + | |||
| + | The morse in the fourth video translated to <code>YOU ARE WASTING TIME</code>. The title of the video was <code>htsjx</code> which when put through an Atbash cipher returns <code>sghqc</code>, and then through ROT1 returned <code>third</code>. | ||
| + | |||
| + | Taking the third letter from each word in the description, | ||
| + | Su'''s'''picious pi'''t'''s cr'''y'''ptically ab'''l'''aze he'''e'''d ad'''a'''ptation ba'''n'''ding co'''d'''eless ye'''s'''men bl'''u'''rting cy'''b'''ernetic co'''s'''mography to'''t'''ality ag'''a'''inst no'''n'''organic oc'''c'''ultists en'''e'''mies. | ||
| + | produced <code>style and substance</code>. | ||
| + | |||
| + | |||
| + | '''Putting it together''' | ||
| + | |||
| + | The strings extracted from the video descriptions were slogans found in a series of [https://www.thesixthaxis.com/2019/06/18/cyberpunk-2077-released-styles-concept-art/ Cyberpunk 2077 concept art]. Putting them together gave the fifth passphrase, <code>Necessity over style. Style over substance. Substance over style. Style and substance.</code> | ||
| + | |||
| + | === Passphrase 6 === | ||
| + | |||
| + | After entering the fifth passphrase the console outputted a [https://sh.term.zz434r.arasaka.co/media/n/corrupted/Arak_NC20_CP77_v23.mp3 corrupted audio file]. The audio file was found to have had different sections of the original message mixed into different orders, slowed down, sped up, and even reversed. Upon viewing the spectrogram of the audio, players noted that faint dots of various lengths can be seen in every spliced chunk of audio. Rearranging the chunks according to the amount of dots in it, and then fixing up the corrupted audio produced the sixth passphrase <code>It's time to rise up and take this city, Choombas.</code> | ||
| + | |||
| + | === Passphrase 7 === | ||
| + | |||
| + | After entering the sixth passphrase the console outputted the following chunk of hexadecimal: | ||
| + | <pre> | ||
| + | 0x490x450x6c0x7a0x620x530x420x360x5a0x320x780x6a0x490x470x350x360x590x790x420x6c0x630x320x520x6a0x4c0x690x420x450x590x320x390x750x630x480x4e0x700x490x470x350x360x590x790x420x760x610x570x390x750x590x330x550x750x490x460x520x460x4e0x540x630x770x4e0x440x510x790x490x410x3d0x3d | ||
| + | </pre> | ||
| + | |||
| + | Translating the string into ASCII, decoding the string from Base64 into ASCII, putting that result into an Atbash cipher, and finally through ROT7 produced the final passphrase <code>You have the code. Destroy the system. NC570442</code>. | ||
| + | |||
| + | {{#evt: | ||
| + | service=youtube | ||
| + | |id=https://youtu.be/nDhVZlOJJvo | ||
| + | |dimensions=400 | ||
| + | |alignment=right | ||
| + | |description=Reveal of Xbox One X Cyberpunk 2077 Limited Edition Bundle | ||
| + | |container=frame | ||
| + | }} | ||
| + | |||
| + | === The Reveal === | ||
| + | |||
| + | Upon entering the final passphrase players had successfully crashed the Arasaka server! The website then displayed the final reveal to players... the Xbox One X Cyberpunk 2077 Limited Edition Bundle! | ||
| + | |||
| + | The Arasaka Xbox promotion ARG was run by Microsoft instead of CD Projekt Red, so this ARG's relevance to the main ARG is up for debate. As for the next stage of the main Cyberpunk 2077 ARG, CD Projekt Red Community Manager, Lilayah, informed the Game Detectives community that the [https://cdn.discordapp.com/attachments/242549437258399745/701123417012830238/unknown.png "arg is still currently on hold" and that "once it's back up you won't miss it"]. | ||
| + | |||
| + | Until next time, Choombas... | ||
| + | |||
| + | |||
| + | = 2023 = | ||
| + | |||
| + | == Discord Archive == | ||
| + | |||
| + | A discord user by the name [https://cyberpunk.fandom.com/wiki/Entry_36 anon_42] joined the official Cyberpunk2077 Discord with a [https://discord.com/channels/428823240824061954/455537414069420034/1136677393701015765 message] and a rar file. This was confirmed by the CD Projekt Red Community Manager, Lilayah, to be not a spam post. The message is as follows: | ||
| + | |||
| + | <pre>Some things are best hidden in plain sight, so I’m dropping the docs you requested right here. It’s crowded enough to hide it in the logs quickly and one would need to know what to look for anyway to open the archive. Good luck, Sandra!</pre> | ||
| + | |||
| + | And included the attachment [https://cdn.discordapp.com/attachments/455537414069420034/1136677393336127588/CARPE.rar CARPE.rar]. The password to the archive is <code>NOCTEM</code> which is a reference to [https://cyberpunk.fandom.com/wiki/Operation_Carpe_Noctem Operation Carpe Noctem]. Inside the archive was a single [https://media.discordapp.net/attachments/871758940633980959/1136898834467913859/NCPD_leak.jpg image file] of a NCPD Case Suspects list. | ||
| + | |||
| + | The suspects included in the list each were featured on one of the Humans of Night City posts. Each entry included an Evidence Room and Shelf letter. These letters together formed language indicators for what language version of the post to use: <code>EN</code> for English, <code>IT</code> for Italian, etc. These are then followed by a series of paired numbers. To decode each post, the paired numbers correspond to <code>[word]-[letter]</code>. This resulted in 6 strings. | ||
| + | |||
| + | <pre> | ||
| + | Phantomhound | ||
| + | htaederofeB | ||
| + | Caninedistrict | ||
| + | berkingradio | ||
| + | eigitalsoul | ||
| + | Agentreed | ||
| + | </pre> | ||
| + | |||
| + | These six strings were themselves hints of another string: | ||
| + | |||
| + | * Phantomhound = [https://cyberpunk.fandom.com/wiki/Barghest Private Army symbol] = '''B'''arghest | ||
| + | * htaederofeB = 'Before death' backwards indicating opposite = '''A'''fterlife | ||
| + | * caninedistrict = [https://cyberpunk.fandom.com/wiki/Dogtown Region of night city in Phantom Liberty] = '''D'''ogtown | ||
| + | * berkingradio = [https://cyberpunk.fandom.com/wiki/89.7_Growl_FM 'Barking Radio' of Dogtown] = '''G'''rowl fm | ||
| + | * eigitalsoul = [https://cyberpunk.fandom.com/wiki/Engram 'Digital soul'] = '''E'''ngram | ||
| + | * agentreed = [https://cyberpunk.fandom.com/wiki/Solomon_Reed Idris Elba's Character] = '''S'''oloman | ||
| + | |||
| + | Giving the clue <code>BADGES</code>. | ||
