Difference between revisions of "Mr. Robot ARG/Season 3/Episodes"
| [checked revision] | [checked revision] |
(Created page with "=Season 3= == Season 3, Episode 1 == Season 3, Episode 1 of Mr. Robot, titled '''eps3.0_power-saver-mode.h''', aired on October 11, 2017. The episode contained several nota...") |
m (Mattyb moved page Mr. Robot ARG/Episodes to Mr Robot ARG/Episodes: Argbox fix) |
(No difference)
| |
Revision as of 04:34, 29 May 2018
Contents
Season 3
Season 3, Episode 1
Season 3, Episode 1 of Mr. Robot, titled eps3.0_power-saver-mode.h, aired on October 11, 2017. The episode contained several notable ARG clues.
License Plates
Irving, in order to call off an FBI car following him, uses an NYPD plate lookup service. The license plate of the FBI SUV is UVM7482, which he uses to find the VIN number, 1HGCM8Z633A0043F2.
Subreddits
A poster with a QR code on it was discovered in the episode. Scanning this QR code led to https://jobs.runpula.net/, which was ostensibly a resume page for a Dylan C. Roberts. Prominently displayed on his resume was his experience with E Corp, which confirmed that Dylan C. Roberts was, indeed, a fictional character.
Several "Contact Me" links on Dylan's page led to the profile of Reddit user BCC4Life, who was active 2 years ago - presumably, BCC4Life is Dylan's handle online. His activity was confined to the /r/inside_e_corp subreddit, which also only displayed activity from 2 years ago. This was particularly interesting given that, at the time of discovery, the /r/inside_e_corp subreddit had only been a community for 1 month (according to its sidebar). This discrepancy was later fixed, but suggested that the Reddit adminstrators may have been involved with the ARG themselves.
At the time of discovery, several other users had posted on /r/inside_e_corp, including:
- officedrone13 (moderator of /r/inside_e_corp)
- EnnuiOtter (moderator of /r/ZenArtofAutoDetailing)
- WhatInTheActualKylie (moderator of /r/TheEclecticSlide)
- KrullFan (moderator of /r/REALMysterySpot)
Some of the NPC users from /r/inside_e_corp were found to have posted on three other fake subreddits: /r/ZenArtofAutoDetailing, /r/REALMysterySpot, and /r/TheEclecticSlide. These subreddits were similar to /r/inside_e_corp, in that all of their activity had taken place 2 years ago. All of these subreddits were private - only approved users could make submissions.
Four posts, one on each of the four subreddits, conspicuously mentioned the number 264 (1, 2, 3, 4). In these 4 posts, the following five emoticons were used: :O :d :c :x :E. When rearranged, the letters used in the emoticons spell codex, and when combined with the number 264, this clue hints at the H.264 codex, which is used in video compression. At this time, it is unclear if this puzzle holds any further significance.
Minesweeper Game
One of the episode's main plot points was hacking a minesweeper game for a "Capture the Flag" hacking challenge. After the episode aired, whoismrrobot.com, the hub site for the Mr. Robot ARG, was updated with a minesweeper.py file, which generates a Minesweeper game identical to the one described in the show. (Note: The game will not run properly on Windows, only on Linux systems.) Additionally, the game is vulnerable to a very particular exploit, the same exploit that was used in the show to hack the game and win the challenge.
More information on the Minesweeper game and its exploit can be found here.
Season 3, Episode 2
Season 3, Episode 2 of Mr. Robot, titled eps3.1_undo.gz, aired on October 18, 2017. At one point in the episode, the subreddits discovered in the previous episode were shown. Additionally, Episode 2 contained several notable ARG clues.
EC_NY Portal
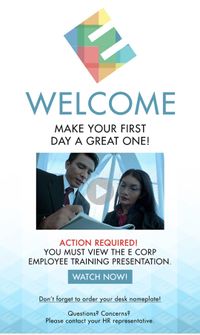
Immediately after the episode was aired, an email was sent to ARG players who had signed up for E Coin. This email encouraged players to visit whoismrrobot.com, where a new desktop portal had become available. This portal was titled EC_NY, and was, presumably, the desktop of an E-Corp machine located in New York. The desktop contained several items:
- A folder titled "HR Form Drafts" containing several drafts of a complaint against an employee, Samar Swailem
- A folder titled "Documents" containing floor plans, a map of E-Corp storage facilities, and a link to various E-Corp employee forms
- A "Nameplate Maker" app that allows a user to generate their own E-Corp nameplate
- The Employee Training video that was shown in the episode
None of these items appear to have any hidden meaning attached to them.
