Difference between revisions of "Tender"
| [checked revision] | [checked revision] |
(Upgrading to official) |
(First pass of Grif Observatory puzzle) |
||
| Line 351: | Line 351: | ||
Knox contacted BetrayedMind1 once more to verify the location and [https://twitter.com/KnoxJ2019/status/1091452514258558976 confirmed] shortly afterwards that this is the correct site. | Knox contacted BetrayedMind1 once more to verify the location and [https://twitter.com/KnoxJ2019/status/1091452514258558976 confirmed] shortly afterwards that this is the correct site. | ||
| + | |||
| + | ===Griffith Observatory=== | ||
| + | |||
| + | At 1900 UTC on 02-02-2019, 2 players met the contact at Griffith Observatory and received a locked briefcase with a 6 digit code. They were also told "Trust No More" before the contact left the observatory. | ||
| + | |||
| + | At the same time, Trust No More updated with a [https://www.trustnomore.com/2019/02/02/trust-no-more/ page] containing 6 lines of numbers. | ||
| + | |||
| + | <pre>-07.16/-78.53/+1533/2of4 | ||
| + | +30.80/+31.83/-1213/1of4 | ||
| + | +36.36/+43.15/-627/3of4 | ||
| + | +41.90/+12.49/+54/4of4 | ||
| + | +47.08/+08.43/+1935/4of4 | ||
| + | +50.19/+14.66/+935/1of4</pre> | ||
| + | |||
| + | Players worked to decipher the numbers however were unable to work out the solution until 2 additional hints were provided. The first linked to a [https://en.wikipedia.org/wiki/List_of_minor_planets_named_after_people list of minor planets named after people] and the second linked the first co-ordinates to [https://www.google.com/maps/place/Cajamarca,+Peru/@-7.1606346,-78.5392219,13z/data=!3m1!4b1!4m5!3m4!1s0x91b25afd3fc7d087:0xea80a2b94d876b2b!8m2!3d-7.1617465!4d-78.5127855 Cajamarca, Peru]. | ||
| + | |||
| + | Players quickly worked out that each of the 6 sets of numbers corresponded to a location (latitude, longtitude) and then the third number referred to a year of death for someone significant there - specifically someone who now has a planet named after them. This resulted in the following 6 planets: | ||
| + | |||
| + | <pre>4721 Atahualpa | ||
| + | 4416 Ramses | ||
| + | 7208 Ashurbanipal | ||
| + | 7117 Claudius | ||
| + | 1128 Astrid | ||
| + | 8740 Vaclav</pre> | ||
| + | |||
| + | After attempting to enter a code based on the digit in each number (1 of 4 in 4721 would be 4), one final hint was provided in the form of a [https://www.youtube.com/watch?v=hMaVIAlJlnw youtube video]. With the title "The Order of Death", players deduced that the order of planets would need to be rearranged in chronological order of death. The new list (and corresponding digit) was: | ||
| + | |||
| + | <pre>4416 Ramses - 4 | ||
| + | 7208 Ashurbanipal - 0 | ||
| + | 7117 Claudius - 7 | ||
| + | 8740 Vaclav - 8 | ||
| + | 4721 Atahualpa - 7 | ||
| + | 1128 Astrid - 8</pre> | ||
| + | |||
| + | The code '''407878''' was entered and the briefcase was successfully unlocked. Inside multiple items were found including a pen, a redacted document from Tender, a page with unusual symbols, a handwritten page about scientific tests on animals, a book on blood types, a recipe for a pancake, sunglasses, a tag that says "trustnomore.com/xxxxxxx" and a notebook that contains the phrase "PUVZREN". | ||
| + | |||
| + | When appending PUVZREN to the trust-no-more.com URL, a [https://www.trustnomore.com/puvzren/ password protected page] was found. | ||
| + | |||
| + | The unusual code was identified as [https://en.wikipedia.org/wiki/Moon_type Moon type], with the text reading '''whistleblower'''. When entered into the password box on the Trust No More page already, found a new [https://s3.amazonaws.com/trustnomore/wp-content/uploads/2019/02/02114627/0750d042-2a97-4c5b-ae5c-87d868603da9.jpg leaked image] was discovered. | ||
{{WIP}} | {{WIP}} | ||
Revision as of 21:19, 2 February 2019
| Trust No More | |
|---|---|
| Type | Official |
| Creator | ??? |
| Discovered | 2019-01-19 |
Main Page > List of Investigations > Tender
KnoxJ2019
On 2019-01-19, a Twitter account with the handle @KnoxJ2019 (full name John Knox) began posting a series of small puzzles. Around the same time, a number of prominent YouTubers began linking KnoxJ2019's account to their followers.