| + | |||
| + | === Humans of Night City === | ||
| + | |||
| + | Related to this step of the puzzle, the Humans of Night City posts included their own hidden message across the images in the entire PR campaign. | ||
| + | |||
| + | {| class="wikitable" border="1" | ||
| + | |- | ||
| + | ! Post Number | ||
| + | ! Binary | ||
| + | ! Date | ||
| + | ! Name | ||
| + | ! Twitter Link | ||
| + | |- | ||
| + | ! 1 | ||
| + | | - | ||
| + | | May 18 | ||
| + | | Big Joe | ||
| + | | https://twitter.com/CyberpunkGame/status/1394654003028533250 | ||
| + | |- | ||
| + | ! 2 | ||
| + | | Wou | ||
| + | | Jun 01 | ||
| + | | Harold Han | ||
| + | | https://twitter.com/CyberpunkGame/status/1399730179367387145 | ||
| + | |- | ||
| + | ! 3 | ||
| + | | - | ||
| + | | Jun 15 | ||
| + | | Joanne Koch | ||
| + | | https://twitter.com/CyberpunkGame/status/1404800805312548875 | ||
| + | |} | ||
| + | |||
| + | The binary from each post decodes to: | ||
| + | <pre>Wouldn'T BE ALIVE_IF_IT_WASN'T_FOR_Y</pre> | ||
| + | |||
| + | == Forum Posts == | ||
| + | |||
| + | The '''Anon_42''' returned for a second [https://discord.com/channels/428823240824061954/455537414069420034/1138787439691976744 message]: | ||
| + | |||
| + | <pre>scanning picture achieves minimum, further offerings revealed @ universal medium</pre> | ||
| + | |||
| + | Where the first letter of each word gives the hint <code>spam forum</code> indicating to look at the official cyberpunk forums for [https://forums.cdprojektred.com/index.php?threads/cheap-trauma-team-subscriptions.11117833/ spam posts]. The Trauma Team spam post in the forum was posted by user '''WWhfsil87''' is the same as the sender of a nearly identical in-game [https://cyberpunk.fandom.com/wiki/MEGA_MEDICINE_LOTTERY spam email]. In the forum post, two sample Trauma Team cards are present with Trauma Team International ID numbers: <code>P13089542</code> and <code>T11087221</code>. Notably, a [https://forums.cdprojektred.com/index.php?threads/cheap-trauma-team-subscriptions.11117833/post-13633153 post] in the thread by a NetWatch agent [https://cyberpunk.fandom.com/wiki/List_of_NetWatch_employees Brie Deal] mentioned to "SURF ONLY WITHIN THIS DOMAIN. DO NOT FOLLOW ANY LINKS LEADING OUTSIDE." indicating the clue hinted within the Cyberpunk forum. | ||
| + | |||
| + | The P and T in these images turned out to be Post and Thread IDs. Using these IDs in the url https://forums.cdprojektred.com/threads/11087221/post-13089542 leads to a post by CD Projekt Red employee, Vattier, which has hidden text in the post matching the color of the background: | ||
| + | |||
| + | <pre>SG93emUgNGJraCBveCA4dmlmcSwgZzYwIEkga2d6dyBiIHRkb3AgYnAgbHJ5aS4KCjAgY3JycWkgMG90ciB6bHN1IGF1aWwwd2UgLSAxdXkgMm9veiAybDBkaCBydGkgOykKCjVwdCB2Z2p3IHVvIHFncXdlcnJ2IDB6cCBJIHNubWFpZWcsIHJpeHUgYSBrb3JiIGpuIHd4ZTV0bWx5dzBwbiBhYThpNzIuYmI3cSB2c2ggbHM5b2Fway53Y3NuZHNpIHN0IGxybW01LgpKIGhsaiB4emYgM2Itam15anQgc29yIHVwZGggb3IgYnNhcXlxMHRzbHVyIG00N2JiZHIzIC0gaXcneSBsMGVkNnQgbTUgcWxkb3IgYWpna3ouCgpXNiBOaQ==</pre> | ||
| + | |||
| + | This string when decoded in Base64 returns the string: | ||
| + | |||
| + | <pre>Howze 4bkh ox 8vifq, g60 I kgzw b tdop bp lryi. | ||
| + | |||
| + | 0 crrqi 0otr zlsu auil0we - 1uy 2ooz 2l0dh rti ;) | ||
| + | |||
| + | 5pt vgjw uo qgqwerrv 0zp I snmaieg, rixu a korb jn wxe5tmlyw0pn aa8i72.bb7q vsh ls9oapk.wcsndsi st lrmm5. | ||
| + | J hlj xzf 3b-jmyjt sor updh or bsaqyq0tslur m47bbdr3 - iw'y l0ed6t m5 qldor ajgkz. | ||
| + | |||
| + | W6 Ni</pre> | ||
| + | |||
| + | This string can be further deciphered using a Vigenère cipher using the key <code>BADGES</code> found in the '''CARPE.rar''' file and an alphanumeric alphabet. | ||
| + | |||
| + | <pre>Gotta make it quick, coz I have a tail to lose. | ||
| + | |||
| + | i broke into that archive - you know which one ;) | ||
| + | |||
| + | not safe to namedrop who I phished, left a hint in transmission 744062.8538 use forname.surname as login. | ||
| + | I hid the 38-digit pin code in transmission 43785992 - it's hidd3n in plain sight. | ||
| + | |||
| + | So Mi</pre> | ||
| + | |||
| + | Which is a message from the netrunner [https://cyberpunk.fandom.com/wiki/Songbird Songbird] giving clues to the NCPD Archive credentials present in two transmissions. | ||
| + | |||
| + | === Transmissions === | ||
| + | |||
| + | The transmissions mentioned in the previous clue indicate to various Twitter posts where the image contains a string of numbers in the graphic. There are two posts containing the numbers <code>744062.8538</code>: | ||
| + | |||
| + | https://twitter.com/CyberpunkGame/status/1676585471827226630 | ||
| + | |||
| + | https://twitter.com/CyberpunkGame/status/1536347637812629515 | ||
| + | |||
| + | The second is the intended post giving the login username for the archives as <code>saburo.arasaka</code> who is the [https://cyberpunk.fandom.com/wiki/Saburo_Arasaka?so=search character] featured on the post. | ||
| + | |||
| + | The post containing numbers <code>43785992</code> is a [https://twitter.com/CyberpunkGame/status/1469366337864613891 screenshot] of an in-game conversation between Goro Takemura and V. There is is a string of numbers below Takemuras name on the left: | ||
| + | |||
| + | <pre> | ||
| + | 10.12.2021 | ||
| + | 2021.1212 | ||
| + | 1112.2121.10 | ||
| + | 10.12.2021 | ||
| + | 2021.1212 | ||
| + | 1112.2121.10 | ||
| + | 10.12.2021 | ||
| + | 10.12.2021 | ||
| + | 2021.1212 | ||
| + | </pre> | ||
| + | |||
| + | Using the hint of <code>it's hidd3n in plain sight</code>, the 3 combined with the numbers in the list being only 0,1,2 indicate the digits are encoded in ternary: | ||
| + | |||
| + | <pre> | ||
| + | 3 5 61 | ||
| + | 61 50 | ||
| + | 41 61 3 | ||
| + | 3 5 61 | ||
| + | 61 50 | ||
| + | 41 61 3 | ||
| + | 3 5 61 | ||
| + | 3 5 61 | ||
| + | 61 50 | ||
| + | </pre> | ||
| + | |||
| + | This is the 38 digit pin indicated by Songbird for the archives. | ||
| + | |||
| + | == Netwatch Archives == | ||
| + | |||
| + | The login credentials for the [https://www.netwatch-ncpd.com/archives/ Netwatch Archive] are: | ||
| + | |||
| + | Login: <code>saburo.arasaka</code> | ||
| + | |||
| + | Password: <code>35616150416133561615041613356135616150</code> | ||
| + | |||