"Plans" Archive
At one point in the episode, a URL is visible: https://sandbox.vflsruxm.net/plans.rar. Visiting that link yielded the following text:
b3VhcUs5UjhqWHhmcEU2a0dWLnBuZwoDAuhpGqmXR9MBykrZA0BlRWMiPzYAaWtG 4y5CKWrcagjRpWw+CVQlthXGUgSkhQFSEhBGwaFVq2EkwkYSBZ6Zla40lwY0rRaF YNLMIiQT4VjFG+hgzEBJRKSWJUkjMwKs+JICQKJIEmY5LLcuW9n5fczubmbvebzu 83e/od3nd3m973dzeeec5mefmqzezsyKE+oJECBAomSmJ6C7VNf855mq/uDUU3vp 4Dq97Nz5F/BaAle0uC8p5xgnMS0+g+9yy3BrKldbq+D5tF18/XHvSipzd2CSz2qa buoI+K3HqzKb8us7zREMzox1pxL3fDuZSJ/WjIHmVg5n3GB8J49zsgrIpCs3o2Fw elehOp1zb+sPUBNrznGIbSYOKAZ9UXYnXzIr+eO7tbYlRR4HZT1ZQf4cVQpoG8PS EZMt+g1q0Oe9/0uAZ8X05JXXez3sxGm3+uFtQK6+Hto065Ku72KlNiPKTQIeyT5l crgkTqA4NF1QqPR7OXBmUrhWxcrzIaRqr/WBQXahXUrJtkXnJpgsd0wEboBRIbP4 sfItuGqV+KqWOblf5Ot64Hvy6jXyUEMgiDY51dmWVjyMKv5G5LdwZyyIJLKbIri1 C6Te+w/dZRNa+LP+Nt0x/ZZdyAlVWR3jJ/scC6msO/Q+4WmJ7n6Kzk80AobYK4pI DOwx2Uei8FCZS/JFYrCthCdW4T4VpcoPaJZY3lI7Rfx6qhjsmRWpLoFK0b7aLR9l YfKROnNI885Mp2ywOKkoSxboKOJlVp7WVGwTsTQcNxc7vKbP/yEEPbVJRb8ZdbtE PVMYEWp6/CnHuhT7N1CWQP+lLHLU3LKw5+NWfyakyxF4hXHJAHMZc2t0UdKNrA8m p7FsXvA/shbhioeagOCmZTIkFWPjXHwylCrUYlP8AOPrfEJur1n4og/+/HL/c6Y5 pksv3JtvDwlx6u78GsXPu7kmlFPzO1sO/p9Lt0FKp9MgDSZdvauPtO9lWFIJfHp7 /8N08CseGojeBhTMJQokVvyljS7QLP20EevozBIfJAZ+C7fFYeeaDvOmkqvrU0ip jgIWnUv/IJbAhKH3Cr+jg5aUhW4UTHd3Q0wdnNq4afNttSRwaJuX7MGjFTdewGM9 LbYN/wIRSwib3+M2mGuywZ92YVVFpjZ4vMhNMSw9eLUFaMhfDXMnUe2M51XusaVF qiQCyf63UDCPCQ8P0bfElu/UvS2+NyX0ALh+pSx9dxrjn3tmO9htRYwHwu5ebeXR ZD6p9CyMpd4is9eDfl9+IspNGtGMaOntIJiBc8RzmvR4oOxlK3jP9ZJ4Rc+Qu4hx k+O/EeVJkZ2Y6hDg/OAdd1ZRAwUEAA==
This data is encoded in Base64, and can be decoded (eg. with this site). By opening the decoded file as a RAR file, its contents could be extracted. The RAR archive contained an image of a QR code, which, when scanned, led here. This page contains a real-world exploit that was used by the FBI in this episode of Mr. Robot, to view a target's monitor. Because this page is publicly accessible, it is thought to be the conclusion of this particular puzzle trail.
E-Corp Webmail
Another link was shown in the episode at one point: https://webmail.e-corp-usa.com/owa/. Visiting this website yields a login prompt. In the episode, two characters' login credentials were shown:
[email protected] / aboynamedg00 peter.mccleery / tapitback!
Using each of these login credentials yielded the following 2 error messages:
INCORRECT FIELD INPUT. ERROR #13489-RARECHPOT INCORRECT FIELD INPUT. ERROR #123578-PARMLETOR
Both error numbers contain a series of digits followed by a series of letters. By taking the letters in the positions of the digits, two distinct anagrams were discovered:
RARECHPOT 1 34 89 R RE OT Anagram: RETRO PARMLETOR 123 5 78 PAR L TO Anagram: PORTAL
Logging into the website with the username RETRO and the password PORTAL links to a PDF file containing a presentation that was seen in the show.
