Difference between revisions of "Mr Robot ARG"
| [checked revision] | [checked revision] |
(→The Breakfast Club) |
(→Email/Brian) |
||
| Line 363: | Line 363: | ||
On March 27, DHCP had updated to have new sections available, '''Advanced Routing''' and '''Port Address Translation'''. Inside of Port Address Translation, there were multiple messages encoded within the IP Addresses, and the MAC Addresses. | On March 27, DHCP had updated to have new sections available, '''Advanced Routing''' and '''Port Address Translation'''. Inside of Port Address Translation, there were multiple messages encoded within the IP Addresses, and the MAC Addresses. | ||
| − | + | On Advanced Routing, the first message was found when it was noticed that the last number was able to be translated into letters using a letter number cipher where A=1 and A=27. | |
{| class="wikitable" border="1" | {| class="wikitable" border="1" | ||
| Line 446: | Line 446: | ||
'''NOT ALL WHO WANDER SEE''' | '''NOT ALL WHO WANDER SEE''' | ||
| − | The second message was found | + | The second message was found when it was noticed that the last 3 octets of the MAC Address were all under 27, leading to doing another letter number: |
{| class="wikitable" border="1" | {| class="wikitable" border="1" | ||
| Line 529: | Line 529: | ||
'''RED HERRINGS ARE FUN DONT YOU THINK YOU SHOULD NOT HAVE COME HERE X''' | '''RED HERRINGS ARE FUN DONT YOU THINK YOU SHOULD NOT HAVE COME HERE X''' | ||
| − | The last message was found by | + | The last message was found by using the only information that was left, the first 3 octets of the MAC Address. The first 3 octets of a MAC Address are the [https://www.webopedia.com/TERM/O/OUI.html OUI], which is used to determine the manufacturer that created a device. By taking a list of the manufacturers, it was noticed that the first letter of each manufacturer spelled out a message: |
{| class="wikitable" border="1" | {| class="wikitable" border="1" | ||
| Line 612: | Line 612: | ||
'''EMAIL PW AMPHISBAENA''' | '''EMAIL PW AMPHISBAENA''' | ||
| − | + | Now that the password was found, a username had to be found. By inspecting the source code of the website, it was found that the login class was named <code>admin-login</code>, which pointed at '''admin''' being the username. | |
| − | + | Once logging in with the credentials '''admin'''/'''amphisbaena'''', the following message appeared: | |
<pre> | <pre> | ||
Revision as of 02:27, 6 April 2018
| Mr. Robot ARG | |
|---|---|
| An ARG set in the universe of Mr. Robot. | |
| Type | [[List_of_Investigations#Official|Official]] |
| Creator | NBC Universal |
| Discovered | 2017-09-28 |
Main Page > List of Investigations > Mr. Robot ARG
SPOILER WARNING: This wiki page may contain spoilers for the show Mr. Robot. The ARG is best played after catching up on the show. You have been warned!
The Mr. Robot ARG is an alternate reality game pertaining to the popular television show Mr. Robot. Throughout the course of the ARG, players interacted with characters and factions from the show, in order to solve puzzles. In particular, some players were recruited into fsociety, a fictional underground network of hackers. One of fsociety's main goals in the show is to disrupt a multinational corporation called E Corp.
| Pages | |
|---|---|
| Events | The events that have taken place during the ARG. |
| Episodes | The solves for the during the season ARG. |
The following recaps the ARG events that took place after the season finale.