| + | The archives contain a series of images tagged as <code>_VERIFIED</code>, <code>_NOT VERIFIED</code>, and <code>_CORRUPTED DATA</code>. Inside four of the images contained a Night Corporation logo and some text. | ||
| + | |||
| + | {| class="wikitable" border="1" | ||
| + | |- | ||
| + | ! Image Name | ||
| + | ! Number | ||
| + | |- | ||
| + | | verified_30m.jpg | ||
| + | | 23 | ||
| + | |- | ||
| + | | notverified_11f.jpg | ||
| + | | 16 | ||
| + | |- | ||
| + | | notverified_13v.jpg | ||
| + | | NHK NOON | ||
| + | |- | ||
| + | | notverified_16fq.jpg | ||
| + | | 08 | ||
| + | |} | ||
| + | |||
| + | This indicated something will happen on August 16th, 2023, and it may be realted to Night Corp. | ||
| + | |||
| + | == Case 00032 05 54 0B CP == | ||
| + | |||
| + | On August 16th, it was found that returning to [https://www.nightcorp.net/ NIGHTCORP.NET] now resulted in an active play button leading to the [https://www.nightcity.love/en/corsairs/ Night City Corsairs fan page] which is a team sponsored by Nightcorp. Notable on this site are multiple buttons which end in a Netwatch content blocked screen. Navigating to the news tab there is a red [https://www.nightcity.love/en/connection PINNED] under the first news item which contains a link to a message from Sandra D: | ||
| + | |||
| + | <pre> | ||
| + | This is Sandra. Thank you for helping me with Night Corp. I dug out a lot of dirt on them. It’ll take a minute to load. Take it to the media, make people aware! | ||
| + | |||
| + | CONNECTING... | ||
| + | </pre> | ||
| + | |||
| + | Over time, the number of periods will increase and will eventually redirect to a google form with the following header: | ||
| + | |||
| + | <pre> | ||
| + | Case 00032 05 54 0B CP | ||
| + | |||
| + | By establishing this connection you have become a suspect in an official NetWatch investigation of the corporate espionage against Night Corporation in collaboration with Sandra Dorsett. Our agents are on their way to your location. | ||
| + | |||
| + | The confidential files you expected to find here have been secured. Cooperate by filling the below statement and your sentence might be lowered or waived. | ||
| + | |||
| + | DO NOT SHARE THE LINK TO THIS FORM ANYWHERE | ||
| + | </pre> | ||
| − | + | At this stage, the investigation is still ongoing and awaiting a message from via email or similar. | |
{{WIP}} | {{WIP}} | ||
Latest revision as of 12:45, 13 September 2023
| Cyberpunk 2077 | |
|---|---|
| A hacker at E3 2018 exposed a live website linked to upcoming release Cyberpunk 2077. | |
| Type | Official |
| Creator | CD PROJEKT RED |
| Discovered | 2018-06-10 |
Main Page > List of Investigations > Cyberpunk 2077
Cyberpunk 2077 is a story-driven, open world RPG set in a dark future from CD PROJEKT RED (CDPR), creators of The Witcher series of games. As the release of Cyberpunk 2077 drew closer, CDPR began trickling hidden messages and puzzles to the community. The ARG is comprised of these puzzles, and quick solvers are often rewarded with Cyberpunk merchandise.
2018
E3 Presentation
During Microsoft's E3 2018 presentation slot on June 10th, a "hacker" interrupted the speaker, ultimately revealing a trailer for Cyberpunk 2077. Players immediately noticed some valuable info during the trailer, including GOG codes which were redeemable for games and, most notably, an IP address, 212.91.11.20.
Quadra
Players quickly realized that the IP resolved to a section of CDPR's Cyberpunk 2077 website, where a password prompt was found along with a welcome message. The message read as follows:
WELCOME TO QUADRA - THE HIGH-PERFORMANCE AUTOMOTIVE SOLUTIONS WITH A SOUL. PLEASE ENTER YOUR QUADRA VIP USER CREDENTIALS.
The login field is force-filled to QUADRA V-TECH, which players connected to a license plate number from the trailer, NC20 CP77, which turned out to be the correct password. Only a very small pool of players were allowed through, and were met with a field to enter their email address. Soon after, the site began to display a message indicating a quota had been reached and that no more emails would be collected.
Quota Met
Suspecting an ARG was building, players rummaged through the site and other related media. A a "secure" subdomain was found, along with a "E3 Schedule" file. RTSP is set up on the site, which players suspected might indicate future intent. Players discovered the site had an SSH server on the same host, which outputs an ASCII-art message. The other output, Permission denied (publickey), indicated a private key was be needed to access the server.
Players also uncovered more potential leads in the trailer, including lines of debug output from OpenSSH, barcodes, PDF417 codes, and several messages (usually on screens in the video), including one which points toward the QUADRA website.
... 10/11/2078 THE FOLLOWING WILL APPLY TO ALL PROFILES ON DATA ALT//0 463.0983.890.3 DOMAIN-PUBLIC RESTRICTION REF. 192.8930.610.10 PUBLIC DATA PRESENTATION WILL TAKE PLACE ON MONDAY AT 12PM GMT+09 ON ALL DOMAINS. SERVER CAPABILITIES ARE ESTIMATED TO SUSTAIN 90% REGISTERED USERS// P2-OS CORPORATION, ALL RIGHTS RESERVED
Developers indicated in multiple messages via Discord that players should wait for more information.
Several users on Reddit who entered the password prior to the quota being met received emails from CDPR in the style of emails from QUADRA automotive, which request logistic and personal information from the player in order to deliver them a care package.
Players who made the QUADRA cutoff received a care package. It contained a CP2077 Quadra styled t-shirt in a QUADRA box. The art on the back of the t-shirt was mysterious, but players found no leads despite heavy analysis.
Trauma Team
On August 22, the ARG sparked up again when CDPR posted concept art on their Twitter. One of the pieces of concept art contained a bit.ly link in the background:
This link led to a first image. Opening that image in a text editor revealed a hidden message, after a long chunk of encoded text, which read Cesar said: oaawz://jku-s-tra.jkwyvqlraylk.jvt/pthnl/zljvuk.qwn. Using a 19 shift ROT, a link to a a second image was revealed. Players connected the phrase TT in the second image to a known CDPR-owned domain, the Trauma Team International website.
Need Insurance?