E-Corp Badge
At one point in the episode, a QR code is shown on Elliot's E-Corp employee badge. Scanning the QR code leads to this URL: http://www.e-corp-usa.com/company_directory/elliot_alderson/
No puzzles have been found on this webpage.
E-Corp Shipping
A link was shown in the episode at one point: http://www.e-corp-usa.com/cp/directory/shipping/1088989/. Visiting this website yields a login prompt - the correct login credentials have yet to be determined.
Season 3, Episode 3
Season 3, Episode 3 of Mr. Robot, titled eps3.2_legacy.so, aired on October 25, 2017.
Babycam IP
At one point in the episode, the following IP address was shown: 192.251.68.238, which links to https://y9bukwer.bxjyb2jvda.net/. This website is ostensibly a webcam monitoring site, which was used in the show to watch an infant. Instead of a video feed, the webpage randomly selects an image of static, which is a GIF file.
In the last frame of the static, a hidden message can be seen:
Cleaned up (the message is written using color index 4, so setting all other colors to white makes it readily apparent):
68 65 72 65
This is hexadecimal for the word here. At this time, the significance of the word is unclear. The static animation changes roughly every 6 hours. There have been four distinct static animations found thus far. Each have hidden messages as well, but on a different frame, and with a different color value:
| Link | Frame | Ciphertext | Plaintext | Color (hex) | Color (ascii) |
|---|---|---|---|---|---|
| 1 | 3 | 77 65 26 23 33 39 3b 72 65
|
we're
|
74 44 44
|
t D D
|
| 2 | 5 | 61 6c 6c
|
all
|
44 4c 74
|
D L t
|
| 3 | 2 | 6d 61 64
|
mad
|
4a 74 44
|
J t D
|
| 4 | 6 | 68 65 72 65
|
here
|
74 44 71
|
t D q
|
Together, these 4 words form the sentence we're all mad here, a reference to Lewis Carroll's Alice in Wonderland. The meaning of the different colors is currently unknown.
The Daily 5/9
ARG players with access to an Amazon Echo device or Reverb (for Android and iPhone), were able to play a minigame called "The Daily 5/9", which could be enabled as a Skill at https://www.amazon.com/gp/product/B076K7QL3V. The objective of the game is to get a file for James, the main character, from Phillip Price. Once enabled, the guide to completing the skill is as follows (the guide will begin after you say "Alexa, play The Daily 5/9" and listen to the news segment from Frank Cody):
1. Yes 2. 1 3. Hello Friend 4. Office 5. Bus 6. Ignore 7. Steal a Badge 8. Steal Co-Worker's Badge 9. Threaten Her 10. Reconnect 11. Decrypt the File 12. Find Another Way 13. get in Vehicle 14. Yes 15. Purple 16. Yes 17. No 18. Seagull 19. Go to the Town Car 20. Yes
Note that options 4-18 are only recommendations. Any choices you make between that range all lead to the arcade. Also note that option 19 is not specifically said in the dialogue. Instead, it's implied as "something unplanned" by Jason. After following the steps though 19, you will get a message from Whiterose:
[Whiterose]: I am both impressed and surprised. Usually, I am neither. Your bold choice has earned you 80 seconds of my time. [Jason]: I... don't understand. [Whiterose]: Oh, no. You do not speak. I have no time for that. What I do is look for potential that will help mine. At the beginning of this, you were like a flipped coin, tossed into the air, how you landed was yet to be known. What fascinates me is the quantum state suggests you were both. Heads and tails. Yes and no. A 1 and a 0. But this lasted only until you were observed. Until you were tested with the choices you made. Only then, your nature became known. And gave me a better understanding of your usefulness. I look forward to meeting you in person. [Jason]: What? [Whiterose]: I'm not talking to you, James. You are insignificant. I'm talking to the little bee, buzzing in your ear. I have an appointment to keep. And James, drop this silly charade. This test is over.
After the game is finished, the player is told that they are now a "full member of the Dark Army", and that they are "now being monitored and will be notified of future missions".
Season 3, Episode 4
Season 3, Episode 4 of Mr. Robot, titled eps3.3_metadata.par2, aired on November 1, 2017.
Dark Army Mask
In the scene where Eliot is hacking E Corp Shipping via a Struts vulnerability (not the same used against Equifax, but similar), the IP address 192.251.68.224 is visible. The IP address redirects to https://y8agrfx3.bxjyb2jvda.net/. This site appears to be a Chinese file browser, with folders called Video, Image, Document, Download, etc. In the Recent and Image folders, there are two images. The desktop Ubuntu Kylin background image appears to be a stock image, but the Dark Army mask (on right), though appearing low resolution, is actually a very high resolution 6526 x 8192 pixel image.