Red Wheelbarrow
Red Wheelbarrow Activity Sheet
After the season finale aired the Red Wheelbarrow website updated again, with a new file in the Kid Wheelbarrow section. The file would change based on the user agent and if an extension named Looking Glass, a custom extension created for the Mr. Robot Season 3 ARG, was enabled. One file would be shown if Firefox was not being used, another would be shown if Firefox was used without the Looking Glass extension enabled, and another by using Firefox with the Looking Glass extension enabled. If you were to align posters of the three activity sheets, you would get this binary:
0000.0001:1111 0000.0100:0100 0000.0101:0110.0001.0101 0000.0110:1000 0000.1001:1100.0010 0000.1100:1110.1101.1001 0000.1110:0011 0000.1111:1010 0001.0010:0000.0111 0001.0100:1011
Converting the left column to decimal from binary, gives numbers, that have to be converted to letters using A1Z26 and the right column just to decimal gives you this translation:
1 (A) : 15 4 (D) : 4 5 (E) : 6, 1, 5 6 (F) : 8 9 (I) : 12, 2 12 (L) : 14, 13, 9 14 (N) : 3 15 (O) : 10 18 (R) : 0, 7 20 (T) : 11
If you use the numbers in the right column as the position of the letters, you get this:
R E I N D E I R F L O T I L L A 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
The string REINDEER FLOTILLA, is a reference to Tron. The rest of the image either has no meaning, or has yet to be solved.
Red Wheelbarrow Clock
On the DA_remote on WIMR, in the Documents folder epilogue.docx a hint for what to do is given.
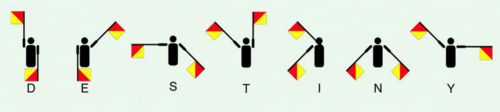
Jonathan consulting his trusty Semaphore manual (for doesn’t every sailor carry one?), realizing the whirling flags are spelling out a single word, over and over, like a drumbeat calling to him across the waves: “DESTINY”.
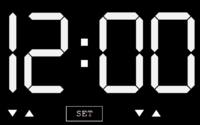
The only command that has been found to work in the terminal is destiny, leading to a clock on the Red Wheelbarrow website. Using the quote from the document as instructions, the word destiny can be converted into semaphore flags, a way of distance communication that uses flags in positions.
Converting the position of the flags to the hands of a clock, you get the following 7 times:
12:30 6:05 9:20 10:00 7:50 7:20 10:15
After inputting those times, the site will change and give you a message. After it is done, it will redirect you to the home page that now shows that you are signed in as admin of the Red Wheelbarrow site.
Red Wheelbarrow Network
Vincent
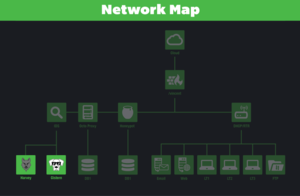
After being signed in as admin on the Red Wheelbarrow website, you will be able to click on the Network Map in the top left corner, redirecting you to this page. Going to that page requests a password, and inputting REINDEERFLOTILLA, previously found from the Red Wheelbarrow activity sheet, it will show the Red Wheelbarrow network map. Using the map, you can connect to the firewall by going to https://www.red-wheelbarrow.com/vincent/.
At the firewall (Vincent) site, the license has many references to the movie The Black Hole. The main references are MarcusT, Marcus Tullius Cicero, and reference to a Cicero misquote being referenced in The Black Hole. "V.I.N.CENT: To quote Cicero: rashness is the characteristic of youth, prudence that of mellowed age, and discretion the better part of valor." Turning that quote into only lowercase letters, you get rashnessisthecharacteristicofyouthprudencethatofmellowedageanddiscretionthebetterpartofvalor. Using that as the password, and Cicero as the username you get access to the 4 other sites referenced on the Network Map.
The firewall site updated on January 26th to have an option to update, giving this message:
Current Base System 03673.12.18 Latest Base System 03701.8.2 Warning: to maintain Dutchman system compatibility administrative level 33 rotational access is required and system time must sync. Proceed with update?
The first system version is a reference to The Black Hole, with 03673 being octal for 1979, and 12.18 being the date for it's release. The same logic was used on the second version, being a reference to the movie Fright Night (Releasing on the date August 2nd, 1985). There currently has been no use for the Fright Night reference.
ProboscisMonkey/theWolf
Proboscis Monkey (theWolf) is the IDS, Intrusion Detection System, for the Red Wheelbarrow network. The site unlocked on January 26th along with the Firewall update. The firewall message, Warning: to maintain Dutchman system compatibility administrative level 33 rotational access is required and system time must sync. gave a hint on what to do.