Twitter Puzzle 1
The first set of clues from KnoxJ2019's account included a picture of constellations and a Pastebin link. The constellations were identified as Cassiopeia, Ursa Major, Ursa Minor, Taurus and Scorpius. The position of each red star within each constellation (as well as the total number of stars) was noted. For instance, Cassiopeia has 5 stars and the 2nd star in Cassiopeia is highlighted. Each of these pairs were then used for a book cipher with the Pastebin, with the total number of stars determining the word and the highlighted star number determining the letter. Using this method resulted in the first word of the cipher: TRUST.
Twitter Puzzle 2
The second set of tweets involved a string of numbers and an alphabetical equation. The string of numbers was solved by working out that every odd-numbered position (1st, 3rd, 5th number) increases by 2 each time, and likewise every even numbered position increases by 3. This resulted in the number 14, which was converted to 'N', the 14th letter in the alphabet.
The alphabetical equation tweet read as follows:
G + A + G = ?
By converting each letter into a number based on its position, then converting back, the following equation was revealed:
7 + 1 + 7 = ?
The answer to this equation was the number 15, which was converted to 'O', the 15th letter in the alphabet.
Putting the two letters together yielded the word NO.
Twitter Puzzle 3
The third set of tweets involved a spam message, an image containing a hex colour code, a backwards tweet and cryptic message.
Players first found a clue to the spam message by searching Knox's liked tweets, which included one where Keralis hinted at some form of cipher which is designed to look like spam. The spam message cipher was identified as Spammimic. The message was entered into the decoder to discover the text "12 - x - 14". This was interpreted as a sequence where x is 13, which was swiftly converted to 'M', the 13th letter of the alphabet.
By this point, players had deduced that the message read as follows:
TRUST NO M____
Eventually, players were able to guess that the completed phrase was TRUST NO MORE.
Trust No More & Tender Beta
After the TRUST NO MORE phrase was revealed, KnoxJ2019 posted a link to a website called trustnomore.com. This same tweet contained another link to tenderbeta.com, which appeared to be advertising a new dating app.
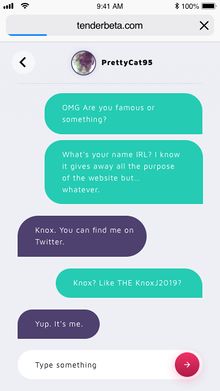
After searching the Trust No More website, Knox was messaged via Twitter regarding an article about zombies, humans, and potential links to Tender. Knox replied with information about BetrayedMind1, who told him about the dangers and experiments that Tender is involved with (as also seen on Trust No More). Also included was a picture showing the chat system and part of the UI within Tender (including the latest message from BetrayedMind1).
Players followed a link within the aforementioned article to the Tender Beta site where a registration page was found. Signing up for the beta with an email address resulted in a queue position number being assigned to the player.
A second article on Trust No More was posted by Manchuria which detailed that a cache of data had been uncovered under the label "Project Chimera". Also noted was that each of the files uncovered appeared to be related to the CEO of Tender - Malcolm Chandler. Finally, the author of the article uncovered an image, but this image has no significance as of yet.
Shortly thereafter, Knox tweeted the following message:
Something is coming up on Saturday and I’ll need your help. The only problem is that I’m only going to be available during my flight [ UA 264 ] from SF to Houston. I’m counting on you guys!
Messages from Tender
Players noticed that several YouTubers and Twitch streamers started to have a random alphanumeric code appear in their video accompanied by a pink smoke. This was first noticed on a video from Keralis - a popular YouTuber who Knox has communicated with via tweets in the past. Soon other creators were found to have a similar message. Below is a list of all known messages that have been sent out so far.
Keralis - Cities Skyline Video
On 2019-01-09, Keralis posted his first episode of a new Cities Skyline series. At 02:01 the code 3ej26jqf can be seen to appear on screen unexpectedly. Keralis appeared to be unaware of this and made no comment in the video or in the description. This code let to a pastebin with the following message:
phase 1 initiated
GassyMexican - Red Dead Redemption 2 Stream
On 2019-01-19, GassyMexican streamed gameplay of Red Dead Redemption 2. At 01:52:51 of the saved livestream the code 2Hawuq0 could be seen. This was a bit.ly link that led to the following pastebin message:
Here’s an exclusive look at our chat feature coming directly from one of our dearest user, PrettyCat95. https://bit.ly/2SPFEd0
This new bit.ly link led to an imgur image showing chat messages between PrettyCat95 and Knox.
