Difference between revisions of "Waking Titan/Phase 4"
(updated with recent events) |
|||
| Line 255: | Line 255: | ||
https://bit.ly/2pLmadg | https://bit.ly/2pLmadg | ||
</pre> | </pre> | ||
| − | + | [[File:Sean-tweet.png|thumb|right]] | |
The shortened link redirected to a tweet from Sean Murray, which said <code> The cause is hidden. The effect is visible to all. #oneonebst </code> | The shortened link redirected to a tweet from Sean Murray, which said <code> The cause is hidden. The effect is visible to all. #oneonebst </code> | ||
Revision as of 22:32, 28 March 2018
| Waking Titan - Phase 4 | |
|---|---|
| Waking Titan was an ARG which led to the Atlas Rises update for No Man's Sky, and has been dormant untill 18-12-2017. | |
| Type | [[List_of_Investigations#Official|Official]] |
| Creator | Alice & Smith & Hello Games |
| Discovered | 2017-05-28 |
Main Page > List of Investigations > Waking Titan > Phase 4
Contents
It is unclear whether Phase IV has officially begun, or whether these events are interstitial matter leading to a new phase. For our purposes we refer to these events as "Phase IV" until contrary evidence is presented.
Tenth Glyph
Beginning on December 28th, 2017, typing WHOIS on the Waking Titan website returned the following: #WHATIS1.5. In addition, the 10th glyph was made active, and linked to a Google Drive folder, which contained community-made pictures of the NMS logo in an infinite mirror.
The titles of the photos, when strung together (skipping the 00 (empty) ones), formed the hexadecimal code for moirrr, which was an anagram for mirror. Additionally, the hexadecimal code in the correct order for the word mirror could be found on the bottom of the Myriad website.
Also of note was the background of the tenth glyph, which read:
Dear Elizabeth We have finished processing 10,000 passes as per your requirements. You should have them in time for the next phase. I really hope you will like the final product. Kind regards, Gail
The allusion to 10,000 passes is likely a reference to the Level 4 Atlas passes that were promised to players as part of earlier phases. The identity of "Gail" remained unknown.
Atlas Passes
On January 17th, 2018, the first CSD user received their Atlas Pass. The passes were made from cardstock, with a textured pass printed on it. The front had the text WAKING TITAN printed, and below that the CSD category the user belonged in. On the very bottom, a series of hexadecimals reading 70686f656e6978 could be found, which, after decoding, translated to PHOENIX. On the back, the owner's CSD-ID was written, along with a serial number stating which pass out of 10,000 the user had, and a number at the top.
It is strongly recommended to not cover up the hex underneath your signature, and to share the number above and below your CSD ID if you are in possession of a pass. Preferably with a picture of the front, as shown below. For a list of all the atlas passes currently known of, please refer to this spreadsheet. In the event you receive one of these, please share a picture of the front, and the numbers underneath and above your CSD-ID (censored bit) on the back.
Status Command Update
On January 20th at 5:44PM UTC, the output of the STATUS command began to update:
Downloading Data...: 19:44 1- : 20:16 (32 min) 1-8 : 20:27 (11 min) 1-80 : 20:39 (12 min) 1-800- : 20:44 (5 min) 1-800-41 : 21:35 (51 min) 1-800-413-01 : 22:14 (39 min) Xxxxx X : New Line 1-800-413-011 : 22:15 (1 min) Xxxxx XX 1-800-413-0110 : 22:16 (1 min) Xxxxx XXX
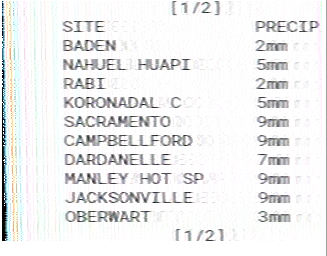
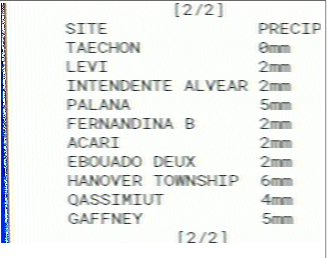
Calling the provided phone number yielded an SSTV transmission (pictured below) which, once decoded, provided meteorological data for various locations.
Players found they were to order the list of locations in the image alphabetically. This yielded a sequence where Index by Precipitation could be read off.
Using the ordered text indexed by precipitation (in alma the second index is o) led to the following:
CAFE BENE NINETEEN SAT
Livedrop Memo
The text indicated a new livedrop would be occurring in the same location as the last one had. However, due to the old Cafe Bene closing, the Xxxxx XXX part was added in the STATUS command update to warn players about the new venue, Outro NYC, which opened in the same place as the Cafe Bene had been located. The livedrop was intended to occur at 7PM EST (12:00AM UTC). However, the first player from the community who set out for the drop was involved in a traffic mishap, delaying their arrival. Anticipating missing the drop's time window, the community reached out to request a time extension, and the STATUS command, which had updated frequently throughout the confusion, was updated again to approve the community's request.