Zooming in to the center grey 'pixel' just below the black mouth, and adjusting the color curves to separate the low contrast data reveals the following message:
This is a misattributed quote to the Mad Hatter in Alice in Wonderland. Nothing else of note has been found on this website.
Also shown on the same screen as the IP address above is a link to https://www.ecoin.services/manager/. This appears to be a static page, with no relevance to the ARG.
EC_NY Portal Update
After the airing of Episode 4, the EC_NY Documents folder was updated with two new images. One is a document from E Corp Information Security Dep't with a reminder of E Corp's company policy concerning password strength:
- A minimum of 8 characters
- Uppercase letters
- Lowercase letters
- Numbers
- Special characters
There is an conspicuously underlined and bolded word, overlook, at the end of the document, which is notable for being eight characters long.
The other new image is a flyer for a screening of the cult film classic Hackers movie, with a quote from the movie about the most commonly used passwords being 'love', 'sex', 'secret', and 'god' (left blank in the poster). There were a number of references in Episode 4 to the characters Elliot and Tyrell becoming gods.
The significance of these two documents is not yet understood, but appear to be hints for guessing ARG passwords.
Season 3, Episode 5
Season 3, Episode 5 of Mr. Robot, titled eps3.4_runtime-error.r00, aired on November 8, 2017
E Corp Website Changes
The layout of the E Corp website completely changed to look as website seen in episode with news about the U.N. Vote on Congo Annexation. Changes to the company directory were also made, adding features to search by name and zip code. Frank Bowman, Angela Moss, and Samar Swailem were all added to the directory. Marketing and Legal sections show [SYSTEM ERROR] Please try your search again later. if you try to access them.
Password Reset
The E Corp password reset link (https://www.e-corp-usa.com/password/reset/) was shown on screen, but nothing has been found to work on it.
192.251.68.232
This IP address (192.251.68.232) was shown on screen, and when you connect to it, it leads to the website https://ycg67gca.bxjyb2jvda.net/ssh/terminal/. On this site there is an empty folder, root/home/samsepi01, and a folder containing UPS logs:
/root/usr/local/logstash-ups: 09/25/15: 06:05:10 192.251.68.229: Pinging (via IMCP) device 09/25/15: 06:05:12 192.251.68.229: Device connection passed 09/25/15: 06:05:13 192.251.68.229: Testing FTP Log-in 09/25/15: 06:05:19 192.251.68.229: FTP Log-in passed 09/25/15: 06:05:28 192.251.68.229: Saving data file 09/25/15: 06:05:35 192.251.68.229: OS Prior to firmware transfer: Network Management Card OS v6.4.1 09/25/15: 06:05:41 192.251.68.229: Saving event & configuration files 09/25/15: 06:05:49 192.251.68.229: Validating firmware file (1/1) 09/25/15: 06:06:32 192.251.68.229: Signature check failed, update aborted 09/25/15: 06:07:20 192.251.68.229: Encountered 1 failure during upgrade
Kibana Monitoring
The website https://ycg67gca.bxjyb2jvda.net/app/kibana/#/dashboard/Priority-Host_Monitoring is shown on screen and automatically logs in as admin with the password tXUzKSoPS5. There has been nothing found on this website so far.
192.251.68.233
The IP address 192.251.68.233 was shown in the episode, which leads to this website. The password z1on0101 was found, along with the PED code 022350 in the episode. After inputting both values, you get the message Key confirmation: B-TUDGTDL-0112180501042508051805. Putting 0112180501042508051805 in a letter numbers decoder, you get ALREADYHERE.
WIMR Updates
After the episode aired, the Origin node on WIMR updated with a folder named protest with photos of the protest signs in the episode.
Emails
On November 9th, people on the WIMR mailing list were sent 1 of 3 photos that when overlayed had the word DISTRACTION. Entering distraction on the Origin node on WIMR showed a hidden folder with images thought to be related to Alice in Wonderland.
Red Wheelbarrow Update
Underneath the news section on Red Wheelbarrow there was a string of text that appeared:
+++ ATDT 0118 999 881 999 119 725 A voice *can* just go somewhere, uninvited, and just kinda hang out- next time we will play fair, even if she doesn't. She can't stop us, and neither can you. And if you can't beat them... Javaphile has nothing on us... Shout outs to Eagle Union, THe GreEns, 888169 and Honker Union- EBGGuvegrra, ernyyl? Cynl gvzrf bire fbba... +++ No carrier.
The text EBGGuvegrra, ernyyl? Cynl gvzrf bire fbba... was ROT13 for ROTThirteen, really? Play times over soon....