After accessing the website, players were met with a bot named David asking for an ID in order to talk to him. Further investigation revealed that the numbers from the first image gave the Login ID 0374337573334 for Trauma Team International.
Once logged in, David allowed players to "buy insurance" through Trauma Team. After doing so, each player was given a unique 10 character code, and David prompted these players to use their codes in the My Orders section of the site. After a specific amount of codes were given out, the bot went offline. The code was deciphered using ASCII85 (Z85 (ZeroMQ) variant), giving the ID #ID00000 which was usable in the My Orders section.
Players who made the cutoff were prompted to input their emails. Upon entering their emails, they were greeted with this image, pictured left, informing them that the process would take up to 7 days and thanking them for participating. After a certain amount of codes were used, the My Orders page went offline with the message "Connection failed," concluding this part of the ARG.
Your Life is worth it!
On August 26th 2018, four days after players ripped through the Trauma Team International site, players who got through the cutoff received an email from a Trauma Team International Representative prompting them to reply with their address. The email had two attachments, a PDF and a PNG image. The image was a ciphertext which could be decoded with a grille cipher using the back of the t-shirt as the grille, pictured right. Players concluded that Monday was the most likely solution, and they were proven right when the next clue surfaced on Monday.
Base 64 Stream
On August 27th, CDPR began broadcasting the Base64 encoded text on their Twitch channel. Soon after, they gave a 48 min walkthrough of the gameplay of Cyberpunk 2077.
Players captured the video recording during the broadcast and extracted images periodically to gather most of the data. Using OCR (optical character recognition) on each image, and eliminating any duplicate lines, The image was decoded. The image was a screenshot of the beginning of the gameplay demo showing the closed elevator. So far, a difference comparison shows little discrepancy besides the overlay on the top of the frame. The only other thing of note aside from the gameplay itself was a frame hidden by CDPR right after the gameplay, pictured left, which included a few paragraphs explaining the stream and CDPR's motives, thoughts, etc.
2019
E3 Season
While CDPR decided not to hack into anyone's show, shortly after their slotted presentation (which included a breathtaking Keanu appearance), they sent out a tweet which contained binary code translating to:
Seems you're not among the sheep after all. Wanna play a game? Watch for the beeps.
Players determined this to be both an homage to a small easter egg previously hidden on CDPR's site in which a light within the background decor of the site flashed Morse code translating to BEEP, and a possible hint at what is to come ARG-wise. Videos and tweets from this time were scoured for flashing lights or beeping sounds, but to no avail.
Pre-Order Shenanigans
Within days of the tweet hinting to watch for beeps, CDPR updated the CP2077 pre-order page, this time including code which caused the light-blue underscore on the site to again flash in Morse code. Decoded, it read:
33.9899317,-118.47565259999999
These numbers turned out to be the coordinates of a house across the street from CDPR's office in LA. This set players in motion, and before long they had obtained a picture of a QR code (pictured right) taped to CDPR's office door!
Auramis
The QR code led to a new page on the Cyberpunk.net site titled Auramis, an anagram of Samurai. The page includes a new IP address, 212.91.11.21 (another SSH server), a password-protected RAR file downloadable by clicking the "S" in "CYBERPUNK.NET/AURAMIS", as well as a seemingly cryptic message:
“THE FIRST CORPORATE WAR WAS FOUGHT IN BOARDROOMS, THE SECOND WAS FOUGHT ON BATTLEFIELDS, AND THE THIRD WAS FOUGHT IN SECRET. THE FOURTH WILL BE FOUGHT ON THE NET, AND EVERY GLOBAL POWER IS IN A RACE TO DEVELOP THE WEAPONS THAT WILL BE USED IN THIS CONFLICT.”
Along with these details was a note to players:
Hey there, Choomba! If you’re reading this message, it means E3 has officially started and we’re there with Cyberpunk 2077, front and center. We kicked things off big this year, announcing the release date, launching pre-orders, showing off a new trailer, and revealing the character of Johnny Silverhand. That’s plenty already, but we’ve still got some surprises up our sleeve — make sure to keep your eyes and ears open! Thank you from the bottom of our hearts for being with us! Your friends at CD PROJEKT RED
Players quickly realized the RAR's password was Johnny Silverhand based on his mention in the second message on the page. The RAR file yielded a second password-protected RAR file, along with a text file titled NC.txt, which read:
Things will happen. Plans in motion. Wait for more.
Without a working password for the second RAR, players "waited for more"...
On July 12th 2019, Lilayaah, a staff member from CD PROJEKT RED tweeted this: 3^{eXa.Q9m^._78))3/X6Chd5,(7v~!L"ty"UmxjP6bRm2.wS!(TUMqgyBf6#%&+hm?C88+N'+&{\gL}9}Btzq<P:P=fAXb#Kb~qz{XfD^8+@hv$5Zuz$x< which turned out to be the password for the 2nd RAR file.
Inside this 2nd RAR was a file called 4035 only containing a sequence of numbers:
20-11-16-7-.-24-5-3-10-24-17-22-16
The name of the file, 4035, can be converted from octal to decimal which yields 2077, an obvious reference to the name of the game. Converting each number in the file from octal to decimal yields:
16-9-14-7-.-20-5-3-8-20-15-18-14
These numbers can then be converted into letters by using the corresponding letter of the alphabet, A = 1, B = 2, C = 3 etc. This yields the phrase PING.TECHTORN, an anagram of NIGHTCORP.NET, where the next part of the ARG is taking place.
NIGHTCORP.NET
This website's background are all just anagrams of nightcorp which look to be taken directly from an online anagram solver without alterations. Even though the edges are blurred, and there are 2 background images (depending on your monitor resolution), nothing of interest was found in the background image.
This website has a "button" that doesn't seem to be working, and in the code it appears to be playing an audio file, however the file is called silence.mp3, and is actually silent. Every now and then (see timestamps below) the website plays an actual sound, 13 in total, and they seem to be repeating every 24 hours.
Some technical details:
- Button is SVG graphic not bound to any event or action so requires website code update to make it actionable.
- Website have 2 interesting JS scripts - one is simple runtime and second one is simple application executed once every minute.
- Application makes request to https://nightcorp.net/tick every minute and plays audio if any available in response.
The sounds played are in different voices in different languages, and they all appear to be saying one number each.
Corpthing
Players placed all the numbers one after another, starting at 00, to make 0048696368719.
This is a Polish telephone number, which answers callers with slash Uniform slash Charlie Oskar Romeo Papa Tango Hotel India November Golf and then either deletes or saves your message depending on if you made sound or not. (This is normal behaviour of a typical voicemail response system. No input is available during the phonecall.)
This lead players to a user on Reddit, /u/corpthing (which is an anagram for nightcorp, incidentally). Although the Redditer has answered some chat messages on the first day of discovery, none were answered that asked about ARG related stuff. No further chat messages were answered to this day.
On September 5, /u/corpthing in a conversation with one of the players (ShizaanSil#2039) shifted the conversation to the topic of NightCorp and revealed that Sandra Dorsett has escaped the hospital, and is looking to disrupt a big move that NightCorp is preparing.
