Cyberpunk 2077
| Cyberpunk 2077 | |
|---|---|
| A hacker at E3 2018 exposed a live website linked to upcoming release Cyberpunk 2077. | |
| Type | Official |
| Creator | CD PROJEKT RED |
| Discovered | 2018-06-10 |
Main Page > List of Investigations > Cyberpunk 2077
Cyberpunk 2077 is a story-driven, open world RPG set in a dark future from CD PROJEKT RED (CDPR), creators of The Witcher series of games. As the release of Cyberpunk 2077 drew closer, CDPR began trickling hidden messages and puzzles to the community. The ARG is comprised of these puzzles, and quick solvers are often rewarded with Cyberpunk merchandise.
Contents
2018
E3 Presentation
During Microsoft's E3 2018 presentation slot on June 10th, a "hacker" interrupted the speaker, ultimately revealing a trailer for Cyberpunk 2077. Players immediately noticed some valuable info during the trailer, including GOG codes which were redeemable for games and, most notably, an IP address, 212.91.11.20.
Quadra
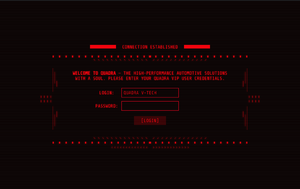
Players quickly realized that the IP resolved to a section of CDPR's Cyberpunk 2077 website, where a password prompt was found along with a welcome message. The message read as follows:
WELCOME TO QUADRA - THE HIGH-PERFORMANCE AUTOMOTIVE SOLUTIONS WITH A SOUL. PLEASE ENTER YOUR QUADRA VIP USER CREDENTIALS.
The login field is force-filled to QUADRA V-TECH, which players connected to a license plate number from the trailer, NC20 CP77, which turned out to be the correct password. Only a very small pool of players were allowed through, and were met with a field to enter their email address. Soon after, the site began to display a message indicating a quota had been reached and that no more emails would be collected.
Quota Met
Suspecting an ARG was building, players rummaged through the site and other related media. A a "secure" subdomain was found, along with a "E3 Schedule" file. RTSP is set up on the site, which players suspected might indicate future intent. Players discovered the site had an SSH server on the same host, which outputs an ASCII-art message. The other output, Permission denied (publickey), indicated a private key was be needed to access the server.
Players also uncovered more potential leads in the trailer, including lines of debug output from OpenSSH, barcodes, PDF417 codes, and several messages (usually on screens in the video), including one which points toward the QUADRA website.
... 10/11/2078 THE FOLLOWING WILL APPLY TO ALL PROFILES ON DATA ALT//0 463.0983.890.3 DOMAIN-PUBLIC RESTRICTION REF. 192.8930.610.10 PUBLIC DATA PRESENTATION WILL TAKE PLACE ON MONDAY AT 12PM GMT+09 ON ALL DOMAINS. SERVER CAPABILITIES ARE ESTIMATED TO SUSTAIN 90% REGISTERED USERS// P2-OS CORPORATION, ALL RIGHTS RESERVED
Developers indicated in multiple messages via Discord that players should wait for more information.
Several users on Reddit who entered the password prior to the quota being met received emails from CDPR in the style of emails from QUADRA automotive, which request logistic and personal information from the player in order to deliver them a care package.
Players who made the QUADRA cutoff received a care package. It contained a CP2077 Quadra styled t-shirt in a QUADRA box. The art on the back of the t-shirt was mysterious, but players found no leads despite heavy analysis.
Trauma Team
On August 22, the ARG sparked up again when CDPR posted concept art on their Twitter. One of the pieces of concept art contained a bit.ly link in the background:
This link led to a first image. Opening that image in a text editor revealed a hidden message, after a long chunk of encoded text, which read Cesar said: oaawz://jku-s-tra.jkwyvqlraylk.jvt/pthnl/zljvuk.qwn. Using a 19 shift ROT, a link to a a second image was revealed. Players connected the phrase TT in the second image to a known CDPR-owned domain, the Trauma Team International website.