Season 3, Episode 6
Season 3, Episode 6 of Mr. Robot, titled eps3.5_kill-process.inc, aired on November 15, 2017
UPS Patch
The URL https://ycg67gca.bxjyb2jvda.net/files/ups_640_patch.zip was shown on screen as Elliot attempted to prevent Stage 2 in the recovery building. Decoding that text using Base64 is:
d0B83jry8pzNwRX9H3F8h3Y5J0IB6Y2u7tYzATP8Rg2PPd7Xl5ZZIe0wQ1V8NH8i u2QTlCnwSObcIGLd9T3Hpt88fhLntcqP1Rk4SHG0UJsJMBGkIwXLKxWoRO0bovo7 tRop2d3k6veISkWsN9lA0ZMb1aTSxTpRmBZDFsjCnuHA8Pgkl8DOWN5OVER5DPdo N0tgNN9dUb8SXmJFfqIU4G0H98IiesHYXhvj0ikegHLqK1iu1ZEqcF9PTbbOF9TY eVFdObJUNh8WQlVUGBQiP7EIWi+NQU5VOm7WDjUpws21y70Cwg3aAIWMNl0UJXg9 i4I2K26xB4oGK0XhNpQa691iE9Jsp0J3eXE6n6CffbjGRhDEk7noeWWGFMUeij0t VU6uL0GkzPRV09BlYHeVT1pkhJvXSLraKeBELHD4+rzp7KfkdoEhDuXSJWK5JF!k pU0PMYTIAHOSRWCFSTAUUUTESTSTMNAA!BGnzbKYmyOac1BAX9lTKcQQ9ZHS2OG8 hzIiLtpMslA0Z1bvPSa12mTX9oXzjRsXH7qUv472xsaOfHJ5ix7VEOVDbnjTa7hy VxlyiOwUhpUnJtoopDIaAqwa7z3fmGypAW5oW5SESYhGmpSsbxAy9tyJmyJ5Lwyn dBGox1AunmEFeSLzjROjjZjiyvepRIb+hCOW4GvbpeWKygJ0r5EyyzEufQLKzDKK Gmw2h4zbQBjTGP89OOqKe4KS6cKXQ2BfLY6M0xZvUgCXcN0kKndr7SxQMp7eMsn7 GmLUUjsrTjM8dTgryqK2Wm2YYgdF8KKJvxg7sRTCIb6zrykOocM7NN1IMio1TAsR hZnuX9uAfV0wFVR2jF7xtJQP53oLp40kssmHulHD3EX3GSMdqDnQeKCIirSGjWLw XCU3dVvnO9stg96amtT4dBD8S9OCvGitRSnPju8QWWBwR3tnytdYEFECNWh2Qsio rT6v!8MotPTjxTyNvntzgjUj9saTs!QTih7k6GR9xqLMlZ1s0yk9w4HEy8N2ZGB2 vX89+0oPGaILKMiDSx4LF4HYBceEOat1umUJa96YrQ81nw9LbczyO1MaLDiIhnM1 uy4Fjs4Jy3bdhtgrqb0JplzJhIGtU0AWaLBUi4rgDnmEekojZm4j6TZ2YgRxSz2Y QdiTeWsbeswGvDuwnnj7Yq3xY770k3cF4bSX85tjMW4cRpQ2arJ4QJnpfa7x1io0 58ZmZdFq7jSTzvUYWk4TbsiWuJ8rNmHkVHjDXxOqthW1037kEOnza1lyFOURlPah vXjArmi9X81lkYnzDCfwN0Q5GyOFnu57Zu2FrS2xw7QjtXuVbbfPjZHvl7LuSN9z YGp9Ec9jgNxFizFdhfjEW4k7V7bjPZLsKHnYXy8fvchUsmBiK7M9RY5soN4i09XV PouVetpqqoTpIaYKplZSNwtpZxSrkNjJDagtjEXPpLDRZ0qDhK4BeCBG9ZzqB6YS KfCYuydms3b7Te13c658WhYQBxSf92M8vBWPzppFS1wxl58vXGzIr5AhcxZoVIHF ymPdT8bSNdL5dJHfYuntf5RHzatwzPnLRmCdrnKYClYnBsdO3SwEii5Y2hfBzwqI pOAz15jEhyUkJe77!lqtzVwSGsQPiahrGl49izodZPkZVkTp11crCIZoixTnJ!wh tVRHZ6rgvc9Uh4WHvKFqDq+Hymv2c56IU7NhO8vSswbz26iI8NtzVUBkZ7bMpDS2 2kK86T5z1hZtI2rwSGryLZmhAbLoqeJeJDRAILO2D4iUeqoZ719gLBJqn5A72dS4 HEq!SnPRZPTiSReFCgmVVGM32dPkBL9y1HbUCgn6bbj9ar9NHcsHyJJR8zD7oPLl SAK2NYl7EJsXvfQupDRNUBysfHK9YNnb1ePPvk8SWsSGW39ZWe6D0VSKmpqmcI87 v0CDc9N3OGkKuZzgT22SURPIfnmu5my2Sn4hKYt1fWMi1iFI2c1VmNXdQirTorSz gtOWeKcIX45kguMsrWE
In that text, the keywords 8DOWN5OVER, RAIL, and FOUR were found. Going down 8 and over 5 in the text gave this line YTIAHOSRWCFSTAUUUTESTSTMNAA. Using a rail cipher with 4 rails returned YOUMUSTRUNTWICEASFASTASTHAT, a reference to the Red Queen's race.