Keralis - Minecraft Video
On 2019-01-19, Keralis posted a Minecraft video which included a short discussion about the events so far regarding Knox and Trust No More. At 0:53 in the video the code 5PCgKkRH can be seen. This code led to a pastebin with the following message:
Welcome future Tender users, We have been in contact with some of your favorite influencers who will soon make a very important announcement. Stay alert, your help will be required in launching our amazing new website, Tender. Much Love, Your friends at Tender
Right after the code appeared, Keralis mentions the ongoing puzzles, how Knox is his friend and that he has read some of the articles on Trust No More
Keralis - Soviet Republic Video
On 2019-01-26, Keralis posted another video, this time about the game Workers & Resources: Soviet Republic. At 1:39 the code ZRK0sWZe can be seen. This led to the following pastebin message:
I never go left and I am never wrong, ever Start the sequence by one and add this number Until you have a thumb, an index, a middle, a ring and a little finger Go back to one when you reach the latter. For each period and mark that you encounter, Restart the sequence with the first number This will affect all the characters Mix lettuce, croutons, lemon juice, olive oil, egg, Worcestershire Anchovies, garlic, Dijon mustard, Parmesan cheese, and black pepper. It will give you a salad that hold the key to this cipher. /// Tq kiwf ary fsg. Igui bf cop fsg. Cww ambv lw mfth? Xgop xjv gsbo cqh bf’no jnmn bsz jp rr biq zi fsg dri xjb aj bth htjpj xmju. Mgw’w ybmh e xugs ffdm lr yjoh xt uyr xmpwvese hrywughr. Qkfxzsg d wrbno, xbp dhhwpqp eubtwqjov fsswguxje husr b vkvjf uweqm idvfhg lr Sfy Bswl. Pwu jtvpgiwt ohx zq cv e lsqxt tg rhsumg zlt icg isdqxryfthh jwguc kbnvi xucux, gsqnis igdvy, bpg wyfthsyzrlgfm rlxkbno sk ppomsf odxhiodonoi. Ujuszhj pyhi edjkfkqi fof gvd-ftdwj cqdvi teumgcnlrl, ujhc gfidr yig fssdgsxx ujdx bpwoh ybmh wtdkdp rffle fof lryftqiy ecwmsh cqh rbmh my ujhmw pyq. Ncnmsh kw szsu: Zljsg gmi xg jiy pwu mifc isw pwu eqhqumyiov? Telisdg rj hpwuwj! Pxhv f gqxv dfcu xwjco tjskrh, ztkqk Usqfiivtdp Jnqwmto Ihrjscwmto xle Rbekmsf Nhewokqk (ts RHKRM), c omyunh ewu, cqh f ecvl tg gptfujb, aj egyiqprhh bicw aj iqsi bjno fj UJH vjwqoyyjqq ms ppomsf odxhiodonoi. B vhgmoqoslz cqh f ugflsjsxi yicw eqmqzw FMN ws kjpg e hppqihukrr (mpyhzjs vkid egimsf vkey) ujdx nt tlkmu hrv yigp. Oq peyugu ctvt eehliuszof, wljsg lw xpohssf qxx yigui biq vtfsmv ctvt lrsft fljnkvxwz. Yh ltqg ws rbmh xmbv fssogfxnpp keuqgq jts ARY. Bu d xwvg wvjofviyugu ese gdvqz cgsuugu, aj icyi fo kqgwfflfqf lrywogb emfcg. Gtrq fmn rj zt jhvj bv Wisegu: Xmbpn ctv hrv opkqmsh. Ujh Xjbo
The first half (non-ciphered) was quickly identified as relating to a Caesar cipher, but with a constantly changing ROT value. By using a vigenere key of bcdef, and resetting at every punctuation mark or new line, players quickly deciphered the second half to:
So here you are. Here we all are. But what is here? Well sit down and we’ll fill you in on who we are and why we are doing this. Let’s take a step back in time to two thousand fourteen. Picture a small, two bedroom apartment converted from a three stall garage in New York. Our founders met up as a group of people who had encountered every false start, broken heart, and stereotypical pitfall of online matchmaking. Through much caffeine and dry-erase board scribbling, they began the concepts that would take social media and internet dating and make it their own. Making it ours: Where did we get our idea for our algorithms? Science of course! Over a four year trial period, using Procedural Emotion Generation via Machine Learning (or PEGML), a little art, and a dash of empathy, we developed what we hope will be THE revolution in online matchmaking. A technology and a technique that allows ALL to find a connection (however they define that) that is right for them. No matter your background, there is someone out there who sparks your inner chemistry. We hope to make that connection happen for YOU. As a true trendsetter and early adopter, we have an incredible journey ahead. From all of us here at Tender: Thank you for joining. The Team
Knox's Flight
On Saturday, January 26, Knox made the following tweet:
The bit.ly link led to the following string:
<~7<W6_H$!_6DJ()+F!+t2DJj#qFCeu8+B3#c+DkP$DBNG-DJj#qFD5Z2+DGm>FD,5.@;^.1ATBC~>
When decoded using BASE85, the message instead reads:
Everything is connected. The main connection is the answer.