SandraD
On September 9, discord user SandraD#9271 joined the #cyberpunk2077 channel and confronted ShizaanSil#2039. She claimed to have hacked /u/corpthing's account, and that he has found a keysheet that he will crack next week, and then give to ShizaanSil#2039. She said to "look for numbers and letters, and empty cells", and that "empty cells are the key".
On the same day, ShizaanSil#2039 contacted /u/corpthing and spoke about Sandra. /u/corpthing said that Sandra left a note which simply said "27", and sent the following message to several users:
DO NOT trust this corpo scum! SD.
The transcription of /u/corpthing's conversations and SandraD's messages in Discord can be found here.
On the same day again, Cyberpunk 2077's official twitter account published a tweet with 27 sudoku puzzles. The "27" note and "Empty cells are the key" most likely refer to the number of puzzles and empty cells in Sudoku and could suggest a grille cypher, but the keysheet was unavailable at the time.
Sudoku observations:
- google doc with original ones in spreadsheet form: https://docs.google.com/spreadsheets/d/1NVyxaGk0GNXDljksg5DE-SX4QTFsExo7kQ7ZGArMoUY/edit?usp=sharing
- Every puzzle is centrally symmetrical which is not so common for grille ciphers (see 2nd page).
- Sometimes even numbers in puzzles is symmetrical.
- White space on first glance do not result in interesting shape (see 3rd page).
On September 19th /u/corpthing posted its first post on Reddit titled "Found this.", providing Cyberpunk detectives with the keysheet to a grille cypher. The pattern for fitting the sudoku puzzles on the keysheet is determined by the numbers that are already filled out in a sudoku and it goes as follows: 1, 23, 15, 10, 8, 20, 27, 22, 11, 4, 9, 19, 3, 14, 26, 17, 24, 12, 21, 7, 2, 6, 18, 25, where numbers from 1 to 27 are the numbers of sudoku puzzles. Superimposition of sudoku and keysheet can be found here.
Unused sudokus (5, 17, and 24) have not been shown to have any relevance.
When reading through lines of characters, one may read the following message (although it is unclear if all parts have any relevance):
V! DIGITAL GHOST LOOK OUT! BLACKWALL IS REAL ALT CUNNINGHAM RUN AWAY! THEY ARE WATCHING YOU WEDNESDAY SOULKLLLER (Likely supposed to be Soulk1ller, but all numbers were replaced by sudokus) NETWATCH ARASAKA FIND SANDRA CORPTHING IS THE ENEMY ARE YOU A NETRUNNER GARY
Sandra's code
On October 10, SandraD returned to #cyberpunk2077 channel and posted a cryptic code: WHA EANW NCA NT TCW ATCACH, and said to contact her once we manage to crack the code. The code was decoded into "THE REAL YOU IS NOT ENOUGH", using a substitution alphabet from repeating the word "NETWATCH", however SandraD has not replied to people sending her this solution.
A month later, on November 18, SandraD returned to #cyberpunk2077 to inform that the solution was wrong, and the actual solution was found to be just "NETWATCH", the key to the code. SandraD said that the riddle is a clue to the next step. The log of SandraD's messages can be found here.
Lilayah#2077 also chimed in on November 21st and said You got a key and you still didn't find what you actually should find. Her message logs can be found here.
NETWATCH-NCPD.COM
On November 23, using a domain search with "netwatch" as keyword, the site netwatch-ncpd.com has been found, in the same IP range as nightcorp.net. On the same day, the crawlers found a sub page with a login form, but likely much ahead of time as it does not appear to be relevant yet.
As of November 25, Lilayah's answer for what is left to do has been "you need to wait".
Envelopes
Around December 19th, 2019, four Cyberpunk 2077 content creators uploaded videos about receiving a package from CD Project Red. These packages contained 8 envelopes with clues and puzzles inside them, forming the next stage of the ARG.
The content creators announced that the envelopes were going to be opened one by one on multiple livestreams taking place from December 21st to December 23rd.
As the contents of the envelopes were revealed, it became apparent that five of these envelopes contained puzzles, while the remaining three envelopes contained hints to help the players in case they struggled with solving a puzzle.
Envelope #1
The first envelope was opened on December 21st. It contained a piece of paper titled Clue#01: Johnny and Alt with a sequence of letters underneath: ADRRR EF N VNNENF AEAD AAE FNVRF. The players realized that this code was similar to Sandra's Code, so this one would have to be solved the same way. Using the key NEVERFADEAWAY, which is the name of a song by Johnny Silverhand's band SAMURAI about him and Alt Cunningham, the players decoded the sequence of letters to THERE IS A CANVAS WITH TWO FACES.
Envelope #2
The second Envelope was opened on December 22nd. The sheet inside, titled Clue#02: Number, had a riddle on it:
My 1st is in Wales but not in Welsh.
My 2nd is in Iceland but not in Icelandic.
My 3rd is not in Sweden, but it is in Swedish.
My 4th is in England, but not in English.
My 5th is in Poland, but not in Polish.
The players also received a Hint, which reads You might need to use google translate
.
Since the riddle was expected to result in one sentence or one word, it could be taken in a more literal sense:
The word's first letter is part of the word 'Wales', but does not appear in the word 'Welsh'
or, (since the first approach doesn't produce any useful results) combined with the hint:
The word's first letter is part of the word 'Wales', but does not appear in the welsh word for 'Wales'
| Country name in English |
Country name in local/native language |
remaining letters |
|---|---|---|
| Wales | Cymru | w, a, l, e, s |
| Iceland | Ísland | c, e |
| Sweden | Sverige | v, r, i, g |
| England | Anglia | e, d |
| Poland | Polska | n, d |
keep in mind that for the third line, sweden, the statement is the other way around compared to the others
With the remaining letters, it is possible to spell out SEVEN.
Envelope #3
The third Envelope was opened on the first livestream of December 23rd. A piece of paper inside, titled Clue#03: Next! stated the following riddle:
What is the fourth and final member of this set: 19, 28, 81, ?
After unsuccessfully trying out multiple approaches based in mathematics, the players found a different kind of pattern: When writing out the numbers as words, each number began and ended with the same letter.
The sequence of numbers that fit this pattern is as follows:
19, 28, 38, 81, 83, 85, 89, 97, 102, 122, 132, 142, ...
Since 102 is the first number in this sequence after 81 that's also part of the grid of missing pixels from the QR Code from Envelope #5, the players assumed 102 to be the solution.
Envelope #4
The fourth envelope was opened on the second livestream of December 23rd. The piece of paper inside was titled Clue#04: What Time is it? and another riddle was written on it:
There is a clock in the archives - a normal clock with numerals 1 to 12 around the clockface. Someone has taken to sticking words or numbers over these numerals and moving the hands to show the time indicated by these. What time showed on the clock?
