Difference between revisions of "Bradwell Electronics"
| [unchecked revision] | [unchecked revision] |
m (Changed to be current.) |
(Found actual method of solving the puzzles.) |
||
| Line 127: | Line 127: | ||
== 2nd Key == | == 2nd Key == | ||
| − | + | When the text of the public memo is copied, it reveals the numbers: | |
| + | <pre> | ||
| + | 10-9|4-2|3-5|14-4 | ||
| + | 7-10|2-13|14-1|1-14 | ||
| + | </pre> | ||
| + | |||
| + | This was found by Discord user Varstahl to be a book cipher for the memo, revealing the phrase "w3trusTu." Discord user Randomizer found this to be the password for the locked zip, revealing another memo. This memo, when copied, reveals the word "together" at the bottom of the document. This was discovered by Discord user <W1CK.R> to be the "second decryption key," revealing the text: | ||
| + | |||
<pre> | <pre> | ||
##DECRYPTIONKIT############# | ##DECRYPTIONKIT############# | ||
Revision as of 02:06, 9 March 2017
| Bradwell Electronics | |
|---|---|
| Better. Brighter. For everyone. | |
| Type | [[List_of_Investigations#Investigation|Investigation]] |
| Creator | Bossa Studios |
| Discovered | 2016-03-05 |
Main Page > List of Investigations > Bossa Studios
Most of the content on this page so far is a rehash of this Reddit post by /u/blackbat24; all credit goes to him.
Bradwell Electronics is a promotional website released by Bossa Studios, a British game developer responsible for Surgeon Simulator and I Am Bread. At this time, the purpose of the site is unknown, but it is speculated to be an in-fiction promotional website for Bossa Studios' next game.
Email Newsletter
On the Bradwell Electronics site, there's a field where you can sign up for the Bradwell email newsletter. A few minutes after signing up, the following message is sent to your email:
Welcome to Bradwell Electronics - Better. Brighter. For Everyone. Thank you for registering your interest for the upcoming relaunch of the Bradwell Electronics website. When John Bradwell founded Bradwell Electronics over 62 years ago in 1964, he never imagined that the family business would become one of the most recognized brands worldwi$"%"$"!£2/.&%...
From this point onwards, the message is "corrupted", and is mostly comprised of Base64 ciphertext. For the full text of the email, check this Reddit post. At one point, the message becomes legible again:
>>INTERRUPT STREAM ----------This is a mayday alert. --------------------It is of concern to all of us. ------------------------------We ask you to trust us. ----------------------------------------We cannot do this alone. << END OF INTERRUPT
Encoding the Base64 in the text of the email yields an image which includes a QR code:
(Note: Amesbury is the location of Stonehenge.)
Reading the QR code reveals the following string:
/?decrypt50726f6a65637441
(Note: 50726f6a65637441 is hexadecimal for ProjectA, but this is not yet relevant to the investigation.)
Countdown Timer
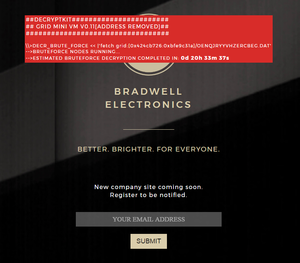
Appending /?decrypt50726f6a65637441 to the http://bradwellelectronics.com URL reveals a red box (link), containing this text:
\\>DECR_BRUTE_FORCE << |'fetch grid:[0x424cb726:0xbfe9c31a]/OENQJRYYVHZERCBEG.DAT' -->BRUTEFORCE NODES RUNNING... -->ESTIMATED BRUTEFORCE DECRYPTION COMPLETED IN: _d __h __m __s
The first line of the text contains the string OENQJRYYVHZERCBEG; this can be deciphered using ROT13 to obtain BRADWELLIUMREPORT. The significance of this is currently unknown.
Additionally, the final line of text in the red box is a countdown timer, which is counting down to 12:00 PM UTC, on March 8, 2017.
/__FILEDATA.ARCHIVE
On March 8, 2017, the text on the login page of "Decryptkit" changed:
##DECRYPTIONKIT############# ## GRID MINI VM V0.11[ADDRESS REMOVED]## ################################## \\>DECR_BRUTE_FORCE << |'fetch grid:[0x424cb726:0xbfe9c31a]/OENQJRYYVHZERCBEG.DAT' -->BRUTEFORCE NODES STOPPED. -->BRUTEFORCE DECRYPTION COMPLETED: ----> ARCHIVE DETECTED (OENQJRYYVHZERCBEG.ARCHIVE) ----> DECOMPRESSING ARCHIVE... COMPLETED WITH ERRORS: -------> TOTAL FILES: 10, RECOVERED: 2 ----> WRAPPING RECOVERED FILES FOR ACCESS: COMPLETED ----> RECOVERED FILES AVAILABE FOR DOWNLOAD: /__FILEDATA.ARCHIVE/ -------> ENTER SECONDARY KEY TO DECRYPT REMAINING FILES:
This leads to archive page, which contains a press release about Bradwell's involvement in the restoration of Stonehenge in 2019, while the other file is a passworded zip that has yet to be unlocked.