Dutchman sytem -> Proboscis Monkey Administrative -> admin username Level 33 -> Red Wheelbarrow commercial Rotational Access -> Hint at password
An additional hint was given by Crypt from Curious Codes, "As the days go by, I leave this thing [bowl on a lathe] rotating over and over". This lead people to investigate and found out if you were to use PLASTICFORKS (previously found from the Red Wheelbarrow commercial) and ROT it by the day of the month, you would get the password. For example, if the day was June 15th, using ROT15 the password would be EAPHIXRUDGZ.
NOTE: To find the current password, you can use this site.
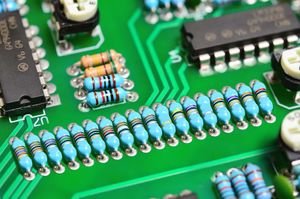
Harvey
Using the network map found inside of Proboscis monkey, Harvey was found with the message 500 Internal Server Error Harvey is CURRENTly down. Sorry for the trouble. with a picture of resistors. The word CURRENT is a hint to get the current of the resistors. If you were to use this chart on all but the tolerance and multiplier bands (last 2 bands) you would get a message:
0 - Black 1 - Brown 2 - Red 3 - Orange 4 - Yellow 5 - Green 6 - Blue 7 - Violet 8 - Gray 9 - White
BROWN BROWN VIOLET - 117 BROWN BROWN BLACK - 110 GRAY VIOLET - 87 VIOLET GREEN - 75 GRAY RED - 83 GRAY BLACK - 80 BROWN BROWN RED - 113 BROWN BROWN WHITE - 119 BROWN BROWN - 11 BROWN GRAY - 18 NONE - 0 YELLOW - 4 VIOLET - 7 NONE - 0 ORANGE - 3 VIOLET - 7 ORANGE - 3 RED - 2
You get the string 117 110 87 75 83 80 113 119 11 18 0 4 7 0 3 7 3 2 Translated the first part using ASCII decimal codes you get unWKRPpw 11 18 0 4 7 0 3 7 3 2. The last number is a reference to Van Eck's sequence, which occurred during Kor Adana's interview with the Hollywood Reporter. Using those numbers as a clue to find a password from those interviews, it was found that hackjamtor was the password for Octo Proxy.
Cistern
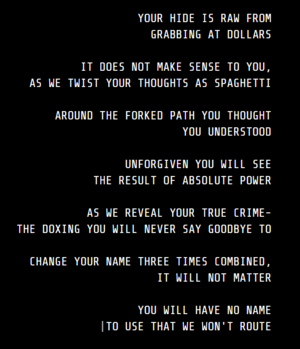
Using the network map Cistern was found with the message Down for Maintenance for Approximately 24 Hours and an image. It was found that if you were to keep the site open for 24 hours (or manipulate the site cookie) the screen would become black and show the following message:
YOUR HIDE IS RAW FROM GRABBING AT DOLLARS IT DOES NOT MAKE SENSE TO YOU, AS WE TWIST YOUR THOUGHTS AS SPAGHETTI AROUND THE FORKED PATH YOU THOUGHT YOU UNDERSTOOD UNFORGIVEN YOU WILL SEE THE RESULT OF ABSOLUTE POWER AS WE REVEAL YOUR TRUE CRIME- THE DOXING YOU WILL NEVER SAY GOODBYE TO CHANGE YOUR NAME THREE TIMES COMBINED, IT WILL NOT MATTER YOU WILL HAVE NO NAME TO USE THAT WE WON'T ROUTE
The message is laden with references to Clint Eastwood movies. "Rawhide", "a Fistful of Dollars", "Spaghetti Western", "Unforgiven", "Absolute Power", "True Crime", "Never Say Goodbye", (The Good, The Bad, and The Ugly [changing names 3 times]), and "The Man With No Name."