STAND BY: CSD CITIZEN NOT DETECTED WARNING: CSD CITIZEN NOT DETECTED! IT'S LONELY OUT HERE TIME EXTENSION REQUESTED? EXTENTION PROPOSED: 2H30 – AWAITING CSD APPROVAL EXTENSION APPROVED, BE SAFE
After the extension was approved, a second player from the community set out to the livedrop location on livestream and met with their A&S contact around 7:30PM EST (12:30AM UTC). During the meeting, the player was handed a memo from a mysterious case disguised as a book, pictured left. After some cryptic conversation, the contact asked if they were "getting enough sleep", stating that being well-rested would be very important. After the meeting, players who had attended the livedrop met in another location and showed off the memo, speculating about it's contents and even discovering the REM Sleep connection to the letters on the memo's back. After the livedrop, the community used the livestream to look over the memo, pictured below. On the back of the memo REMS is written. This clue, in combination with the strange question A&S asked at the rendezvous, led players to the password for the 10th Glyph, REM SLEEP.

Once the glyph was solved, the STATUS command updated to a bit.ly link to a form. Players discovered that on the sixth question on the form, entering REMS or REM Sleep (case sensitive) caused a seventh question, pictured right, to reveal itself, allowing CSD users to enter their email address to receive "left over materials" from something called Lab 319. Players remained unclear on what exactly Lab 319 was or what it's leftovers were, however signing up seemed integral given the input is only revealed after using the REM Sleep phrase.
Solar Event
On 26 March, 2018 at 05:25 UTC an event occurred. The Myriad site came online featuring indications of a solar event interfering with operations. In addition, the status command on Waking Titan briefly displayed the following:
CODE -3 Unable to restart ................. ERROR LOG SUMMARY - Major malfunction - Protect the monarch - All tiers 2 and tiers 3 clients must be purged IMMEDIATELY ................. TO ALL CSD - Gather maximum EXTERNAL intel - CSD should take time to regroup and get organized
Ten minutes elapsed before the Status command began to display the following:
CODE -5 System Locked e b 4 c 1 4 a 9 c 6 2 2 d f 7 1 6 6 f b e 0 d d 8 9 1 5 d b 0 2
This hexadecimal string was used to reference a connection the private key for an Ethereum cryptocurrency wallet related to an ostensibly "promotional" event for an upcoming product from V/RE.
Client 3597b
At 1:11 AM, UTC, Myriad-70.com updated, and the updates included the following.
Latest network diagnostic table: - Network corruption detected - Situation isolated to Client 3597b - Process cannot be suspended due to critical conditions -------------------------- -Beijing: 29.1Tb/s -------------------------- MAJOR ISSUES: Client 3597b
Soon after, at 1:30 AM UTC, the Status command updated in the Terminal to say the following.
> status CODE -5 System Locked e b 4 c 1 4 a 9 c 6 2 2 d f 7 1 6 6 f b e 0 d d 8 9 1 5 d b 0 2 -------------- Monarch Repository Status: Degraded Conflict With - Client 18d1a TRACERT 10.30.74.* - Client 3597b TRACERT 54.91.155.* - Client 351h TRACERT 6.128.214.* - Client 0911a TRACERT 74.1.21.*
Approximately 15 minutes later, clients began to disconnect, beginning with Client 0911a, second being Client 18d1a, and the last being Client 351h, who had an additional piece of text added, being ID: 79657321, which was translated as hex into Yes!
Then, at 2:15 AM UTC, the status command was updated again, stating - Client 3597b - UNABLE TO DISCONNECT 54.91.155.209 NAT 52.2.248.*
At 1:38 PM UTC, the status command updated once again, stating - Client 3597b - UNABLE TO DISCONNECT 54.91.155.209 NAT 52.2.248.*:80\\
Ware-tech.cloud
Of the sites found in the 52.2.248 range, 52.2.248.6 was found. Using the metadata found in the HTML and searching on Google, the domain and Twitter were located as well. The site is in Chinese, although Google Translate gives a good, readable translation.