In addition, in order to access other parts of the site, a decryption key is needed to be added in the code of the website, which is heavily obfuscated. However, within the js of the website, Discord user Concerned Hobbit found large blocks of hex in the code which, when translated:
innerHTML addEventListener DOMContentLoaded decrypt50726f6a65637441 location href toLowerCase indexOf getElementsByTagName body DIV rootkit appendChild 2017-03-08T12:00:00 getTime floor tmr01 tmr <div style='position:fixed;width:100%;top:80px;font-family: 'Courier New', Courier, monospace;'><div style='font-size:14px;background-color:#d82c29;padding:3px;margin-left:auto;margin-right:auto;width:680px;color:#ffffff'><div>##DECRYPTIONKIT#############<br>## GRID MINI VM V0.11[ADDRESS REMOVED]##<br>##################################<br> <br>-->BRUTEFORCE NODES STOPPED. <br>-->BRUTEFORCE DECRYPTION COMPLETED: <br>----> DECOMPRESSING ARCHIVE... COMPLETED WITH ERRORS: <br>-------> TOTAL FILES: 10, RECOVERED: 2 <br>----> WRAPPING RECOVERED FILES FOR ACCESS: COMPLETED <br>----> RECOVERED FILES AVAILABE FOR DOWNLOAD: <a target='_blank' href='/__FILEDATA.ARCHIVE/'>/__FILEDATA.ARCHIVE/</a> ##DECRYPTKIT#######################<br>## GRID MINI VM V0.11[ADDRESS REMOVED]##<br>##################################<br> <div style='font-size:9pt'><br>\\>DECR_BRUTE_FORCE << |'fetch grid:[0x424cb726:0xbfe9c31a]/OENQJRYYVHZERCBEG.DAT'</font> <br>-->BRUTEFORCE NODES RUNNING...<br>-->ESTIMATED BRUTEFORCE DECRYPTION COMPLETED IN: <span id='tmr01' style='font-weight:bold;font-size:14px'>[calculating]</span></div></div></div></div> getElementById value together ---->DECRYPTION TIME CANNOT BE DETERMINED.<Br> ---->NOTIFICATION ON JOB COMPLETITION AVAILABLE USING SOCIAL MEDIA NETWORKS TO PROTECT ANONYMITY<br> ------>USE <a target='_blank' href='https://twitter.com/intent/tweet?text=Fresh%20air%20is%20good%20for%20you.%20BETTERBE2026'>LINK</a> TO POST A TWEET INCLUDING SPECIAL CODE 'BETTERBE2026'<br> ------>DECRYPTION SYSTEM WILL GET IN TOUCH ONCE JOB HAS BEEN COMPLETED<br> parentNode removeChild
2nd Key
When the text of the public memo is copied, it reveals the numbers:
10-9|4-2|3-5|14-4 7-10|2-13|14-1|1-14
This was found by Discord user Varstahl to be a book cipher for the memo, revealing the phrase "w3trusTu." Discord user Randomizer found this to be the password for the locked zip, revealing another memo. This memo, when copied, reveals the word "together" at the bottom of the document. This was discovered by Discord user <W1CK.R> to be the "second decryption key," revealing the text:
##DECRYPTIONKIT############# ## GRID MINI VM V0.11[ADDRESS REMOVED]## ################################## \\>DECR_BRUTE_FORCE << |'fetch grid:[0x424cb726:0xbfe9c31a]/OENQJRYYVHZERCBEG.DAT' -->BRUTEFORCE NODES STOPPED. -->BRUTEFORCE DECRYPTION COMPLETED: ----> ARCHIVE DETECTED (OENQJRYYVHZERCBEG.ARCHIVE) ----> DECOMPRESSING ARCHIVE... COMPLETED WITH ERRORS: -------> TOTAL FILES: 10, RECOVERED: 2 ----> WRAPPING RECOVERED FILES FOR ACCESS: COMPLETED ----> RECOVERED FILES AVAILABE FOR DOWNLOAD: /__FILEDATA.ARCHIVE/ -------> ENTER SECONDARY KEY TO DECRYPT REMAINING FILES: ACCEPTED -->SUBMITTING SECONDARY ENCRYPTION JOB TO GRID SYSTEM: [#####] ---->DECRYPTION TIME CANNOT BE DETERMINED. ---->NOTIFICATION ON JOB COMPLETITION AVAILABLE USING SOCIAL MEDIA NETWORKS TO PROTECT ANONYMITY ------>USE LINK TO POST A TWEET INCLUDING SPECIAL CODE 'BETTERBE2026' ------>DECRYPTION SYSTEM WILL GET IN TOUCH ONCE JOB HAS BEEN COMPLETED
The link is a tweet template which says "Fresh air is good for you. BETTERBE2026."
This page is a work in progress, and will be updated with new leads as they emerge.