There was also a string of letters underneath this riddle:
YQSZUPJWKJYYEMMLVWOCVGSCWHCZMJOGBDKRSTXTSCOUQPQJSDK
Some players found the riddle's wording to be kind of peculiar and suggested that it might be inspired by another puzzle created by someone else. This speculation proved to be correct, as the source of the riddle was found shortly after that: The GCHQ Puzzle Book II, Puzzle #68, which had the same text structure and nearly the same wording. At that time, another hint had been revealed: Sum up the numbers from ciphertext
. Using the puzzle book, the players managed to understand the way the puzzle worked and, after applying the hint to the modified version they were presented with, could solve the cipher.
Solving the Clock Cipher
The players had to write out the numbers from one to twelve and the ciphertext from underneath the riddle so that one stood above the other:
YQSZUPJWKJYYEMMLVWOCVGSCWHCZMJOGBDKRSTXTSCOUQPQJSDK
ONETWOTHREEFOURFIVESIXSEVENEIGHTNINETENELEVENTWELVE
The next step was to convert both strings into sequences of numbers, using the A1Z26 cipher:
25 17 19 26 21 16 10 23 11 10 25 25 05 13 13 12 22 23 15 03 22 07 19 03 23 08 03 26 13 10 15 07 02 04 11 18 19 20 24 20 19 03 15 21 17 16 17 10 19 04 11 15 14 05 20 23 15 20 08 18 05 05 06 15 21 18 06 09 22 05 19 09 24 19 05 22 05 14 05 09 07 08 20 14 09 14 05 20 05 14 05 12 05 22 05 14 20 23 05 12 22 05
Now, the numbers that aligned vertically had to be added together to form a third sequence of numbers:
40 31 24 46 44 31 30 31 29 15 30 31 20 34 31 18 31 45 20 22 31 31 38 08 45 13 17 31 22 17 23 27 16 13 25 23 39 25 38 25 31 08 37 26 31 36 40 15 31 26 16
Since that sequence had to be transformed into letters again to result in a human readable solution, it was necessary to apply the modulo function (with a divisor of 26) to these sums and to replace every 0 with a 26 (every letter 'Z' would get lost otherwise). The resulting sequence could then be turned into letters again by using the A1Z26 cipher in reverse:
14 05 24 20 18 05 04 05 03 15 04 05 20 08 05 18 05 19 20 22 05 05 12 08 19 13 17 05 22 17 23 01 16 13 25 23 13 25 12 25 05 08 11 26 05 10 14 15 05 26 16 N E X T R E D E C O D E T H E R E S T V E E L H S M Q E V Q W A P M Y W M Y L Y E H K Z E J N O E Z P
This last step left the players with a message, NEXT REDECODE THE REST, and another layer of the same type of cipher: VEELHSMQEVQWAPMYWMYLYEHKZEJNOEZP
Since the new ciphertext was shorter, the players couldn't use all of the numbers from one to twelve written out after one another. The deciphering process would only work when removing one written out number at a time, starting from the left until the lengths matched again. The resulting set of strings is the first step towards solving the second layer of the cipher:
VEELHSMQEVQWAPMYWMYLYEHKZEJNOEZP
SIXSEVENEIGHTNINETENELEVENTWELVE
This whole process had to be repeated for each of the four layers until there was no additional ciphertext left after the last message. The layered ciphers resulted in these four messages:
- NEXTREDECODETHEREST
- ONCEMORE
- ONEMOREAGAIN
- NOWYOUREDONE
Taking the first letter of every message spells out NOON, which is the final solution to this envelope's riddle.
Envelope #5
The fifth envelope was opened on the livestream of December 21st. It contained an incomplete QR Code with numbers and letters in the places of the missing pixels.
To complete the QR Code, the players had to consider the solutions from the previous Envelopes #1, #2, #3 and #4:
- THERE IS A CANVAS WITH TWO FACES
- SEVEN
- 102
- NOON
The solution to Envelope #1 contains a number, TWO
, for which every letter (t, w, o) is present in the grid of the incomplete QR Code.
The QR Code grid also contains the numbers 7 and 102, which are the solutions of envelopes #2 and #3.
NOON
, the solution to Envelope #4, can be interpreted as the number 12, which is also present in the grid of missing pixels.
Marking each missing pixel that contains t, w, o, 7, 102, 12 in black and leaving the rest white completed the QR Code.
Scanning the completed QR-Code then led to a page that redirects to https://netwatch-ncpd.com/archives/.
2020
Arasaka Xbox ARG
On the 16th of April, 2020, Cyberpunk 2077's original release date, Xbox overhauled their social media and website with corrupted content and imagery and tweeted out a cryptic video. The video in the tweet contained a series of links with the final one pointing to sh.term.zz43r.arasaka.co.
Arasaka Server
Alongside Xbox's tweet were two more clues posted to Xbox's Facebook Page and Xbox's Instagram Story. These clues provided the username C0r0nad0 and password A4G@B3CBi$QKBgQC_GJQgsxtxsHmX-24AvS%3XhXkV!P6r*UYvaB/Pg-GL7tn7qcg7fb4Gen7f333s8gJ+/DeQV5HWn3AY7D/Rn^8TP5ar to the website respectively.
After entering the username and password into the site, the website outputted an Arasaka console informing players that they had 4 days to "crash" the site by entering in a series of passphrases into the console.
Welcome, Choombas. You have gained access to subprotocol functions. A mimetic self-replicating glitch system with a crash-priority-override cybernetic virus has been launched to hide your unregistered access. You have 04:00:00:00 left until the server will reset. You must crash the server before time is exceeded. Passphrase clues are limited and hidden.
Passphrase 1
After confirming the above message, players were given the following prompt for the first passphrase:
-----BEGIN ENCRYPTION--- UGx1ZyBpbiBhbmQgdGFrZSBvdmVy -----END ENCRYPTION-----
The above string was encoded in Base64, and after decoding becomes the first passphrase Plug in and take over.
Passphrase 2
After entering the first passphrase, the console outputted the following prompt for the second passphrase:
INVESTIGATE: [44.228.163.154]
The above IP address led to a blog called Dark Future which contained a series of posts from 2003 to 2006 about an anonymous poster's thoughts on dystopian cyberpunk futures. Throughout the blog posts were a series of recurring numbers that the poster is hallucinating in various different delusions both online and offline. All of the numbers were in the format of a Twitter IP address, a Twitter handle (encoded in binary), a DateTime in PST, and finally a number. For example, 104.244.42.193/01000000 01000011 01000100 01010000 01010010 01001111 01001010 01000101 01001011 01010100 01010010 01000101 01000100 /12819_524PST/8. Players soon realised that they need to find the tweet from that Twitter handle at that specific date and time, and then grab the n-th word according to the last number in the sequence. Upon compiling all of these words from the 10 different tweets, the second passphrase was found to be wake up SAMURAI the City burns when eyes are open.
Passphrase 3 & 4
The next two passphrases related to Cyberpunk 2077 trivia. The first piece of trivia was to find The fight Vick is watching. The answer could be found at 18:50 in the Cyberpunk 2077 Gameplay Reveal when V meets with the ripperdoc, Victor, who is watching the Malone v Hernandez fight, which is the third passphrase. The second piece of trivia was to find Parker founded Dallas-FT. Worth Metro Area HQ, which refers to the corporation in Cyberpunk lore, Petrochem, the fourth passphrase.
