Difference between revisions of "Eye Sigil ARG/Clockwork Empires"
| [unchecked revision] | [checked revision] |
(Created page with "== Game == == What we searched so far == - We datamined the game. - Events we tried: -- The Dark Grimoire, both path. -- The Mad Carpenter, all outcome. -- Fish Idol...") |
m (Mattyb moved page Clockwork Empires to Eye Sigil ARG/Clockwork Empires) |
||
| (6 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | = | + | {{ArgHeader|arg=Eye Sigil ARG}} |
| + | [[Image:Ce 2015 sep promo illustration small.jpg|thumb|The terrible secret of whatever is on that table]] | ||
| + | '''Clockwork Empires''' is an early access colony sim game by ''[https://www.gaslampgames.com/ Gaslamp Games]''. | ||
| + | Being in early access, it updates pretty much every month. The update with the sigil was for September 2015, version 43 of the game, dubbed ''The Terrible Truth''. The update blogpost was posted 16 Sep 2015. | ||
| + | =Sigil= | ||
| + | Sigil is located on the promotional art for the version 43 update, [https://www.gaslampgames.com/2015/09/16/clockwork-empires-september-update-the-terrible-truth/ available here]. | ||
| + | It wasn't added into the game on update 43, but in later versions it does appear in-game in a simplified form (no fishbro, no girl with an axe) as the art for various events — the file called <code>eldritch_tinkering.png</code> in the game's resources. | ||
| + | The list of events that the image illustrates was changed with updates too. | ||
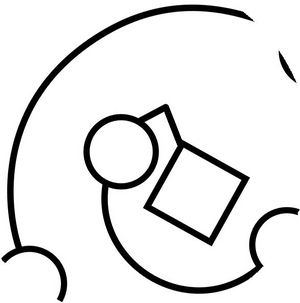
| + | [[Image:ClockworkSigil.png|300px]] | ||
| + | =Piece= | ||
| + | The puzzle piece is hidden in the promotional image itself with [http://www.openstego.com/ OpenStego] steganography software, using the randomLSB algorithm (which is the default) and the password 191761112. The piece was first extracted by Discord user ecstaticeggplant. | ||
| − | + | To find the password, the player has to recognise the symbols on the stone on the right of the sigil in the image. They are actually the first word of the [[Wikipedia:Phaistos Disc|Phaistos Disc]], as discovered by [https://www.reddit.com/u/zarawesome /u/zarawesome]. The password is composed of the amounts of times these symbols appear on the disc in order (19, 17, 6, 11 and 12). | |
| + | The piece is also hidden with the same software in the eldritch_tinkering.png file too. | ||
| + | |||
| + | OpenStego encodes the filename along with the data itself, in this case it was '''gaslamp_map_piece.jpg'''. | ||
| + | |||
| + | [[Image:CEPiece.jpg|300px]] | ||
| + | |||
| + | ==Discovery process notes== | ||
| + | Steganography tools were tried as early as the first discovery of the sigil, but to no avail. Usually you cannot extract the data unless you know exactly which tool was used to hide it, since there are many possible algorithms to pick pixels to modify [[Wikipedia:least significant bit|LSB]]s and methods of encryption of the hidden data. However, an important progress to make sure that steganography was used and to pinpoint the tool was finding out that the promo image was uploaded in two versions. | ||
| + | |||
| + | There was a JPEG uploaded on 14 Sep 2015 and the PNG (which is used in the post) on 16 Sep 2015. As study by Discord users Crauss and DukeBG has shown, these images differ only in the LSBs. That blogpost is also the only one that actully uses PNGs for the art, every other one just uses JPEGs. | ||
| + | |||
| + | The changed LSBs also were scattered randomly on the image as opposed to being changed one by one in rows starting from the top or the bottom of the image, as many stegano tools do. This let to believe that OpenStego that has the randomLSB algorithm is the one. | ||
| + | |||
| + | The developer later revealed (through their community manager Daynab) in GameDetectives Discord that they've chosen OpenStego as the first link in google for "steganography software". | ||
| + | |||
| + | =False leads= | ||
- We datamined the game. | - We datamined the game. | ||
| − | - Events we tried: | + | |
| − | + | - Events we tried: | |
| − | + | * The Dark Grimoire, both path. | |
| − | + | * The Mad Carpenter, all outcome. | |
| − | + | * Fish Idol | |
| − | + | * Airship Crash | |
| − | + | * Dream Spectres | |
| − | + | * Quaggaroth | |
| − | + | * Creepy Night | |
| − | + | * Mysterious Ore | |
| − | + | * Singing Grass | |
| − | + | * Eerie Spectres | |
| − | + | * Fishpeople stuff | |
Latest revision as of 17:54, 29 September 2021
Clockwork Empires is an early access colony sim game by Gaslamp Games.
Being in early access, it updates pretty much every month. The update with the sigil was for September 2015, version 43 of the game, dubbed The Terrible Truth. The update blogpost was posted 16 Sep 2015.
Sigil
Sigil is located on the promotional art for the version 43 update, available here.
It wasn't added into the game on update 43, but in later versions it does appear in-game in a simplified form (no fishbro, no girl with an axe) as the art for various events — the file called eldritch_tinkering.png in the game's resources.
The list of events that the image illustrates was changed with updates too.
Piece
The puzzle piece is hidden in the promotional image itself with OpenStego steganography software, using the randomLSB algorithm (which is the default) and the password 191761112. The piece was first extracted by Discord user ecstaticeggplant.
To find the password, the player has to recognise the symbols on the stone on the right of the sigil in the image. They are actually the first word of the Phaistos Disc, as discovered by /u/zarawesome. The password is composed of the amounts of times these symbols appear on the disc in order (19, 17, 6, 11 and 12).
The piece is also hidden with the same software in the eldritch_tinkering.png file too.
OpenStego encodes the filename along with the data itself, in this case it was gaslamp_map_piece.jpg.
Discovery process notes
Steganography tools were tried as early as the first discovery of the sigil, but to no avail. Usually you cannot extract the data unless you know exactly which tool was used to hide it, since there are many possible algorithms to pick pixels to modify LSBs and methods of encryption of the hidden data. However, an important progress to make sure that steganography was used and to pinpoint the tool was finding out that the promo image was uploaded in two versions.
There was a JPEG uploaded on 14 Sep 2015 and the PNG (which is used in the post) on 16 Sep 2015. As study by Discord users Crauss and DukeBG has shown, these images differ only in the LSBs. That blogpost is also the only one that actully uses PNGs for the art, every other one just uses JPEGs.
The changed LSBs also were scattered randomly on the image as opposed to being changed one by one in rows starting from the top or the bottom of the image, as many stegano tools do. This let to believe that OpenStego that has the randomLSB algorithm is the one.
The developer later revealed (through their community manager Daynab) in GameDetectives Discord that they've chosen OpenStego as the first link in google for "steganography software".
False leads
- We datamined the game.
- Events we tried:
- The Dark Grimoire, both path.
- The Mad Carpenter, all outcome.
- Fish Idol
- Airship Crash
- Dream Spectres
- Quaggaroth
- Creepy Night
- Mysterious Ore
- Singing Grass
- Eerie Spectres
- Fishpeople stuff