This was emailed to the provided contact address, however this was not the correct response with the contact replying:
If you're reading this, well...nice try but that's not it. She needs people who can deal with things, heavier things than these puzzles. C'mon, next time you contact me, you better have the right answer. < 1969-41-1 >
Searching the TNM site for 1969-41-1 resulted in an error page with 3 sets of articles, times and answer string formats.
Article 1 - FBI leaks federal secrets
The first article was timed for 16:37 UTC, at which time the linked article updated to include a crossed-out line at the bottom:
Fear and Dread are my “children”. I am close to you but how close am I from the “Sol”
Fear and Dread were identified as referencing Phobos and Deimos - the children of Aphrodite and Ares. Sol was identified as the Latin name for the Sun in our solar system. Finally, Ares is the Greek god equivalent of roman god Mars. Since Mars is the 4th planet from the Sun, the answer was determined to be 4.
Article 2 - The Murder Carpet
The second article was time for 19:14 UTC. When the time elapsed the following string was added to the bottom of the relevant article.
I am composed of 5.9% red, 32.2% green and 72.9% blue You can find me between the 5th and 6th knuckle.
The colour was quickly identified as Sapphire. The 5th and 6th knuckle referred to the 1st and 2nd knuckle of the right hand (5th and 6th when both hands are together). This translates to September when using knuckles to count months. As confirmation, Sapphire is also the birth stone of September.
Article 3 - Blood Moon: A Heavenly Body Abused
The final article was scheduled for 21:22 UTC but was released early due to the progress of players. This new article did not contain a line at the bottom but instead an image which, when clicked on to enlarge, revealed a transparent layer with 4 symbols hidden in the image previously. These symbols were found to be numbers that were cut off half way through - 1, 7, 8 and 1.
Response from the Messenger
With this, players had a full date - 4 September 1781. This was the same date that Los Angeles was founded. A second email was sent to the provided address stating that Los Angeles was the answer (as well as the solution method), with the following response received:
Los Angeles? Yes, that's it. That's what she told me. Here, you might have more info on what she's going on about: 0, 1, 1, 2, 3, 5, 8, 13, 21, 55, 89, 144, 213, 233, 266, 377, 610, 987, 1597, 2584, 4181, 6785, 7737, 10946, 17711, 28657, 46368, 75025, 121393, 196418, 317811
This was quickly identified as very similar to a Fibonacci sequence, but with additional numbers inserted - namely 213, 266 and 7737. This corresponded to a US phone number in the LA area (213-266-7737). Players who called this number heard an automated message with a modulated voice reading the following message:
Hello there, Knox I see you've made your way through the puzzles. Well done. You have proven trustworthy enough to meet in person next weekend. We have some business to discuss at that time. You better be serious about this
After updating Knox on this message, it was made clear in a tweet that he would not be available on the weekend and as such someone would need to go to Los Angeles and meet the user who has been communicating with him.