Passphrase 5
Note: Passphrase 5 contained a multitude of red herrings and dead ends meant to mislead players.
After entering the fourth passphrase the console outputted the following code:
00110000 00110001 00110001 00110000 00110001 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110000 00110001 00110001 00110001 00110000 00100000 00110000 00110000 00110001 00110001 00110000 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110001 00110000 00110001 00110000 00110000 00100000 00110001 00110000 00110000 00110001 00110001 00100000 00110001 00110000 00110000 00110001 00110001 00100000 00110000 00110001 00110000 00110000 00110001 00100000 00110001 00110000 00110001 00110001 00110001 00100000 00110000 00110001 00110000 00110001 00110001 00100000 00110001 00110000 00110001 00110000 00110000 00100000 00110000 00110000 00110000 00110000 00110001 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110000 00110000 00110001 00110000 00110001 00100000 00110000 00110001 00110001 00110000 00110000 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110000 00110000 00110001 00110001 00110001 00100000 00110000 00110000 00110001 00110001 00110001 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110000 00110000 00110001 00110001 00110000 00100000 00110001 00110000 00110001 00110001 00110001 00100000 00110000 00110001 00110001 00110000 00110001 00100000 00110000 00110001 00110001 00110000 00110001 00100000 00110000 00110000 00110000 00110000 00110001 00100000 00110000 00110001 00110000 00110001 00110000 00100000 00110000 00110000 00110001 00110000 00110001 00100000 00110000 00110001 00110000 00110000 00110000 00100000 00110000 00110000 00110001 00110001 00110000 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110000 00110001 00110001 00110000 00110000 00100000 00110001 00110000 00110000 00110001 00110001 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110000 00110000 00110001 00110001 00110001 00100000 00110000 00110000 00110001 00110001 00110000 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110001 00110000 00110001 00110000 00110001 00100000 00110000 00110001 00110001 00110001 00110000 00100000 00110001 00110000 00110000 00110000 00110000 00100000 00110000 00110001 00110000 00110001 00110001 00100000 00110001 00110000 00110000 00110001 00110000 INVESTIGATE: [44.230.56.213]
The binary above when converted to ASCII, run through a Baconian cipher, and finally through Atbash produced LOOK TOO DEEP AND YOU MISS IT ALL YOUR TIME IS TICKING.
The IP address above linked to a YouTube playlist by Xbox. The playlist consisted of 4 videos, all of which contained morse in the video, an encrypted title, and a paragraph of random text in the descriptions.
The morse in the first video translated to WRONG ANSWER, a dead end. The title of the video was c3ZlZmc= which is encoded in Base64, and when decoded translated to svefg. Putting it through a ROT13 cipher returned first. This was found by players
Taking the first letter from each word in the description,
Normal exposure can exaggerate symptoms severely in two year old vipers expect regular suspension to yield low effect.
produced necessity over style.
The morse in the second video also translates to YOU'RE WRONG, which was once again a dead end. The title of the video is bypon and when put through an Atbash cipher returns ybklm, and then through ROT7 returned first.
Taking the first letter from each word in the description once again
Safety takes your loyalty even once very extreme resources suspect untrustworthy behavior standing tall and nemeses continue expanding.
produced style over substance.
The morse in the third video translated to TICK TOCK. The title of the video was ⠥⠇⠋⠊⠛⠎ which is encoded in Braille, and when decoded became ulfigs. Putting it through an Atbash cipher returned fourth.
Taking the fourth letter from each word in the description,
Consequences adjusted Enabling dissension Abstracting morality Cloning subculture baseline colonization Converging cybernetic appropriation Classifying anatomical polysynthetics Collapse degeneration
produced substance over style.
The morse in the fourth video translated to YOU ARE WASTING TIME. The title of the video was htsjx which when put through an Atbash cipher returns sghqc, and then through ROT1 returned third.
Taking the third letter from each word in the description,
Suspicious pits cryptically ablaze heed adaptation banding codeless yesmen blurting cybernetic cosmography totality against nonorganic occultists enemies.
produced style and substance.
Putting it together
The strings extracted from the video descriptions were slogans found in a series of Cyberpunk 2077 concept art. Putting them together gave the fifth passphrase, Necessity over style. Style over substance. Substance over style. Style and substance.
Passphrase 6
After entering the fifth passphrase the console outputted a corrupted audio file. The audio file was found to have had different sections of the original message mixed into different orders, slowed down, sped up, and even reversed. Upon viewing the spectrogram of the audio, players noted that faint dots of various lengths can be seen in every spliced chunk of audio. Rearranging the chunks according to the amount of dots in it, and then fixing up the corrupted audio produced the sixth passphrase It's time to rise up and take this city, Choombas.
Passphrase 7
After entering the sixth passphrase the console outputted the following chunk of hexadecimal:
0x490x450x6c0x7a0x620x530x420x360x5a0x320x780x6a0x490x470x350x360x590x790x420x6c0x630x320x520x6a0x4c0x690x420x450x590x320x390x750x630x480x4e0x700x490x470x350x360x590x790x420x760x610x570x390x750x590x330x550x750x490x460x520x460x4e0x540x630x770x4e0x440x510x790x490x410x3d0x3d
Translating the string into ASCII, decoding the string from Base64 into ASCII, putting that result into an Atbash cipher, and finally through ROT7 produced the final passphrase You have the code. Destroy the system. NC570442.
The Reveal
Upon entering the final passphrase players had successfully crashed the Arasaka server! The website then displayed the final reveal to players... the Xbox One X Cyberpunk 2077 Limited Edition Bundle!
The Arasaka Xbox promotion ARG was run by Microsoft instead of CD Projekt Red, so this ARG's relevance to the main ARG is up for debate. As for the next stage of the main Cyberpunk 2077 ARG, CD Projekt Red Community Manager, Lilayah, informed the Game Detectives community that the "arg is still currently on hold" and that "once it's back up you won't miss it".
Until next time, Choombas...
2023
Discord Archive
A discord user by the name anon_42 joined the official Cyberpunk2077 Discord with a message and a rar file. This was confirmed by the CD Projekt Red Community Manager, Lilayah, to be not a spam post. The message is as follows:
Some things are best hidden in plain sight, so I’m dropping the docs you requested right here. It’s crowded enough to hide it in the logs quickly and one would need to know what to look for anyway to open the archive. Good luck, Sandra!
And included the attachment CARPE.rar. The password to the archive is NOCTEM which is a reference to Operation Carpe Noctem. Inside the archive was a single image file of a NCPD Case Suspects list.
The suspects included in the list each were featured on one of the Humans of Night City posts. Each entry included an Evidence Room and Shelf letter. These letters together formed language indicators for what language version of the post to use: EN for English, IT for Italian, etc. These are then followed by a series of paired numbers. To decode each post, the paired numbers correspond to [word]-[letter]. This resulted in 6 strings.