Website Updates
The IP address 192.251.68.229 was updated with new dates, and the command upsfwupdate -status
192.251.68.242 was also updated, allowing people to simulate the hack in the episode.
Steps: unzip ups_fw_patch.zip gpg --verify hashes.asc sha256sum --check hashes.asc scp apc* [email protected]:/upsfw ssh [email protected]
The WIMR Origin node updated with a new terminal icon, along with new files if you cd .. -> open tmp
Red Wheelbarrow Audio
After the episode aired, the Red Wheelbarrow website updated with a new commercial. The commercial was also aired live along the episode. Reversed in the audio was the message Do your homework in the dark, and in the video, segments of a spectrograph appear, that when assembled seems to say level 33C plastic forks or level 33 seed plastic forks.
Season 3, Episode 7
Season 3, Episode 7 of Mr. Robot, titled eps3.6fredrick&tanya.chk, aired on November 22, 2017.
WIMR fsoc Node
After the episode aired, the node fsoc became available on WIMR. It was discovered that if you went to the directory /tools there was a file called data.json:
data.json:
{
"fragments": {
"0": "0fhizn7z0w",
"1": "m91ft6waa8",
"2": "xf49c7k6j1",
"3": "5kkqf92qm5",
"4": "s2vvij1g3k",
"5": "7op6ypyn7k",
"6": "4jpg7moa0g",
"7": "h18i60bahg",
"8": "rigw2zlzcz",
"9": "3tkcl5awgy"
}
}
Using that as a guide for the files in /tools/data a base64 image was assembled. When translated from Persian, it was a quote from the Hacker Manifesto.
Season 3, Episode 8
Season 3, Episode 8 of Mr. Robot, titled eps3.7_dont-delete-me.ko, aired on November 29, 2017.
Trenton Email
As shown in the episode, the email [email protected] when emailed auto replied the same text as in the episode:
I may have found a way to undo the hack. I've been investigating Romero. He installed hardware keyloggers on all the machines at the arcade some time before five/nine. The NYPD imaged all of his data after he was murdered. I was able to get this chain of custody document from the NYPD when they prepared to transfer the evidence to the FBI. They couldn't get into the encrypted keylogger containers. If Romero somehow got a hold of the keys, or even the seed data and source code for the encryption tools, the answer might be in those keylogger captures, but the FBI probably has those files now.
WIMR Update
After the episode aired, WIMR updated with an article on the Origin node
Red Wheelbarrow Update
After the episode aired, the Red Wheelbarrow website updated with a card on the home page. This is thought to have links to the previously found message in the Red Wheelbarrow commercial.
E Coin Promo
On December 5th, members of E Coin were able to redeem a writer's room promo for episode 9. Inside the video was audio that revealed Cheshire Cat from Alice in Wonderland in the spectrograph of the audio.
Season 3, Episode 9
Season 3, Episode 9 of Mr. Robot, titled eps3.8_stage3.torrent, aired on December 6, 2017.
192.251.68.228
The IP address 192.251.68.228 was found in the episode that has a file in base 64, that when decoded outputs a zip file. Running the command dd if=decoded.zip | gunzip -f > fU8extI11NDuLxcSV80A.bmp outputted an image of a rose.
192.251.68.236
The IP address 192.251.68.236 was found on the website that was used by Elliot to sign into the Dark Army's botnet. The username and password were found from the keylogger used by Elliot, garyhost/hunter2. Using that gives an error message that translates to "Password Update Please enter the update password". Using LSB extraction on the image found on 192.251.68.228 resulted in the string "p":"qBqOR5VJJzgJERxpXZ4l2JXSQOthufVnAynQMROT" being found.