Octo Proxy/theRunningMan
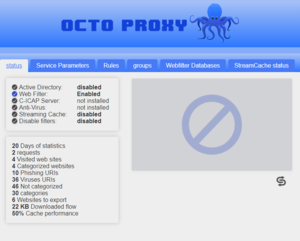
Octo Proxy (theRunningMan) is the proxy on the Red Wheelbarrow network. The username and password WKRP/hackjamtor was found in the Proboscis Monkey Harvey image. Inside of Octo Proxy is a control panel with the only options being available are status and Webfilter Databases. In the status tab of Octo Proxy it had the following statistics:
20 Days of statistics 2 requests 4 Visited web sites 4 Categorized websites 10 Phishing URIs 36 Viruses URIs 46 Not categorized 30 categories 6 Websites to export 22 KB Downloaded flow 50% Cache performance
The solution to the puzzle was found by removing all the text, going from the top to the bottom, and using the 50% on all numbers. After doing that, translating using A1Z26 you got the following:
10 - J 1 - A 2 - B 2 - B 5 - E 18 - R 23 - W 15 - O 3 - C 11 - K 25 - Y
On the Webfilter Databases tab, there is the login to DB1, and text at the bottom:
Brace yourselves- Let the idea sink in...it's on the tip of your tongue you know. Core truths, when heard will ring out, calling you out of ignorance.
The password for DB1 was found by finding the origin of Jabberwocky, which is Through the Looking-Glass, a source commonly referenced throughout the ARG. Using a synonym for looking glass, it was found that mirror was the password to access DB1.
DB1
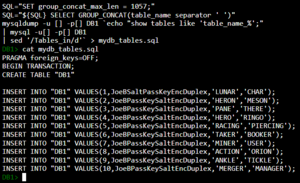
Once signing into the DB1 console, you are given a terminal that is running MySQL, and has a limited amount of commands. It was then discovered that cat mydb_tables.sql was a working command that gave you the contents of the file shown to be generated above:
PRAGMA foreign_keys=OFF; BEGIN TRANSACTION; CREATE TABLE "DB1" INSERT INTO "DB1" VALUES(1,JoeBSaltPassKeyEncDuplex,'LUNAR','CHAR'); INSERT INTO "DB1" VALUES(2,JoeBPassKeySaltEncDuplex,'HERON','MESON'); INSERT INTO "DB1" VALUES(3,JoeBPassKeySaltEncDuplex,'PANE','THERE'); INSERT INTO "DB1" VALUES(4,JoeBPassKeySaltEncDuplex,'HERO','RINGO'); INSERT INTO "DB1" VALUES(5,JoeBPassKeySaltEncDuplex,'RACING','PIERCING'); INSERT INTO "DB1" VALUES(6,JoeBPassKeySaltEncDuplex,'TAKER','BOOKER'); INSERT INTO "DB1" VALUES(7,JoeBPassKeySaltEncDuplex,'MINER','USER'); INSERT INTO "DB1" VALUES(8,JoeBPassKeySaltEncDuplex,'ACTION','ORION'); INSERT INTO "DB1" VALUES(9,JoeBPassKeySaltEncDuplex,'ANKLE','TICKLE'); INSERT INTO "DB1" VALUES(10,JoeBPassKeySaltEncDuplex,'MERGER','MANAGER');
The output seems to be creating a database with a list of words. JoeB is a reference to Meet Joe Black, a movie that Brad Pitt is in, likely referring to the Honeypot. For each set of words, if you were to remove the common ending, then combined what is left, you would get another word.
LUNAR - CHAR | AR | LUNCH HERON - MESON | ON | HERMES PANE - THERE | E | PANTHER HERO - RINGO | O | HERRING RACING - PIERCING | CING | RAPIER TAKER - BOOKER | KER | TABOO MINER - USER | ER | MINUS ACTION - ORION | ION | ACTOR ANKLE - TICKLE | KLE | ANTIC MERGER - MANAGER | GER | MERMANA
Honeypot/bradPitt
The login for the Honeypot was found by using the first of the list of ten words pairs found in Octo Proxy, excluding the last pair, as the username and then using the word found by removing the common ending as the password. The following is a list of the working usernames and passwords.
