Difference between revisions of "TidalVortex"
| [unchecked revision] | [unchecked revision] |
(Removed Zaelong's addition.) |
|||
| Line 37: | Line 37: | ||
At approximately 1AM UTC on December 21st, the in-game situation room updated to show what looks like a nebula on one of the screens. When clicked on, it opens up [https://clyp.it/1ialhctq?token=25962f8e988d867853af6ea7a7c79dab this link to Signal Intercept Attempt #2 uploaded by Dispatch.] As of now, it hasn't been solved yet. Even though this is a different signal to the first one, both seem to be connected. | At approximately 1AM UTC on December 21st, the in-game situation room updated to show what looks like a nebula on one of the screens. When clicked on, it opens up [https://clyp.it/1ialhctq?token=25962f8e988d867853af6ea7a7c79dab this link to Signal Intercept Attempt #2 uploaded by Dispatch.] As of now, it hasn't been solved yet. Even though this is a different signal to the first one, both seem to be connected. | ||
| + | |||
| + | |||
| + | At 17:55 UTC, an agent emailed Dispatch explaining how the used cipher operated, and afterwards, a message from Dispatch was received publicly on Discord which read the following. | ||
| + | |||
| + | <pre> | ||
| + | |||
| + | Dispatch: | ||
| + | |||
| + | Someone has cracked the signal: | ||
| + | The noise from the signal is ordered like this: | ||
| + | 000000 111111 000000 001110 110001 011001 010010 100110 | ||
| + | |||
| + | By taking the nth bit from these sequences we can rearrange the bits to this: | ||
| + | 01001001 01001110 01010100 01010001 01010011 01001100 | ||
| + | |||
| + | Which than can be converted to ascii: writing: | ||
| + | INTQSL | ||
| + | |||
| + | In other words: | ||
| + | By starting at the 000000 111111 000000 part of the sequence, we can transform the message to Q codes used in radiocommunication. | ||
| + | |||
| + | </pre> | ||
| + | |||
| + | Soon after, a follow up message was received, stating <code> We should have a clearer version of the first signal for you shortly, as well. </code> | ||
| + | |||
| + | |||
''As of now, this is all that is known. This page will continue to be updated as more of the event plays out.'' | ''As of now, this is all that is known. This page will continue to be updated as more of the event plays out.'' | ||
Revision as of 18:27, 21 December 2017
| Operation TidalVortex | |
|---|---|
| Live event 14 of The Black Watchmen, involving the long lost mysterious figure Whitechapel. | |
| Type | [[List_of_Investigations#Official|Official]] |
| Creator | Alice & Smith |
| Discovered | 2017-12-19 |
Main Page > List of Investigations > TidalVortex
On December 15th, 2017, Alice & Smith released the Whitechapel DLC for The Black Watchmen, a PARG (Permanent Alternate Reality Game). 4 days after the release, a live event began, known as Operation TidalVortex.
The mission began as the situation room previewed a Dagaz rune, and the event was officially classified as live.
Contents
Briefing
On December 19th, 2017, at approximately 1:54AM UTC, a briefing email was sent out to all Black Watchmen agents. This email contained a classified document from site 7361, which proves that Mr. Whitechapel is behind the mysterious occurrences in New England. The email also contained the following instructions:
- Take your cell phone and go to map.blackwatchmen.com
- Record yourself reading the following incantation:
A custodia matutina usque ad noctem
- The Situation Room will broadcast a symbol in real-time, draw it on your cellphone to submit your voice recording.
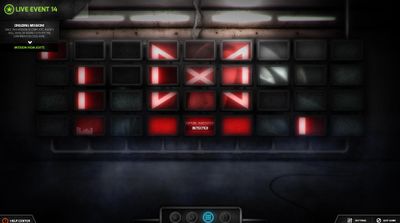
On December 20th, at approximately 1:50AM UTC this intercepted broadcast was found in the in-game situation room.
After agents received the briefing, the Black Watchmen Map along with the in game map began to fill up with symbols indicating an agent in that area had recorded and submitted their chant. Soon after these symbols appeared, audio cues of agents chanting began to play, each audio cue being repeated after ending.At approximately 1AM UTC on December 21st, the in-game situation room updated to show what looks like a nebula on one of the screens. When clicked on, it opens up this link to Signal Intercept Attempt #2 uploaded by Dispatch. As of now, it hasn't been solved yet. Even though this is a different signal to the first one, both seem to be connected.
At 17:55 UTC, an agent emailed Dispatch explaining how the used cipher operated, and afterwards, a message from Dispatch was received publicly on Discord which read the following.
Dispatch: Someone has cracked the signal: The noise from the signal is ordered like this: 000000 111111 000000 001110 110001 011001 010010 100110 By taking the nth bit from these sequences we can rearrange the bits to this: 01001001 01001110 01010100 01010001 01010011 01001100 Which than can be converted to ascii: writing: INTQSL In other words: By starting at the 000000 111111 000000 part of the sequence, we can transform the message to Q codes used in radiocommunication.
Soon after, a follow up message was received, stating We should have a clearer version of the first signal for you shortly, as well.
As of now, this is all that is known. This page will continue to be updated as more of the event plays out.