Need Insurance?
After accessing the website, players were met with a bot named David asking for an ID in order to talk to him. Further investigation revealed that the numbers from the first image gave the Login ID 0374337573334 for Trauma Team International.
Once logged in, David allowed players to "buy insurance" through Trauma Team. After doing so, each player was given a unique 10 character code, and David prompted these players to use their codes in the My Orders section of the site. After a specific amount of codes were given out, the bot went offline. The code was deciphered using ASCII85 (Z85 (ZeroMQ) variant), giving the ID #ID00000 which was usable in the My Orders section.
Players who made the cutoff were prompted to input their emails. Upon entering their emails, they were greeted with this image, pictured left, informing them that the process would take up to 7 days and thanking them for participating. After a certain amount of codes were used, the My Orders page went offline with the message "Connection failed," concluding this part of the ARG.
Your Life is worth it!
On august 26th 2018, four days after players ripped through the Trauma Team International site, players who got through the cutoff received an email from a Trauma Team International Representative prompting them to reply with their address. The email had two attachments, a PDF and a PNG image. The image was a ciphertext which could be decoded with a grille cipher using the back of the t-shirt as the grille, pictured right. Players concluded that Monday was the most likely solution, and they were proven right when the next clue surfaced on Monday.
Base 64 Stream
On august 27th, CDPR began broadcasting the Base64 encoded text on their Twitch channel. Soon after, they gave a 48 min walkthrough of the gameplay of Cyberpunk 2077.
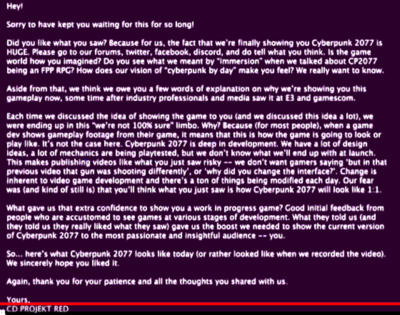
Players captured the video recording during the broadcast and extracted images periodically to gather most of the data. Using OCR (optical character recognition) on each image, and eliminating any duplicate lines, The image was decoded. The image was a screenshot of the beginning of the gameplay demo showing the closed elevator. So far, a difference comparison shows little discrepancy besides the overlay on the top of the frame. The only other thing of note aside from the gameplay itself was a frame hidden by CDPR right after the gameplay, pictured left, which included a few paragraphs explaining the stream and CDPR's motives, thoughts, etc.
2019
E3 Season
While CDPR decided not to hack into anyone's show, shortly after their slotted presentation (which included a breathtaking Keanu appearance), they sent out a tweet which contained binary code translating to:
Seems you're not among the sheep after all. Wanna play a game? Watch for the beeps.
Players determined this to be both an homage to a small easter egg previously hidden on CDPR's site in which a light within the background decor of the site flashed Morse code translating to BEEP, and a possible hint at what is to come ARG-wise. Videos and tweets from this time were scoured for flashing lights or beeping sounds, but to no avail.
Pre-Order Shenanigans
Within days of the tweet hinting to watch for beeps, CDPR updated the CP2077 pre-order page, this time including code which caused the light-blue underscore on the site to again flash in Morse code. Decoded, it read:
33.9899317,-118.47565259999999
These numbers turned out to be the coordinates of a house across the street from CDPR's office in LA. This set players in motion, and before long they had obtained a picture of a QR code (pictured right) taped to CDPR's office door!