LUNAR/LUNCH HERON/HERMES PANE/PANTHER HERO/HERRING RACING/RAPIER TAKER/TABOO MINER/MINUS ACTION/ACTOR ANKLE/ANTIC
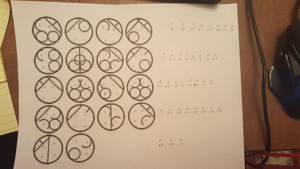
After logging in, a picture of glyphs appear:
By using process of elimination, it was found that there were 10 different glyphs, representing 1-10. Then it was determined that the glyphs read, bottom right, top left, bottom left, top right. Using that method of reading the glyphs, the message PREACHER PASSWORD HELLFOLLOWEDWITHHIM a quote from Revelation 6:8.
DB1
Inside of Honeypot there is a link that leads to the database. Once you go to that site, it shows the following numbers:
0152052216.9000302595 1599901684.0679734511
The numbers were the ISBN for 4 books:
East.Password Dangerous.Demons
DHCP/preacher
The login for DHCP was found by using the solution from Honeypot, and the text from Cistern in Proboscis Monkey, hinting at Man with No Name. Using the 3 nicknames and combining them, you get the username joemoncoblondie and the password hellfollowedwithhim.
The Breakfast Club
Email/Brian
On March 27, DHCP had updated to have new sections available, Advanced Routing and Port Address Translation. Inside of Port Address Translation, there were multiple messages encoded within the IP Addresses, and the MAC Addresses.
On Advanced Routing, the first message was found when it was noticed that the last number was able to be translated into letters using a letter number cipher where A=1 and A=27.
| IP Adress | Last Digit | Letter Number |
|---|---|---|
| 10.10.10.14 | 14 | N |
| 10.10.10.15 | 15 | O |
| 10.10.10.20 | 20 | T |
| 10.10.10.27 | 27 | A |
| 10.10.10.38 | 38 | L |
| 10.10.10.64 | 64 | L |
| 10.10.10.75 | 75 | W |
| 10.10.10.96 | 96 | R |
| 10.10.10.119 | 119 | O |
| 10.10.10.127 | 127 | W |
| 10.10.10.131 | 131 | A |
| 10.10.10.144 | 144 | N |
| 10.10.10.160 | 160 | D |
| 10.10.10.161 | 161 | E |
| 10.10.10.174 | 174 | R |
| 10.10.10.175 | 175 | S |
| 10.10.10.187 | 187 | E |
| 10.10.10.213 | 213 | E |
NOT ALL WHO WANDER SEE
The second message was found when it was noticed that the last 3 octets of the MAC Address were all under 27, leading to doing another letter number:
| MAC Adress | MAC Address (Last 3 Octets) | Letter Number |
|---|---|---|
| 00:23:A6:18:05:04 | 18:05:04 | RED |
| B8:D4:9D:08:05:18 | 08:05:18 | HER |
| 00:1A:9F:18:09:14 | 18:09:14 | RIN |
| 00:0B:1F:07:19:01 | 07:19:01 | GSA |
| 00:10:27:18:05:06 | 18:05:06 | REF |
| 00:02:2F:21:14:04 | 21:14:04 | UND |
| 00:06:AB:15:14:20 | 15:14:20 | ONT |
| 00:1A:9F:25:15:21 | 25:15:21 | YOU |
| B8:D4:9D:20:08:09 | 20:08:09 | THI |
| 00:02:2F:14:11:25 | 14:11:25 | NKY |
| E8:C2:29:15:21:19 | 15:21:19 | OUS |
| 00:0B:1F:08:15:21 | 08:15:21 | HOU |
| 30:F7:7F:12:04:14 | 12:04:14 | LDN |
| 48:02:2A:15:20:08 | 15:20:08 | OTH |
| 00:1A:9F:01:22:05 | 01:22:05 | AVE |
| 00:23:A6:03:15:13 | 03:15:13 | COM |
| FC:83:C6:05:08:05 | 05:08:05 | EHE |
| 00:15:66:18:05:24 | 18:05:24 | REX |
RED HERRINGS ARE FUN DONT YOU THINK YOU SHOULD NOT HAVE COME HERE X