Using the username garyhost and the password qBqOR5VJJzgJERxpXZ4l2JXSQOthufVnAynQMROT allowed players to log in to the Dark Army's botnet. Using the locations listed, the following locations were found:
50.9413° N, 6.9583° E Cologne Cathedral 37.8267° N, 122.4230° W Alcatraz Island 27.1750° N, 78.0422° E Taj Mahal 31.2397° N, 121.4998° E Oriental Pearl TV Tower 37.9715° N, 23.7267° E Parthenon 35.6586° N, 139.7454° E Tokyo Tower 55.7539° N, 37.6208° E Red Square 39.9489° N, 75.1500° W Independence Hall 34.3568° S, 18.4740° E Cape of Good Hope
Taking the first letter of each location spelled CATOPTRIC, relating to a mirror, a reflector, or reflection.
Season 3, Episode 10
Season 3, Episode 10 of Mr. Robot, titled eps3.9_shutdown-r, aired on December 13, 2017.
Congo Shipping
In the episode, Elliot is seen typing the Dropbox link https://www.dropbox.com/s/0cp05oezsolrn4d/ which includes the likely location of White Roses's project.
{
"DD":{
"lat":-10.617537,
"lng":22.339499
},
"DMS":{
"lat":"10º37'3.14\" S",
"lng":"22º20'22.2\" E"
},
"geohash":"kqpgs75hk5",
"UTM":"34L 646530.0545339 8825993.18511926"
}
Emails
Emailing the address [email protected] as seen in the episode led to the following reply:
-----BEGIN RSA PRIVATE KEY----- MIIJKAIBAAKCAgEA05b6qDVeCiapeVJ96ekFs+MTYgOuNkyVHqE9WaE4zcW/+uoN Hg4fzB8TYK1NJAdj+S+4+4g/1N6zmYg6zr57cBp2GdMI/lXNuDdtw2jZbd54YODA rRyR8kReNdPuDbbk76fxrB7iASaCSEraOOQdtRkRTLNPlxOzw5WZ+UBJ2JvSNAKT Vsp2GaeUqYEwn7aQ4p0RrMNAnFPPw8G1Z0YKxGnoV0+ntA/y3MD88h1+uCurPf4P +bsxOxn/RzHBHiPZHJJcpKID5/op6F6KdqBP6BrDiDu05ZKnamdnmBFBuCEzrb3E 29lt944DtwCC8wl0YM4INgEhOk0mDFwYYWkBXrQC2jH7tQyaMM9RPbE0KzVtn5iT Sk/Zp0IRWwmwbUuCeLI5/DNUj72MCXZ3cHNVWcm3nT+j8WFP73c/dY4Rwd9ZlgFl Vd8NNFRfHAjqyMSNuFJGBYHK5ZkP1ntRsjJKod1aLK6nOBe68T2nGXODWHIpoDti uxAXteCX9Cb0QniVf9mronbW8C1p+IyXF/E3hbB83sBL4O7cLl0sKHgUou37XBKL 8xUrzZmQnzoDg9QbQQCqNMoyZY+Blthrb2p9bpYOFbtz+iXHsRrZkKkCNkyiQrNF dJseqXxR2R7NY6MEY5rcQpSrQaYO6B6asm4PZXre5+dQxyosmVQEw2V/bq8CAwEA AQKCAgEArbI7guqMkHi8l0QI6YTJkarPtp6e3SRxJfvniTS4lPPJbgnFSu79W2wH VE3wDaujfmSWzqZDAFTxyw/ydtYYLycJ3JlJwMBfaOLX0Jq6I1+GIsFear4RcXh+ fmHEAq4psjOESW/wyFD8kqwgCKP7Xzd85CIvLC6YW+7rv5nvBUqlfNzAZ3c9DEJt 39iWOgZ9Wgrm/5Qp7is/W8whRu5Q2Hy4pzRUz5RoIqCrBXcBF9+BbBqssq3g9Eub LK7DgiKbkMD2HJCD9GOBE6jIsilYb4nJCoU5M1z44niQql1APg/DhNVMTc5oX9jN Y+WfmjQgvXdldi/nPx0mJu9TdGPnIoEsJMW19lPgElRfq6E0qtFw1+ppqwb0TTaZ LZk+N3LUOqgaNbTpEkSKSI6BCm9WTTjGmeFkqz4viwTzOnUfPJqVwQA8FsaqhPJb