Sombra ARG:Cryptography
Contents
The Base64
At 0:08 seconds in the Summer Games youtube video, you can find a base64 string. You can use , and . keys to skip frame by frame until you see it.
Base64 is a binary-to-text encoding scheme that allows you to safely share binary information. Blizzard most likely uses this because reading information off a video is hard enough, this makes it much easier.
Unfortunately the base64 doesn't use a monospace font, our reading skills are pretty good, so we can narrow it down to 16 different possibilities for reading the base64, since characters like a capital I and a lowercase L look the same. However if we let the computer try and figure it out, there are 78732 possibilities.
The Decoding
Since Base64 is for encoding, decoding the string is very easy. Using our best guess base64:
U2FsdGVkX1+vupppZksvRf5pq5g5XjFRlipRkwB0K1Y96Qsv2L m+31cmzaAILwytX/z66ZVWEQM/ccf1g+9m5Ubu1+sit+A9cenD xxqklaxbm4cMeh2oKhqlHhdaBKOi6XX2XDWpa6+P5o9MQw==
We can pass it into a tool like so:
$ echo "U2FsdGVkX1+vupppZksvRf5pq5g5XjFRlipRkwB0K1Y96Qsv2Lm+31cmzaAILwytX/z66ZVWEQM/ccf1g+9m5Ubu1+sit+A9cenDxxqklaxbm4cMeh2oKhqlHhdaBKOi6XX2XDWpa6+P5o9MQw==" | base64 -d
Salted__���ifK/E�i��9^1Q�*Q�t+V=�
/ع��W/
�_����V��?q����f�F���"��=q�������[��
z��*����Z����u�\5�k�C
Please note this decoding is useless since your browser kills most of the actual data. Use base64 to pass the string around.
The Understanding
Our best guess so far is that this decoded string is a OpenSSL salted encrypted string. The key identifier is the Salted__ string in the output.
You can read more about OpenSSL salted encryption here, but the gist is pretty easy. OpenSSL is encryption, salts are unique inputs. Salts are added to encrypted data to ensure uniqueness. With the string we have above, we already know the salt. It's the 8 bytes after the Salted__ identifier.
Since we know the salt, and we know the input data, all we need to decrypt is the password and cipher method. Since OpenSSL has been around for ages, there are many different cipher methods. However most are not used, however we must check all of them because you can still encrypt data with them.
A Cipher is a mathematical algorithm to convert data into unreadable binary data.
A Password is key to the box, if you know it you can easily decrypt the data.
Narrowing Down Ciphers
Since there are 190+ cipher methods, we need to narrow it down. So our next step is to look for clues in the encrypted data. There are two major types of ciphers, stream ciphers and block ciphers. Stream ciphers encrypt only the data fed into them, whereas block ciphers will always be a set chunk length.
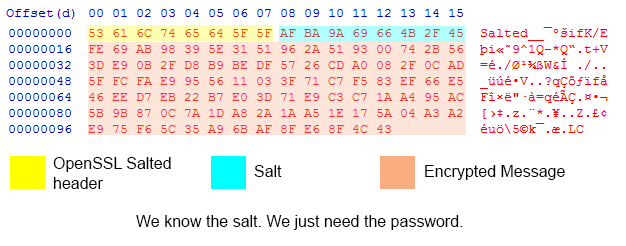
With that knowledge we can use a hex editor to look at the encrypted string:
A byte is roughly a single character, but special characters can take up multiple bytes. We know that OpenSSL Salted Encryption uses the first 8 bytes of the output for Salted__ and the next 8 bytes for the actual salt. The rest of the information is the encrypted message.
The immediately interesting thing here is that the encrypted message data stops 3 bytes short of a full chunk. This is a excellent indicator that the cipher used is a stream cipher (or a block cipher in CTR/OFB/CFB mode). This narrows our cipher list down significantly.
This means that the final string that Blizzard encrypted MUST BE 93 bytes! However some of the stream ciphers aren't 1:1 so it may be shorter.
Where We Are Now
Currently we're using the hivemind to guess passwords with the Gol! Guesser and using advanced bruteforcing methods to try and find the password. We're still far away but this is the most concrete problem Blizzard has given us to solve. Please checkout the Gol! Guesser and the GameDetectives Discord to help us out and contribute!
Thanks This information comes from the GameDetectives Discord and specifically the following people: vmzcg, efco, Epsilon, dovinde, offbeatwitch, catnipp, Wolen