On Twitter, under the Shipping Soon image, is a Hex string 77 61 6E 74 20 74 6F 20 6B 6E 6F 77 20 6D 6F 72 65 that, when converted to ascii reads want to know more. Under the #waretech hashtag on Twitter, there are three images shared by "Partner Companies" with the following code (and the ascii conversion):
62 69 74 2E = bit. 6C 79 2F 77 = ly/w 61 72 65 32 = are2
On the ware-tech website, if you subscribe, you receive an email with another 3 characters: 30 31 38, which again in Ascii becomes 018. Together this gave a bit.ly link that leads to the W/are Discord channel.
On Discord, we were informed of a community puzzle that was going on by the admin. Members of the W/ARE Discord had received tweets from another account, https://twitter.com/w9rPQ45E, which had seven tweets with hex code in them:
01 [ 74 78 2f 30 78 66 65 30 31 35 30 66 ] 02 [ 62 33 30 32 61 38 62 36 64 34 30 38 ] 03 [ 35 37 32 32 64 61 61 31 64 30 37 37 35 ] 04 [ 38 33 31 38 35 30 38 36 39 31 30 61 31 ] 05 [ 61 38 32 34 38 63 65 32 34 38 30 64 ] 06 [ 32 65 33 38 37 33 31 ] 07 - Signal Lost [ 65 6e 64 20 6f 66 20 6c 69 6e 65 ]
Translated into Ascii, these tweets give the following:
tx/0xfe0150f b302a8b6d408 5722daa1d0775 83185086910a1 a8248ce2480d 2e38731
which references this Ethereum transaction. The Twitter username, w9rPQ45E is also a Pastebin, providing the string edb044c81d40a196c4672a2bd6f17f1f6. In the Ethereum transaction, there is Input Data that, when converted to ascii, links to another Pastebin, providing another string: b67fbb5e90ddcda8a921656d0b30a20
Two things have been done with these strings. Together, they are the Private Key for the Ethereum account the money was transferred to. It has since been withdrawn to a different account. Second, if you put the two strings together and compare them with the string from Waking Titan's console, every odd character matches the strings from Pastebin.
edb044c81d40a196c4672a2bd6f17f1f6b67fbb5e90ddcda8a921656d0b30a20
e b 4 c 1 4 a 9 c 6 2 2 d f 7 1 6 6 f b e 0 d d 8 9 1 5 d b 0 2
The remaining characters are d0 48 d0 16 47 ab 61 ff b7 b5 9d ca a2 66 03 a0, however if this has any use is yet to be seen.
Three hours after the W/ARE Discord Admin let the community know about the puzzle, at 6:01 PM UTC they returned and said
That was it for today, good job on solving our community puzzle! You are good! :smiley: Tomorrow one of our partners will have a giveaway for us! We will have more for you this weekend also!
Mercury Project
At 9:26 PM UTC, the Mercury command updated to say the following.
Mercury process > Build XXXX Ready to load branch version 1.5 Send Password Code in HEX to : Telegram MercuryHG80
This puzzle required a user to solve the riddle shown below, convert the answer into hexdecimal, and send it to an official Telegram account run by one of the Puppet Masters.
The puzzle was as follows: “Descended from Night, I share the blood of nightmares. Look forward to the gates of horn and ivory”
This puzzle was solved by searching "The gates of horn and ivory", which resulted in dreams and nightmares of Greek mythology. After noting the capital N in "nightmares", users found the Greek god of night, Nyx, which led to one of her children, Morpheus, who was one of the Oneiroi, and the god of dreams. The name was then converted to hexdecimal and sent to the Telegram account, and the terminal accepted the password, resulting in the following command update.
Processing "Morpheus" > ACCESS GRANTED Downloading.......
Then, at 9:54 UTC, the Mercury command updated again, and said the following.
<Mercury process > Build XXXX Ready to load branch version 1.5 Send Password Code in HEX to : Telegram MercuryHG80 -------------------------------- Process started by community - ETA 11:00 BST https://bit.ly/2pLmadg
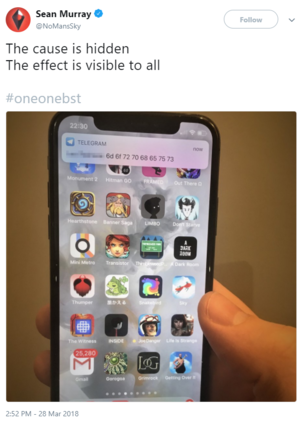
The shortened link redirected to a tweet from Sean Murray, which said The cause is hidden. The effect is visible to all. #oneonebst
The tweet also included a photo of someone, presumably Sean himself, holding a phone receiving a Telegram notification, which was Morpheus in hexdecimal. The hashtag spells out 11BST, or more precisely, 11:00 BST, or, 10:00 UTC. No updates were made at 10:00 PM, and was then confirmed to be counting to 10:00 AM.
This page is a work in progress, and will be updated as new developments emerge.