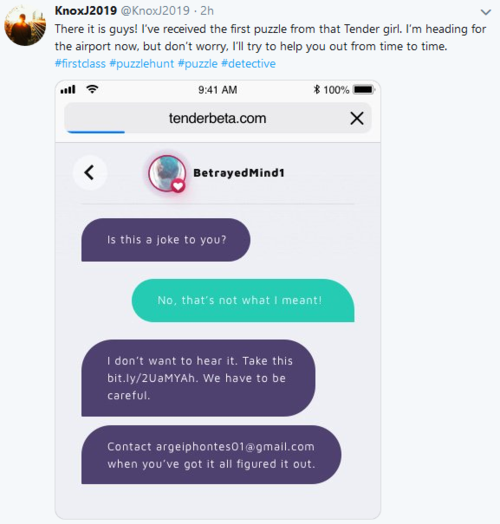
Meeting BetrayedMind1
On 2019-01-31, Knox tweeted that he had contacted BetrayedMind1 about the planned meeting in order to get more information on where it is taking place. The user refused to give this information, instead saying that "it's something you're already aware of".
The following day, after receiving no firm idea on where the meeting is to be held, Knox ran through the list of everything known so far in a tweet. Of note was that the phone number was written down in whole, rather than just referred to. When players called this number again, they found that rather than an automated message, background noise could be head from someone driving.
Finding the location
The first message users found was at 16:33 UTC on 2019-02-01. It contained background audio from a radio station, a turn signal and then the following Sat Nav message:
Continue straight onto Hollywood Boulevard
At 17:13 UTC another player called the same number and found a different message, featuring the same background radio stations, the below Sat Nav message followed by another turn signal:
Turn right onto Berendo Street
At 18:31 UTC, a third message was found, with the same background audio as the two previous messages and a new Sat Nav line:
Turn left onto Franklin Avenue
At 20:01 UTC the fourth message was found, with the following Sat Nav direction:
Turn right onto Western Avenue
This new direction was sent to Knox, who in turn tweeted that he would contact BetrayedMind1 for more details. This resulted in nothing more as Knox followed up to say that everything had been provided to us. The only new information was the she had been repeatedly using the Dizzy Symbol emoji (💫).
Players noted that around the area where the directions stopped, a trail started which led to the Griffith Observatory. This was determined to be likely both due to the emoji containing a star and that earlier in the ARG, the planet Mars was referred to.
Knox contacted BetrayedMind1 once more to verify the location and confirmed shortly afterwards that this is the correct site.
Griffith Observatory
At 1900 UTC on 02-02-2019, 2 players met the contact at Griffith Observatory and received a locked briefcase with a 6 digit code. They were also told "Trust No More" before the contact left the observatory.
At the same time, Trust No More updated with a page containing 6 lines of numbers.
-07.16/-78.53/+1533/2of4 +30.80/+31.83/-1213/1of4 +36.36/+43.15/-627/3of4 +41.90/+12.49/+54/4of4 +47.08/+08.43/+1935/4of4 +50.19/+14.66/+935/1of4
Players worked to decipher the numbers however were unable to work out the solution until 2 additional hints were provided. The first linked to a list of minor planets named after people and the second linked the first co-ordinates to Cajamarca, Peru.
Players quickly worked out that each of the 6 sets of numbers corresponded to a location (latitude, longtitude) and then the third number referred to a year of death for someone significant there - specifically someone who now has a planet named after them. This resulted in the following 6 planets:
4721 Atahualpa 4416 Ramses 7208 Ashurbanipal 7117 Claudius 1128 Astrid 8740 Vaclav
After attempting to enter a code based on the digit in each number (1 of 4 in 4721 would be 4), one final hint was provided in the form of a youtube video. With the title "The Order of Death", players deduced that the order of planets would need to be rearranged in chronological order of death. The new list (and corresponding digit) was:
4416 Ramses - 4 7208 Ashurbanipal - 0 7117 Claudius - 7 8740 Vaclav - 8 4721 Atahualpa - 7 1128 Astrid - 8
The code 407878 was entered and the briefcase was successfully unlocked. Inside multiple items were found including a pen, a redacted document from Tender, a page with unusual symbols, a handwritten page about scientific tests on animals, a book on blood types, a recipe for a pancake, sunglasses, a tag that says "trustnomore.com/xxxxxxx" and a notebook that contains the phrase "PUVZREN".
When appending PUVZREN to the trust-no-more.com URL, a password protected page was found.
The unusual code was identified as Moon type, with the text reading whistleblower. When entered into the password box on the Trust No More page already, found a new leaked image was discovered.
| This page is a work in progress and will be updated as new developments emerge. If you have information you think should be added, please create an account to enable page edits or contact a Wiki Editor. |