XrFHud3e+YkhcB9OVsHV7vlq/3KPrFSkgYTpAjjLnGfxId++A8mLC5Cf2cobzwC5 Jla/HQ8Rs7nFVZ4P2TohfF6Vm5KCF5GdrZ8nJGkOAXJTkIiLEu5W8pjIuFBD+6OZ 4H9iAWsUw1M0Lls5Bvukef1zjnYpxiTMy9xzbZ5HTRi+5DoaCalJB+3YRD5sTK6f JNIBXTBhs3UOKQzYRC2sDeXMInymJQECAwfrPrakY4VI3fxDEkECggEBAOWUpWsb 3pOfmFHAvdc9lvRw+YC6cqnvpsMg+pddJGSY32IXtCzWHaTTLaXKHqWDHE8Wfkkm fyQUzkTYKRlfcsmncGg3VlM9nZP0c8Xw7O2DVkHxNdnp+gy/JeKJ8mgXHXQbl0or eVcCHBlsY4qxPkb5faR0hRkc9fqqiTVqMjVCJHmz3PiCUFCtKiwMboXZld/EbXmb M0z+48GSWleD50PwRxkvbiJteVzb+0PWEfLPng/fmMMf7h82VmZHYiA9OdKF9pr7 NK3jspPCXokzw13XTC/M9OH527jWDAQY6fIOPbU1wOfwAdmqGsDZEO5zHD+vy5Zt ypcv3mgT4CnEmFMCggEBAOvwVCKaRTNS9R/LzsKM9lx96ucTZsbYW2yFsXrCDmNf scT55xx239EYuZbYhWIDImr3NzYlEiULlA+7nqQBcRufg9ySbGeG5uW4f8Y8/mqL vL0aVZwVzeSlbEUPzkRS9z0Ld+wHEvx/U6i2wxOSBNC1YhFWY3IF75zM1kEv+qZO NGC5YfhsV/HGjvURwEJNyVmfSKx/GSHfOJABLmq9mPDDPsXXUWajBDjy5gBxlK/k rE4iRSlpUyN/HDJtsVmqsmQyu/6iN2T8asovAISxKFgI99nrc3jO3zjwnLc+qX63 7a2btF2VhSDJeOMOmc4juGP/Fsl9qLQqtGd8PCvZ1LUCggEACci4+ASbCr2Nd0Z4 kLi+OzKpX3QSuO1OtRgttc+xYlwlgP+znQmO/9xEIMGpZrJcvX4e6a0rU/VTCRoR PlSUBsYNA1QAaNHCanDLkk7/OewT/AF0oxHWpz5qNepdG1SI287lNrL9m9iqK+cz otCE7+9oDF8u4PAcB4/HAzDAbQahmVIyA6FCHP4UQwZQm4G3Ym7zn3Ae0pQ2TqSX Fw23CG0wCoG79tmlh3CUl8KCx09T1CdaUk6FDm15Zyh5pRgW48LzzI0SJKsEjEmH T9+V3uTzCUJ52TuVwp3Uq0QIjFlRBe0BiKDw4z7dnwRhNVhQhuJOEd4h+SmAF/1o 2z7WowKCAQAdPlV/UHXBTcf6H+3JqWUjw6uo5nu3q7txMQT1fTYBVSwYiQz/NzC4 nwLp0n59znumnGuod2HPW6cHaC7ajx8w2E2kujVbg5n84ShdLtQt6pIDMk9oID+7 1lEcIkBjsZDZbSF5DMtqpnF9GOIG+/NC1yiHk5iR2nB/k9f+jm7XzBur3W5qNyuT WRQBBik5TqDlTdvZHYvE6gD9wFe7fTKGrPyL0wtQ2GW+lUSyy2Eth/9fU9oUruxS GwAos/XmckTYLH2mqv6IssydsMO0rqycdMgbp5ZRY/rA+PnDsK2bejqoaQMrEkxE 6xPjuLyRk1XYdxag9MVDR4PCy+A9Yyt9AoIBAEwEQ9BnpAhzrkHRFNCBg529ouzZ b6jow+PYQVn3WeJta0wE9U2oqA/mqUc+9n5JET/KQvL8MgaBe2q/nBPl4UpeYSED gJV5eqcObMqInN61d8JDJQtL/+UDfioTyUjhe+//pWvAdGWAcORKLaTg5YLh8iVR Znz3PxfE5zGQtAfhmwNXeYM6bQkfHLrOT2fcCZokmh8Pki0typ/8DOcdj4Ag8Unx 4ChX952jX9nk1ZwFZ89Rh4RivqXRoqp5aPs/xBtRDBCL49NF2QFgXArj5LvO8b6B m/YPKCGUyJQoTt0jHdNwmTP0mBdIYT7sJIVdHk/zBWHp1q9gxKE4Z4VghWw= -----END RSA PRIVATE KEY-----
Emailing the address [email protected] as seen in the episode resulted in the following reply:
We have received your request and the following ticket has been created: 5yc9elk3xu
WIMR Update
On WIMR A new node, DA_remote became available, along with a new document in EC_NY node regarding passwords. The password for DA_Remote was CATOPTRIC previously found on 192.251.68.236.