The last message was found by using the only information that was left, the first 3 octets of the MAC Address. The first 3 octets of a MAC Address are the OUI, which is used to determine the manufacturer that created a device. By taking a list of the manufacturers, it was noticed that the first letter of each manufacturer spelled out a message:
| OUI | Manufacturer | Letter |
|---|---|---|
| 00:23:A6 | E-Mon | E |
| B8:D4:9D | MSevenSy M Seven System Ltd. | M |
| 00:1A:9F | A-Link A-Link Ltd | A |
| 00:0B:1F | IConComp I CON Computer Co. | I |
| 00:10:27 | L-3Commu L-3 COMMUNICATIONS EAST | L |
| 00:02:2F | P-Cube P-Cube, Ltd. | P |
| 00:06:AB | W-Link W-Link Systems, Inc. | W |
| 00:1A:9F | A-Link A-Link Ltd | A |
| B8:D4:9D | MSevenSy M Seven System Ltd. | M |
| 00:02:2F | P-Cube P-Cube, Ltd. | P |
| E8:C2:29 | H-Displa H-Displays (MSC) Bhd | H |
| 00:0B:1F | IConComp I CON Computer Co. | I |
| 30:F7:7F | SMobileD S Mobile Devices Limited | S |
| 48:02:2A | B-LinkEl B-Link Electronic Limited | B |
| 00:1A:9F | A-Link A-Link Ltd | A |
| 00:23:A6 | E-Mon | E |
| FC:83:C6 | N-RadioT N-Radio Technologies Co., Ltd. | N |
| 00:15:66 | A-FirstT A-First Technology Co., Ltd. | A |
EMAIL PW AMPHISBAENA
Now that the password was found, a username had to be found. By inspecting the source code of the website, it was found that the login class was named admin-login, which pointed at admin being the username.
Once logging in with the credentials admin/amphisbaena', the following message appeared:
WEST PASSWORD: DEADLY DISPUTE FTP richard
FTP/Richard
The previous message from email had mentioned Richard, /vincent/preacher/richard, which is the next website. The username and password were found by using the default guest login into an FTP server, anonymous/anonymous. Once logged in, it references the web login Andrew. Additionally, you can run the commands dir and get chat.log.txt to get the following text:
remote: Chat.Log.txt 228 Extended Passive Mode Entered (|||36565|) 150 Opening ASCII mode data connection for ChatLog.txt (438 bytes) For Apache access: GET 62+18 EACH 53-8 PART 59+26 AT 39+34 CHAT 46+2 AND 62+10 MACE 41+20 HUNT 59+26 KURT 39+34 226 Transfer Complete 438 bytes received in 00:00 (110.57 KiB/s)
The first word, GET, is also the first word on Andrew. It was found that if you were to translate the 2 numbers into coordinates, get the location, and translate the word into that language, you get an animal. This is another hint that it is connected to Andrew and Orwell, shown in the title of the site, because of one of Orwell's books named Animal House.
| Word | Number 1 | Number 2 | Coordinates | Location | Region Translate |
|---|---|---|---|---|---|
| GET | 62 | 18 | 62.00000 18.00000 | Sweden | Goat |
| EACH | 53 | -8 | 53.00000 -8.00000 | Ireland | Horse |
| PART | 59 | 26 | 59.00000 26.00000 | Estonia | Duck |
| AT | 39 | 34 | 39.00000 34.00000 | Turkey | Horse |
| CHAT | 46 | 2 | 46.00000 2.00000 | France | Cat |
| AND | 62 | 10 | 62.00000 10.00000 | Norway | Duck |
| MACE | 41 | 20 | 41.00000 20.00000 | Albania | Cat |
| HUNT | 59 | 26 | 59.00000 26.00000 | Estonia | Wolf |
| KURT | 39 | 34 | 39.00000 34.00000 | Turkey | Wolf |