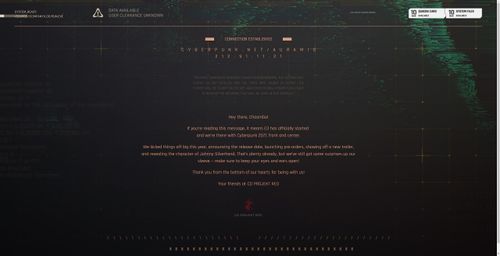
Auramis
The QR code led to a new page on the Cyberpunk.net site titled Auramis, an anagram of Samurai. The page includes a new IP address, 212.91.11.21 (another SSH server), a password-protected RAR file downloadable by clicking the "S" in "CYBERPUNK.NET/AURAMIS", as well as a seemingly cryptic message:
“THE FIRST CORPORATE WAR WAS FOUGHT IN BOARDROOMS, THE SECOND WAS FOUGHT ON BATTLEFIELDS, AND THE THIRD WAS FOUGHT IN SECRET. THE FOURTH WILL BE FOUGHT ON THE NET, AND EVERY GLOBAL POWER IS IN A RACE TO DEVELOP THE WEAPONS THAT WILL BE USED IN THIS CONFLICT.”
Along with these details was a note to players:
Hey there, Choomba! If you’re reading this message, it means E3 has officially started and we’re there with Cyberpunk 2077, front and center. We kicked things off big this year, announcing the release date, launching pre-orders, showing off a new trailer, and revealing the character of Johnny Silverhand. That’s plenty already, but we’ve still got some surprises up our sleeve — make sure to keep your eyes and ears open! Thank you from the bottom of our hearts for being with us! Your friends at CD PROJEKT RED
Players quickly realized the RAR's password was Johnny Silverhand based on his mention in the second message on the page. The RAR file yielded a second password-protected RAR file, along with a text file titled NC.txt, which read:
Things will happen. Plans in motion. Wait for more.
Without a working password for the second RAR, players "waited for more"...
On July 12th 2019, Lilayaah, a staff member from CD PROJEKT RED tweeted this: 3^{eXa.Q9m^._78))3/X6Chd5,(7v~!L"ty"UmxjP6bRm2.wS!(TUMqgyBf6#%&+hm?C88+N'+&{\gL}9}Btzq<P:P=fAXb#Kb~qz{XfD^8+@hv$5Zuz$x< which turned out to be the password for the 2nd RAR file.
Inside this 2nd RAR was a file called 4035 only containing a sequence of numbers:
20-11-16-7-.-24-5-3-10-24-17-22-16
the name of the file 4035 can be converted from octal to decimal which gives us 2077, an obvious reference to the name of the game, Cyberpunk 2077.
By converting each number in the file from octal to decimal we got the following string of numbers:
16-9-14-7-.-20-5-3-8-20-15-18-14
These numbers can then be converted into letters by using the corresponding letter of the alphabet, A = 1, B = 2, C = 3 etc. This gave us the phrase PING.TECHTORN which reshuffled gives us NIGHTCORP.NET, where the next part of the ARG is taking place.
NIGHTCORP.NET
This website's background are all just anagrams of "nightcorp" which look to be taken directly from an online anagram solver without alterations. Even though the edges are blurred, and there are 2 background images -depending on your monitor resolution- nothing of interest was found in the background image.
This website has a "button" that doesn't seem to be working, and in the code it appears to be playing an audio file, however the file is called silence.mp3, and is actually silent. every now and then (see timestamps below) the website plays an actual sound, 13 in total, and they seem to be repeating every 24 hours
The sounds played are in different voices in different languages, and they all appear to be saying one number each.
If we place all the numbers one after another, starting at 00, that makes 0048696368719.
This is a Polish telephone number, which answers your call with slash Uniform slash Charlie Oskar Romeo Papa Tango Hotel India November Golf and then either deletes or saves your message depending on if you made sound or not. (This is normal behaviour of a typical voicemail response system. So we can't input anything on this phonecall.)
This is leading us to the reddit user /u/corpthing (which is an anagram for nightcorp, incidentally). Although the redditer has answered some chat messages on the first day of discovery, none were answered that asked about ARG related stuff. No further chat messages were answered to this day.
The significance of this reddit user account remains unsure for now.
| This page is a work in progress and will be updated as new developments emerge. If you have information you think should be added, please create an account to enable page edits or contact a Wiki Editor. |