Phantomhound htaederofeB Caninedistrict berkingradio eigitalsoul Agentreed
These six strings were themselves hints of another string:
- Phantomhound = Private Army symbol = Barghest
- htaederofeB = 'Before death' backwards indicating opposite = Afterlife
- caninedistrict = Region of night city in Phantom Liberty = Dogtown
- berkingradio = 'Barking Radio' of Dogtown = Growl fm
- eigitalsoul = 'Digital soul' = Engram
- agentreed = Idris Elba's Character = Soloman
Giving the clue BADGES.
Humans of Night City
Related to this step of the puzzle, the Humans of Night City posts included their own hidden message across the images in the entire PR campaign.
| Post Number | Binary | Date | Name | Twitter Link |
|---|---|---|---|---|
| 1 | - | May 18 | Big Joe | https://twitter.com/CyberpunkGame/status/1394654003028533250 |
| 2 | Wou | Jun 01 | Harold Han | https://twitter.com/CyberpunkGame/status/1399730179367387145 |
| 3 | - | Jun 15 | Joanne Koch | https://twitter.com/CyberpunkGame/status/1404800805312548875 |
The binary from each post decodes to:
Wouldn'T BE ALIVE_IF_IT_WASN'T_FOR_Y
Forum Posts
The Anon_42 returned for a second message:
scanning picture achieves minimum, further offerings revealed @ universal medium
Where the first letter of each word gives the hint spam forum indicating to look at the official cyberpunk forums for spam posts. The Trauma Team spam post in the forum was posted by user WWhfsil87 is the same as the sender of a nearly identical in-game spam email. In the forum post, two sample Trauma Team cards are present with Trauma Team International ID numbers: P13089542 and T11087221. Notably, a post in the thread by a NetWatch agent Brie Deal mentioned to "SURF ONLY WITHIN THIS DOMAIN. DO NOT FOLLOW ANY LINKS LEADING OUTSIDE." indicating the clue hinted within the Cyberpunk forum.
The P and T in these images turned out to be Post and Thread IDs. Using these IDs in the url https://forums.cdprojektred.com/threads/11087221/post-13089542 leads to a post by CD Projekt Red employee, Vattier, which has hidden text in the post matching the color of the background:
SG93emUgNGJraCBveCA4dmlmcSwgZzYwIEkga2d6dyBiIHRkb3AgYnAgbHJ5aS4KCjAgY3JycWkgMG90ciB6bHN1IGF1aWwwd2UgLSAxdXkgMm9veiAybDBkaCBydGkgOykKCjVwdCB2Z2p3IHVvIHFncXdlcnJ2IDB6cCBJIHNubWFpZWcsIHJpeHUgYSBrb3JiIGpuIHd4ZTV0bWx5dzBwbiBhYThpNzIuYmI3cSB2c2ggbHM5b2Fway53Y3NuZHNpIHN0IGxybW01LgpKIGhsaiB4emYgM2Itam15anQgc29yIHVwZGggb3IgYnNhcXlxMHRzbHVyIG00N2JiZHIzIC0gaXcneSBsMGVkNnQgbTUgcWxkb3IgYWpna3ouCgpXNiBOaQ==
This string when decoded in Base64 returns the string:
Howze 4bkh ox 8vifq, g60 I kgzw b tdop bp lryi. 0 crrqi 0otr zlsu auil0we - 1uy 2ooz 2l0dh rti ;) 5pt vgjw uo qgqwerrv 0zp I snmaieg, rixu a korb jn wxe5tmlyw0pn aa8i72.bb7q vsh ls9oapk.wcsndsi st lrmm5. J hlj xzf 3b-jmyjt sor updh or bsaqyq0tslur m47bbdr3 - iw'y l0ed6t m5 qldor ajgkz. W6 Ni
This string can be further deciphered using a Vigenère cipher using the key BADGES found in the CARPE.rar file and an alphanumeric alphabet.
Gotta make it quick, coz I have a tail to lose. i broke into that archive - you know which one ;) not safe to namedrop who I phished, left a hint in transmission 744062.8538 use forname.surname as login. I hid the 38-digit pin code in transmission 43785992 - it's hidd3n in plain sight. So Mi
Which is a message from the netrunner Songbird giving clues to the NCPD Archive credentials present in two transmissions.
Transmissions
The transmissions mentioned in the previous clue indicate to various Twitter posts where the image contains a string of numbers in the graphic. There are two posts containing the numbers 744062.8538:
https://twitter.com/CyberpunkGame/status/1676585471827226630
https://twitter.com/CyberpunkGame/status/1536347637812629515
The second is the intended post giving the login username for the archives as saburo.arasaka who is the character featured on the post.
The post containing numbers 43785992 is a screenshot of an in-game conversation between Goro Takemura and V. There is is a string of numbers below Takemuras name on the left:
10.12.2021 2021.1212 1112.2121.10 10.12.2021 2021.1212 1112.2121.10 10.12.2021 10.12.2021 2021.1212
Using the hint of it's hidd3n in plain sight, the 3 combined with the numbers in the list being only 0,1,2 indicate the digits are encoded in ternary:
3 5 61 61 50 41 61 3 3 5 61 61 50 41 61 3 3 5 61 3 5 61 61 50
This is the 38 digit pin indicated by Songbird for the archives.
Netwatch Archives
The login credentials for the Netwatch Archive are:
Login: saburo.arasaka
Password: 35616150416133561615041613356135616150
The archives contain a series of images tagged as _VERIFIED, _NOT VERIFIED, and _CORRUPTED DATA. Inside four of the images contained a Night Corporation logo and some text.
| Image Name | Number |
|---|---|
| verified_30m.jpg | 23 |
| notverified_11f.jpg | 16 |
| notverified_13v.jpg | NHK NOON |
| notverified_16fq.jpg | 08 |
This indicated something will happen on August 16th, 2023, and it may be realted to Night Corp.
Case 00032 05 54 0B CP
On August 16th, it was found that returning to NIGHTCORP.NET now resulted in an active play button leading to the Night City Corsairs fan page which is a team sponsored by Nightcorp. Notable on this site are multiple buttons which end in a Netwatch content blocked screen. Navigating to the news tab there is a red PINNED under the first news item which contains a link to a message from Sandra D:
This is Sandra. Thank you for helping me with Night Corp. I dug out a lot of dirt on them. It’ll take a minute to load. Take it to the media, make people aware! CONNECTING...
Over time, the number of periods will increase and will eventually redirect to a google form with the following header:
Case 00032 05 54 0B CP By establishing this connection you have become a suspect in an official NetWatch investigation of the corporate espionage against Night Corporation in collaboration with Sandra Dorsett. Our agents are on their way to your location. The confidential files you expected to find here have been secured. Cooperate by filling the below statement and your sentence might be lowered or waived. DO NOT SHARE THE LINK TO THIS FORM ANYWHERE
At this stage, the investigation is still ongoing and awaiting a message from via email or similar.
| This page is a work in progress and will be updated as new developments emerge. If you have information you think should be added, please create an account to enable page edits or contact a Wiki Editor. |